Despite the summer break for many, August was a busy and rewarding month for IronNet. We achieved FedRAMP Ready status, meaning that FedRAMP has approved IronNet as a Network Detection and Response (NDR) vendor for the U.S. government based on the program's standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.
Here’s how our IronDefense NDR solution works. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to threat sharing in real time so SOC analysts across companies can answer the common question: “What’s going on here?”
With IronNet’s correlated threat knowledge and SOAR integrations, SOC analysts can respond faster to threats within their existing SOAR platform (e.g., integrations for Splunk Phantom).
Below is a snapshot of our latest IronLens report from the IronNet CyOC team:
The September IronLens
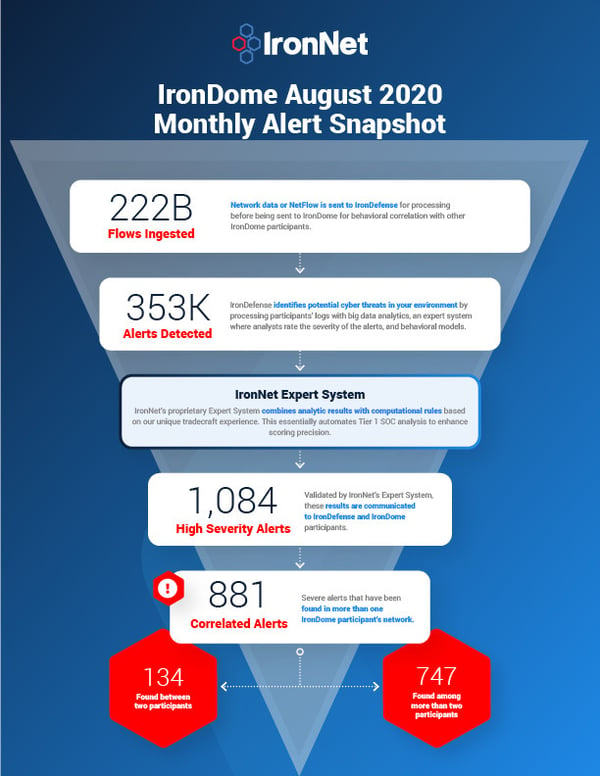
The ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. Analysts in the IronNet Cyber Operations Center (CyOC) review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered and correlated across the IronDome communities in August:
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 256 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. After consulting multiple OSINT resources, we rated the domain cssjs[.]co as malicious, as it appears to be associated with credit card skimming, specifically the MageCart campaign. We recommend blocking the domain and investigating traffic for loss of personally identifiable information (PII) and payment information. Another malicious domain includes 16b86fe6-c648-40c5-B714-17567427d821[.]server-100[.]deeponlines[.]com. This domain is associated with the Glupteba malware strain. If seen in your network, ensure there are no follow-on communications related to Glupteba Command and Control (C2) servers, which are well documented in OSINT.
These IoCs are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment. See the September IronLens Report for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In August, we created 9,578 threat intel rules of our 137,051 created to date. For example, new rules are based on analysis of new TeamTNT group cryptomining worm that can steal Amazon Web Services (AWS) credentials and scan for insecure Docker APIs (application programming interfaces). Our threat research team also looked into new variants of the venerable Agent Tesla Remote Access Trojan (RAT) distributed via COVID-19-themed phishing campaigns.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
Tracking Russian cyber threats
The IronNet CyOC continues to track industry threats, including the Russian threat landscape, to strengthen cybersecurity resiliency across industries. For example, we are tracking the functionality of a malware toolset dubbed Drovorub, according to a joint report released in August by the NSA and FBI. The agencies assert this malware has been used by Russian security services to facilitate cyber espionage operations. The report specifically attributes the malware to a military unit within the Russian General Staff Main Intelligence Directorate (GRU). This report is the third in recent months where the U.S. Intelligence Community has publicly attributed malicious cyber operations to Russian state actors.
Drovorub consists of multiple components, including a Linux implant and kernel module rootkit, which communicate with actor-controlled infrastructure using the WebSocket protocol. The endpoint malware contains functionality to support file transfer, port forwarding, and remote shells, while the Drovorub kernel module effectively hides artifacts of its presence on the infected system. Sophisticated obfuscation techniques such as these once again highlight the importance of leveraging behavior-based detection solutions such as IronDefense and the urgent need to collectively defend against state-sponsored threats.
You can see the latest industry news in the full report and in IronNet News.
That’s a wrap from the CyOC. See you next month.
.png)