Maze is not necessarily a single group of threat actors; the actually name refers to multiple attack campaigns that extort targeted organizations on the basis of threat of ransomware and possible public disclosure of private data if ransom demands are not met.
Maze-themed attacks have been ongoing since May 2019 and have targeted organizations across different sectors and geographies. While a substantial number of targets are located in the Americas and Europe, recent evidence suggests the attackers are also actively targeting organizations in APAC and EMEA.
The ransomware payload was directly delivered and executed on victim machines via email phishing campaigns and exploit kits after users were lured to visit compromised sites hosting the exploit kits. The tactics have now evolved such that the ransomware payloads are executed in later stages of the attack with the initial stages focused on obtaining a foothold on the network, moving laterally and exploiting additional systems, exfiltrating data from victim machines and finally executing the ransomware payload. The penultimate step of exfiltrating data from victim machines is key because it allows the MAZE actor to further extort money from its victims if its initial ransomware related demands are not met.
IronNet proves to be a very capable network detection and response (NDR) platform that is able to track and trace a Maze campaign as it progresses along its kill chain in the victim organization. As it precipitates various alerts associated with the attacker’s malicious activities, they represent multiple opportunities for the organization to provide a swift and effective response to neutralize the threat.
In the following, we will unravel the tactics, techniques and procedures (TTPs) of Maze and the associated detections on the IronNet NDR platform, IronDefense.
Behavioral detection of “unknown unknown” threats
IronNet was founded by General (Ret.) Keith Alexander — former head of the U.S. National Security Agency and founding Commander U.S. Cyber Command — to defend companies, organizations, sectors, and nations against highly organized cyber adversaries and sophisticated attacks. The IronNet NDR platform, IronDefense, strengthens an organization’s cybersecurity defense posture and resilience against highly sophisticated adversaries, across borders and sectors.
Furthermore, IronNet’s unique platform for Collective Defense, IronDome, delivers the power and resources of Collective Defense so that any company, organization, or public entity can defend more effectively as part of a collaborative ecosystem with shared knowledge and vetted alerts in real time.
Instead of relying solely on static rules, signatures, or static indicators of compromise (IoCs), IronNet’s NDR adds sophisticated AI and machine learning algorithms to detect the elusive unknown unknown threats based on detection of malicious behavior on the network. The graphic below illustrates the differences between these unknown unknown threats and other categories of (relatively) easily identifiable threats.
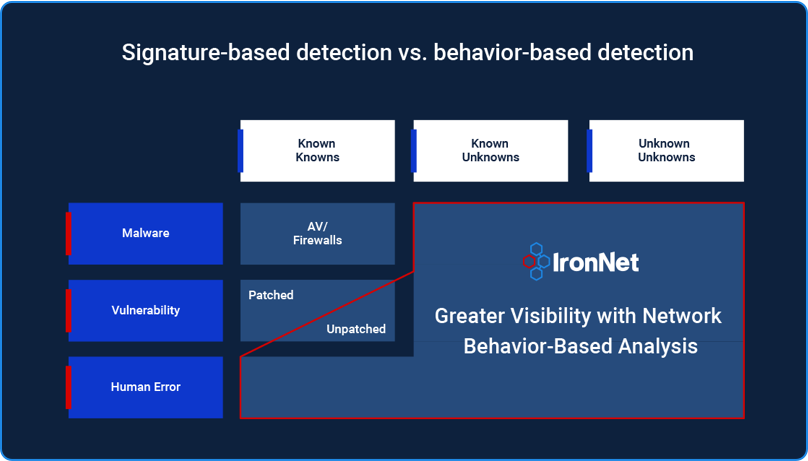
Figure 1: Detection of unknown unknown threats using behavioral detection at the network level
Furthermore, IronNet does not need to be presented with decrypted traffic, as its analytics are designed to operate on encrypted traffic.
Given that in a typical enterprise, approximately 75 percent of the traffic is likely encrypted and organizations typically can’t and do not want to decrypt traffic, the ability to detect malicious behavior in encrypted traffic, by design, puts IronNet in a position of immense advantage over some of its competitors.
