
Credit: Puzzle photo by Ryoji Iwata on Unsplash
SOC managers must weigh utility versus convenience when deciding whether to add a new tool to their cybersecurity ecosystem. Sure, the tool would be useful, but is it worth your time and cost to integrate it with your technology stack? And is integration seamless and easy?
IronNet positions its products in a way that preserves the workflow of our customers’ SOC. IronDefense is a Network Detection & Response (NDR) solution that delivers scalable network behavioral analytics, integrated packet-level cyber hunt, and the application of tradecraft expertise to the detection of advanced threats. The IronDefense App for Splunk allows IronNet customers to stream detections from IronDefense's IronAPI into their own Splunk instance. In this way, security operation teams can leverage the power of IronDefense behavioral detection and benefit from broader threat visibility, sharing, and collaboration in our IronDome Collective Defense platform. These integrations enable SOC teams to start with their existing workflow in Splunk and pivot seamlessly, as needed, to the IronDefense UI for advanced investigation and cyber hunt.
.png?width=3788&name=Splunk1%20Screen%20Shot%202020-05-18%20(1).png) IronDefense dashboard in Splunk
IronDefense dashboard in Splunk
How does IronDefense work?
IronDefense provides machine-speed detection at scale to identify advanced threats that are often missed by existing commercial cybersecurity solutions. Leveraging machine learning and analysis by IronNet analysts, IronDefense sees “unknown unknowns” based on network behavior, including lateral movement, DNS tunneling, and beaconing.
IronDefense works closely with our Collective Defense solution IronDome to deliver unprecedented industry-level threat awareness and insights to help members identify threats that would be difficult to identify by a single enterprise.
IronDefense App for Splunk
The IronDefense App for Splunk enables customers to see anomalous network activity detected by IronDefense and enriched by IronDome using the Splunk interface. The app is also integrated to allow customers to report their assessments of IronDefense discoveries, enabling Collective Defense and analytic improvements by the IronNet team.
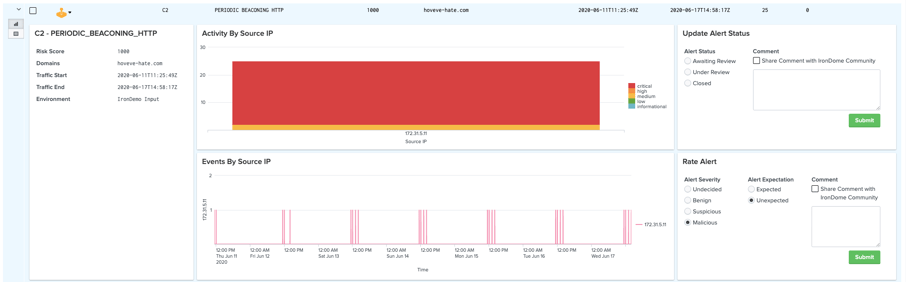
Anomalous network activity detected by IronDefense and enriched by IronDome using the Splunk interface
IronDefense App for Splunk offers five key features:
- Seamless integration with IronVue: Each IronDefense detection includes a unique URL that enables security teams to quickly pivot into IronVue – IronDefense’s user interface – for deep-dive investigation including PCAP retrieval and triage of detected anomalies.
- Collective Defense: Integration of the IronDefense App for Splunk with IronDefense’s IronAPI allows IronNet customers who subscribe to IronDome to send their analysis of IronDefense detections to IronDome, enabling a proactive, collaborative approach to cybersecurity.
- Customizable dashboard: Splunk users can use the IronDefense App to customize reports and dashboards of the results from their IronDefense solution. The app comes with a default dashboard that aggregates key threat detection metrics into a summary view for reporting purposes.
- Custom reports: IronDefense detections include data that does not map to the Splunk Alert Common Information Model (CIM). This additional data is available for custom report generation within the Splunk interface through building custom queries.
- Hunt: IronDefense's IronAPI shares detections with the IronDefense App for Splunk to enable indexing. The indexed detections are available for hunting within Splunk's search page. This permits discovery of IronDefense detections during exploratory hunt operations.
IronNet's 2020.9.0 release includes an update to the IronDefense App for Splunk. This integration improvement between IronNet and Splunk eliminates complexity as it reduces the number of APIs leveraged (from OpenAPI and IronAPI to just IronAPI). Additionally, the integration will expose more metadata about IronNet detections in the form of event context and extensive IronDome correlation information. Both of these additions will be available for users within the application in an on-demand fashion to eliminate ingest costs for Splunk. New displays for event context and IronDome correlation information will be available within the table of alerts on the IronDefense dashboard.
The IronDefense App for Splunk Phantom
IronDefense App for Splunk Phantom enables customers to seamlessly apply their threat response playbooks to events detected by IronDefense. This particular integration enables security teams to manage alerts more efficiently by integrating teams, processes, and tools together through the automation of tasks and orchestration of workflows. Data ingestion from IronDefense allows users to capitalize on Phantom’s ability to automate security actions through playbooks and rapidly triage IronDefense events and alerts in an automated, semi-automated, or manual fashion. Users also can utilize Phantom’s mission control feature to access IronDefense events, alerts, and IronDome community activity for investigation, decision, and action.
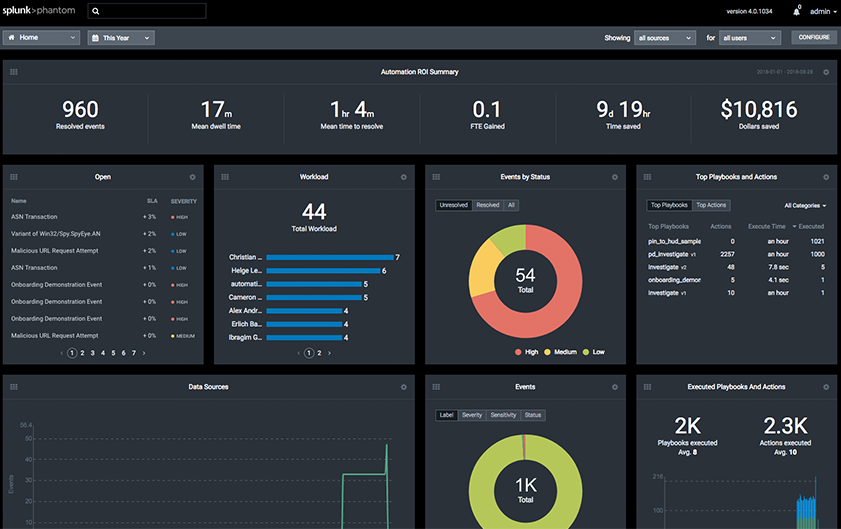
IronDefense integration in Splunk Phantom dashboard
Getting started
Ready to bring the power of IronDefense to Splunk? Existing IronNet customers who have deployed IronDefense can download the IronDefense App for Splunk by visiting Splunkbase.
Learn more in the IronDefense App for Splunk solution sheet and the IronDefense App for Phantom solution sheet.
.png)
