As part of IronNet’s Network Detection and Response (NDR) capabilities, we are committed to helping our customers pivot from threat detection to response quickly and seamlessly within their SOC’s existing security stack.
Here’s how we do it: First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on the alert fatigue most SOC analysts are experiencing. Finally, we take a Collective Defense approach to threat sharing in real time so SOC analysts across companies can answer the common question: “Are you seeing what we’re seeing?”
With IronNet’s correlated threat knowledge and SOAR integrations, SOC analysts can respond faster to threats within their existing SOAR platform. For example, see how our IronDefense detection platform integrates with Splunk Phantom.
Now, let’s take a closer look at recent threats affecting the cyber world:
The July IronLens from the IronNet CyOC
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. Analysts in the IronNet Cyber Operations Center (CyOC) review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered and correlated across the IronDome communities in June:
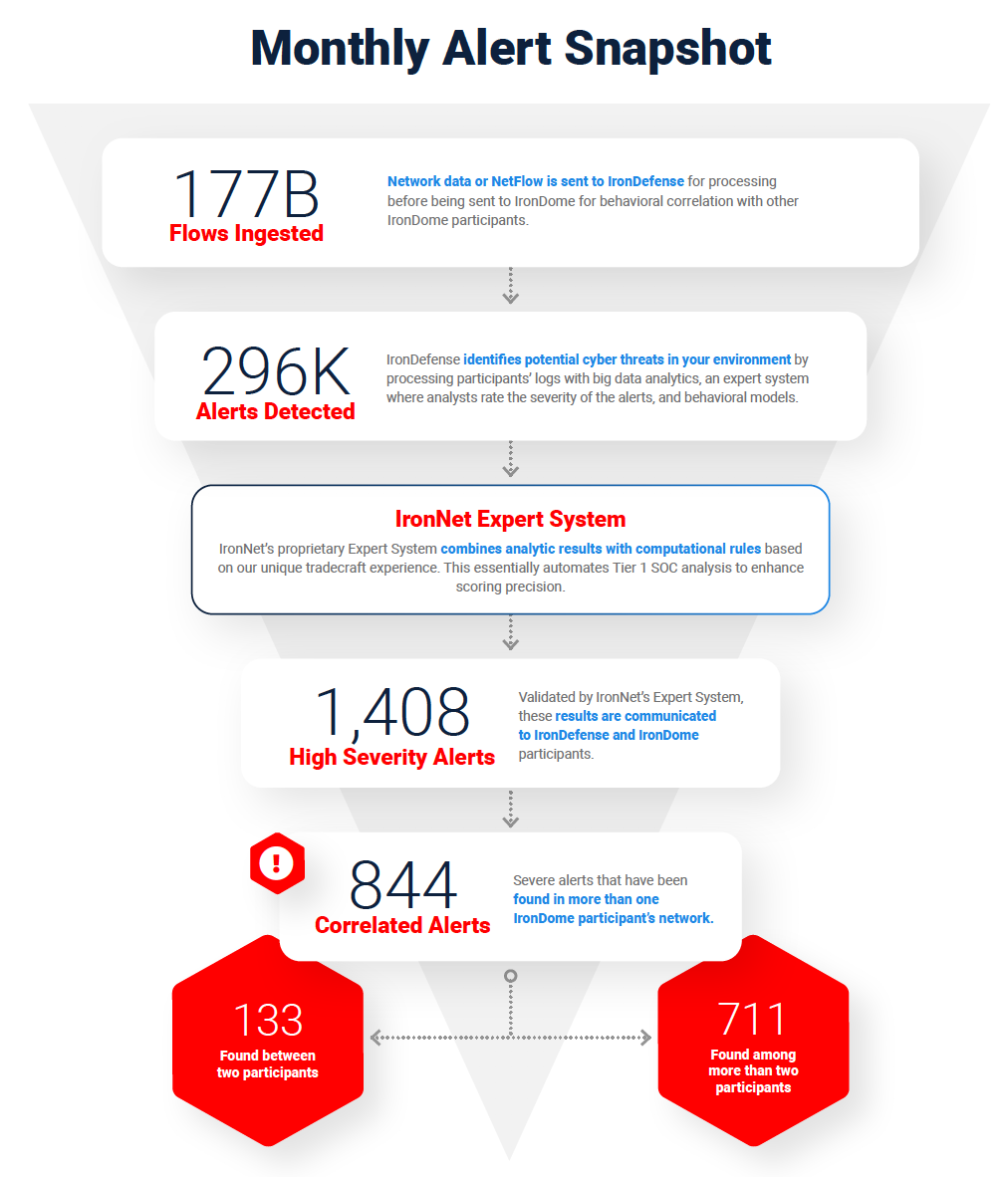
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 371 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. Some recent malicious IoCs include a phishing site targeting users’ Microsoft Office credentials and a domain appearing to be hosting active PayPal phishing sites.
These IoCs are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the July IronLens Report for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In June, we created 8,739 threat intel rules, including rules related to CryCryptor ransomware posing as a Canadian COVID-19 tracing app for Android, as well as rules for the Sodinokibi ransomware campaign designed to identify credit card or point-of-sale software on victim networks. You can see more in the full July IronLens CyOC Report.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
Focus on Maze ransomware
The IronNet CyOC continues to track industry threats to strengthen cybersecurity resilience across industries. For example, we are tracking threats by the group behind Maze ransomware, which has continued its steady pace of successfully infiltrating and encrypting files within various enterprise networks. Since April 2020, Maze ransomware has managed to infect several high-profile companies such as Cognizant, the insurance provider Chubb, and Conduent (an IT services company). Maze is not necessarily a single group of threat actors; the name refers to multiple attack campaigns that extort targeted organizations on the basis of threat of ransomware and possible public disclosure of private data if ransom demands are not met. You can read in this “Navigating Maze ransomware” blog more about how to unravel the TTPs of this high-profile ransomware and how IronNet behavioral analytics can detect it. You can see the latest industry news in the full report and in IronNet News.
That’s a wrap from the CyOC. See you next month.
Access the July IronLens Report.

.png)