As a result, IronNet is resilient to an adversary’s attempts to:
- make use of legitimate rather than outright malicious tools and techniques (so-called “living off the land”)
- periodically change its C2 infrastructure (IP addresses and domain names associated with the malware’s controller)
- apply advanced evasion and bypass tactics to defeat endpoint-based controls such as NGAV and EDR
- hide activity on the endpoints using Rootkits
- periodically modify characteristics of its C2 network traffic profile (e.g. beacon frequency, introduce jitter, traffic protocol)
- use encryption to hide much of what is transmitted on the wire.
Specifically, in the case of Maze ransomware attacks, Maze operators have been observed to use most of the aforementioned tactics and techniques to avoid detection on the endpoints they infect.
However, despite these attempts by the adversary to avoid detection on the endpoints, this activity is still expected to generate network traffic activity (as a result of the need to maintain a communication link between the adversary and the compromised hosts), which would be subject to analysis by IronNet.
Because IronNet detects patterns of behaviors in addition to signatures, it is impervious to the attempts by Maze operators to obfuscate their activity on the network.
The sections below describe:
- The Maze ransomware attack kill chain in terms of its TTPs
- How IronNet NDR leverages its behavior-based analytical models to detect the attack throughout its various stages and provide the targeted organization multiple opportunities to detect and neutralize the threat.
Maze Group Kill Chain
A typical Maze ransomware attack progresses through the following stages of its kill chain:
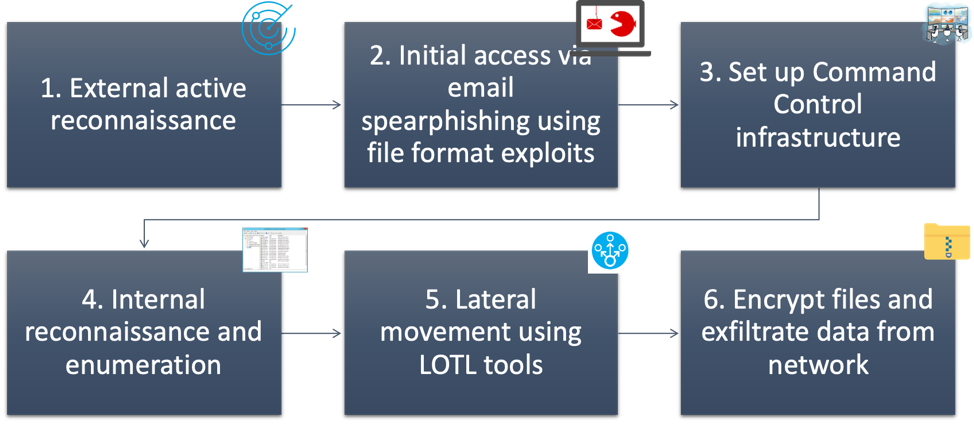
Figure 2: Maze ransomware attack kill chain
Now let’s describe each of these stages from an adversarial point of view:
Stage 1: Initial compromise
Various techniques have been observed of Maze threat actors to obtain initial access to its victims such as:
- Macro-laden MS Word documents sent to individuals which, when opened, deliver Cobalt Strike Beacon malware delivered via multiple stages
- Malicious RTF documents attached to emails that also victimize recipients in a similar manner
- Malware delivered via Exploit Kits hosted on compromised sites
- Logging on to an unsecured RDP account on a publicly accessible part of the company infrastructure
- Exploiting a misconfiguration on an internet-accessible system allowing the attacker to copy and load malicious tools on the system
- Obtaining access to internal systems via Citrix web gateway
Stage 2: Establish foothold and maintain presence
As the attack progresses, the Maze actor now aims to establish a foothold and maintain persistence on the compromised machines. It should be noted that in several cases the activity, and changes caused by execution of techniques and tools used for privilege escalation and persistence, is localized to an endpoint and not typically visible on the network which is where IronNet operates.
Some of the associated techniques in this stage of the attack are:
- Installation of CS beacon payloads in as many systems in the network as possible
- In some cases, web shells have been deployed to systems that are internet-facing. The system level access granted by these web shells was then used to enable initial privilege escalation and the execution of a backdoor, in most cases a CS Beacon, but occasionally use of Metasploit meterpreter payloads was also observed.
- Maze operators also obtained and maintained access to multiple domain and local system accounts with varying permissions that were used throughout their operations for lateral movement.
- Attackers also often created a new domain account and added it to the “Domain Administrators” group.
Stage 3: Establish command & control (C2)
At this stage the Maze operators have successfully obtained initial foothold and proceed to infect the machines with an advanced malware payload which is capable of persistent communication with its controller. In the case of Maze ransomware attacks Cobalt Strike (CS) exploitation framework would appear to be the exploitation tool of choice.
During this stage:
- Maze installs CS Beacon payloads to endpoints and servers widely in the post-compromise stage of the attack. Specifically, Maze operators use Cobalt Strike malleable C2 profiles for the installed beacon to communicate with CS servers.
- Malleable C2 provides operators with a method to mold Cobalt Strike command and control traffic to their will.
For example, if the target organization allows employees to use OneDrive, a malleable C2 profile can be generated to make Cobalt Strike’s C2 traffic look like OneDrive on the wire.
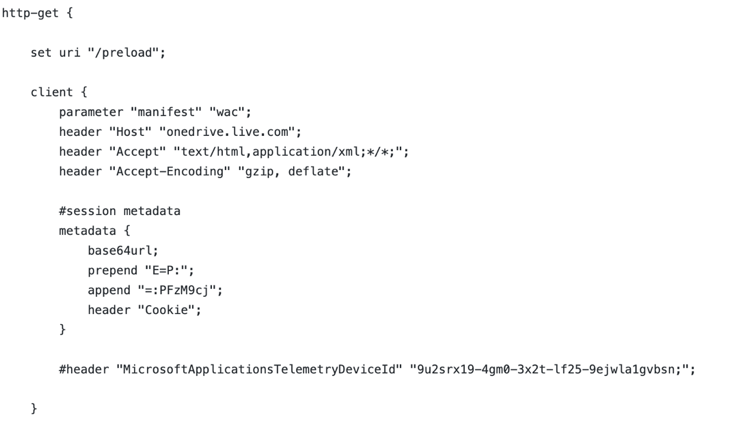
Figure 3: Part of a CS malleable C2 profile for OneDrive
During a typical C2 communication between a Beacon and the CS server we expect to see the following transaction on the wire:
- Beacon makes an HTTP GET request to Cobalt Strike's web server with the metadata that contains information about the compromised system.
- Cobalt Strike's web server responds to this HTTP GET with another HTTP GET with tasks that the Beacon must execute.
- As Beacon executes its tasks, it accumulates output. After all tasks are complete, Beacon checks if there is output to send. If there is no output, Beacon goes to sleep. If there is output, Beacon initiates an HTTP POST request containing a session id in a URI parameter or header (Cobalt Strike uses this information to associate the output with the right session).
- Cobalt Strike's web server may respond to an HTTP POST with anything it likes. Beacon ignores this information.
Stage 4: Escalate privileges
- Shortly after initial access, Maze operators used the popular Mimikatz tool to harvest credentials from memory (lsass.exe) and Registry (SAM file).
- These credentials are then used to move laterally to other machines on the network.
- In order to identify computers, accounts, groups and associated permissions the Maze operator also executes a large number of reconnaissance scripts via Cobalt Strike to collect network, host, filesystem, and domain related information. Majority of these scripts use Windows DOS commands, WMIC queries, and PowerShell commands, all integral parts of the Windows network ecosystem.
- Apart from the above techniques, the Maze operators also used specialized tools ADFind, Advanced IP Scanner, PowerSploit/PowerView, and Bloodhound to enumerate Windows network resources and obtain a “lay of the land” prior to extending the scope of the attack (installation of Beacon payloads on additional machines, obtaining additional privileges) via lateral movement (the next stage of the kill chain).
Stage 5: Lateral movement
- The Maze operator moved laterally throughout the network leveraging compromised service and user accounts obtained from the system on which they gained their initial foothold, allowing immediate access to additional systems.
- Stolen credentials using the Mimikatz tool were then used to move laterally across the network via RDP and to install Beacon payloads providing the actors with access to nearly one hundred hosts.
- Additionally, Maze operators used post exploitation modules available via CS Beacon payloads on compromised endpoints to move laterally across the network.
- The Maze operator also tunneled RDP using the ngrok utility and employed tscon to hijack legitimate RDP sessions to enable both lateral movement and privilege escalation.
Stage 6: Impact (completing the mission)
- Maze operators have been observed exfiltrating data (specifically files with .7z extension) to predefined FTP servers using a hard-coded username and password.
- Actors deploying Maze ransomware have also used the popular Windows file transfer utility WinSCP to exfiltrate data to an attacker-controlled FTP server.
- Additionally, Maze operators have used file replication utilities to copy data to cloud-based storage services.
- Volume shadow copies and other backup files found are also deleted to defeat attempts to restore data from local and network backups.
- Immediately following the exfiltration of sensitive data, the actors began deployment of Maze ransomware to hosts across the network and in some cases, thousands of hosts were ultimately encrypted. The ransom notes were stored in text files on each of the affected hosts and the wallpaper on these hosts was also altered to present the ransom note to the user.
Having completed the description of each of the Maze Ransomware attack stages from an adversarial POV, lets now examine how IronNet NDR would detect each of these stages of the attack from an Analyst/Defender’s POV.
IronNet detections across the Maze kill chain
This section describes (in stages) IronNet detections that would fire based on the activity IronNet sees on the wire.
Detection: initial compromise
While IronNet does not detect spearphishing attacks directly, it will detect immediate consequence of successful phishing attacks such as:
- download of payload binary
- attempts to obtain account credentials
- beaconing traffic associated with the Cobalt Strike (CS) Beacon payload
- presence of abnormal encrypted traffic on the wire.
The specific IronNet analytics that are expected to fire are:
- Domain analysis HTTP/TLS
- Beaconing HTTP/TLS
- Encrypted communications
- Suspicious file download
- Phishing HTTPS
Detection: Establish foothold and maintain presence
In the case of a Maze operator deploying CS Beacons on multiple systems, immediate consequences would be:
- multi-stage downloads of Beacon binaries
- beaconing traffic associated with the Beacon payloads
- presence of abnormal encrypted traffic
In cases where the Maze operator uploaded web shells that granted system level access to the on the internet-facing servers, this web shell foothold would then subsequently be used to download and execute CS Beacon payloads, the network visible effects of which would be detected by IronNet analytics.
While the creation, maintenance, and use of the domain or local user accounts (standard or those with domain admin rights) are primarily "endpoint visible,” IronNet would detect activity when such accounts are used for moving laterally amongst computers in the network.
Finally, while the creation of a new domain user account and its addition to the Domain Administrators group would not be directly detected by IronNet, usage of such accounts for lateral movement on the network would be detected by IronNet.
Overall, during this stage of the Maze attack IronNet would fire on various analytics such as:
- Beaconing HTTP
- Beaconing TLS
- Encrypted communications
- Suspicious file download
- Lateral Movement
Detection: Establish command & control (C2)
Regardless of the sophistication of the Command Control framework used by Cobalt Strike Beacon payloads to communicate with the CS servers, for example, the use of malleable C2 profiles to disguise and hide C2 traffic to blend in with the normal traffic seen in the targeted organization’s network, IronNet NDR will apply its network behavior based models to detect malicious C2 traffic and malicious C2 domains.
IronNet would fire on the following detection analytics:
- Beaconing C2 HTTP
- Beaconing C2 TLS
- Beaconing C2 DNS
Detection: Escalate privileges
Download, installation and use of Mimikatz tool to extract credentials from the SAM file and/or the LSASS memory will be undetectable with IronNet as this malicious activity is visible only on endpoints. However, post credential collection activity such as use of these newly acquired credentials for lateral movement would be detected using IronNet.
Corresponding to this activity, the following IronNet detections would be observed:
- Lateral movement
- Long sessions pairs/triplets
- Beaconing HTTP/TLS
- Encrypted communications
Both internal scanning and network activity associated with executing, maintaining and using a Cobalt Strike Beacon payload would be detected by IronNet.
Corresponding to this activity, the following IronNet detections would be observed:
- Internal scanning
- Beaconing HTTP/TLS
- Encrypted communications
Internal reconnaissance, scanning activity performed by tools such as Advanced IP finder, as well as built-in Windows/DOS commands, would be detected by IronNet. Internal scanning using tools such as Bloodhound and PowerSploit/PowerView would generate malicious network traffic (anomalous SMB traffic for example) inside the network that would be detected by IronNet. Corresponding to these activities, the following IronNet detections would be observed:
- Internal Scanning
Detection: Lateral movement
Maze actors primarily used Cobalt Strike Beacon payload for lateral movement; however, some other techniques were also occasionally noted. IronNet would detect lateral movement activity between machines.
IronNet would also detect post lateral movement (installation and execution of Beacon payloads on the new machines) via its beaconing and encrypted communications analytics.
Corresponding to this activity, the following IronNet detections would be observed:
- Lateral movement
- Long sessions pairs and triples
- Beaconing HTTP/TLS
- Encrypted communications
Furthermore, as IronNet relies on behavior-based detection rather than a specific signature or pattern — and because the CS Beacon’s built-in (post exploitation) lateral movement technique and Metasploit’s built-in lateral movement technique (smb_psexec) are behaviorally similar— this type of activity will be detected by IronNet’s lateral movement analytic.
Installation of a Cobalt Strike Beacon payload on the new endpoint (post-lateral movement) would also be detected by IronNet as a result of the C2 traffic that would be generated post payload execution.
Corresponding to this activity, the following IronNet detections would be observed:
- Lateral movement
- Long sessions pairs and triples
- Beaconing HTTP/TLS
- Encrypted communications
Detection: Exfiltrate data and encrypt files
Exfiltration of large amounts of data, which is typical in the case of ransomware, would be detected by IronNet’s unusual day and extreme rates analytics which detect suspicious network behavior on endpoints (in terms of unusual amount of data transfer) by way of comparison to a known baseline.
IronNet’s behavior detection models are agnostic of the type of tool or command used to exfiltrate data as long as they are behaviorally similar. In this case, even if the attacker modified the command to use a different form of data encoding, the network traffic generated by the endpoint involved in exfiltration activity would still trigger the extreme rate and/or unusual day analytic.
The activity of archiving data across corporate file shares and exfiltration over FTP would be detected by IronNet. But any localized activity that does not manifest on the network such as encryption of files in place, deletion of shadow copies on the endpoint, etc., would not be detected by IronNet.
However, the network activity could be time- and space-correlated with endpoint-based activity (process, registry, file system and event logs) observed by the EDR tool and/or SIEM.
Corresponding to these activities, the following IronNet detections would be observed:
- Unusual day
- Extreme rates
- Extreme rates TLS
The actual encryption of files on hosts on the network would not be directly addressed by IronNet.
However in order to get access to thousands of hosts and encrypt files on each one of them the actor needed to execute a series of commands that included commands (using WMIC and PSEXEC) to move laterally to the targeted hosts in order to copy and execute the Maze ransomware encryption scripts/commands on each one of them.
This lateral movement activity would be detected by IronNet regardless of what tool was used to perform this activity.
Corresponding to this activity, the following IronNet detections would be observed:
- Lateral movement
- Long sessions pairs and triples
Conclusion
A behavior-based approach to threat detection at the network level is necessary to detect malicious activities associated with sophisticated threat actors such as the Maze group.
The Maze group implements (this is not an exhaustive list):
- Rapidly changing tactics, tools, and procedures (especially the creative use and re-purposing of legitimate tools) making it almost impossible to resolve between “good use of a legitimate tool” and “malicious use of the same tool.”
- A dynamic external infrastructure necessary to support such operations (e.g. IP addresses and domains used to host C2, malware and act as file drops for exfiltration) making it an eternal (and unwinnable) game of “whack-a-mole” on rule-based perimeter defense systems such as NGFW and IPS.
- Use of advanced obfuscation and evasion at the endpoint level to bypass or confound NGAV and EDR tools.
- Use of malleable C2 profiles in an attempt to evade traditional rule and signature-based detection on the wire.
It is critical to adopt a solution that detects malicious behavior on the network rather than alerting based simply on the presence of a “known bad” indicator of compromise such as an IP or domain. This is the only way to stand any chance of early detection and neutralization of a sophisticated threat such as Maze Ransomware.
As we believe in IronNet, “the network doesn’t lie.”
.png)
