July was a busy month for IronNet as we push forward our approach to cybersecurity via Network Detection and Response (NDR) and Collective Defense. Industry analysts are taking note as we help our customers pivot from threat detection to response quickly within their SOC’s existing security stack.
Here’s how we do it: First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to threat sharing in real time so SOC analysts across companies can answer the common question: “What’s going on here?”
With IronNet’s correlated threat knowledge and SOAR integrations, SOC analysts can respond faster to threats within their existing SOAR platform (e.g., integrations for Splunk Phantom).
Below is a snapshot of our latest IronLens report from the IronNet CyOC team:
The August IronLens from the IronNet CyOC
The ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. Analysts in the IronNet Cyber Operations Center (CyOC) review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered and correlated across the IronDome communities in July:
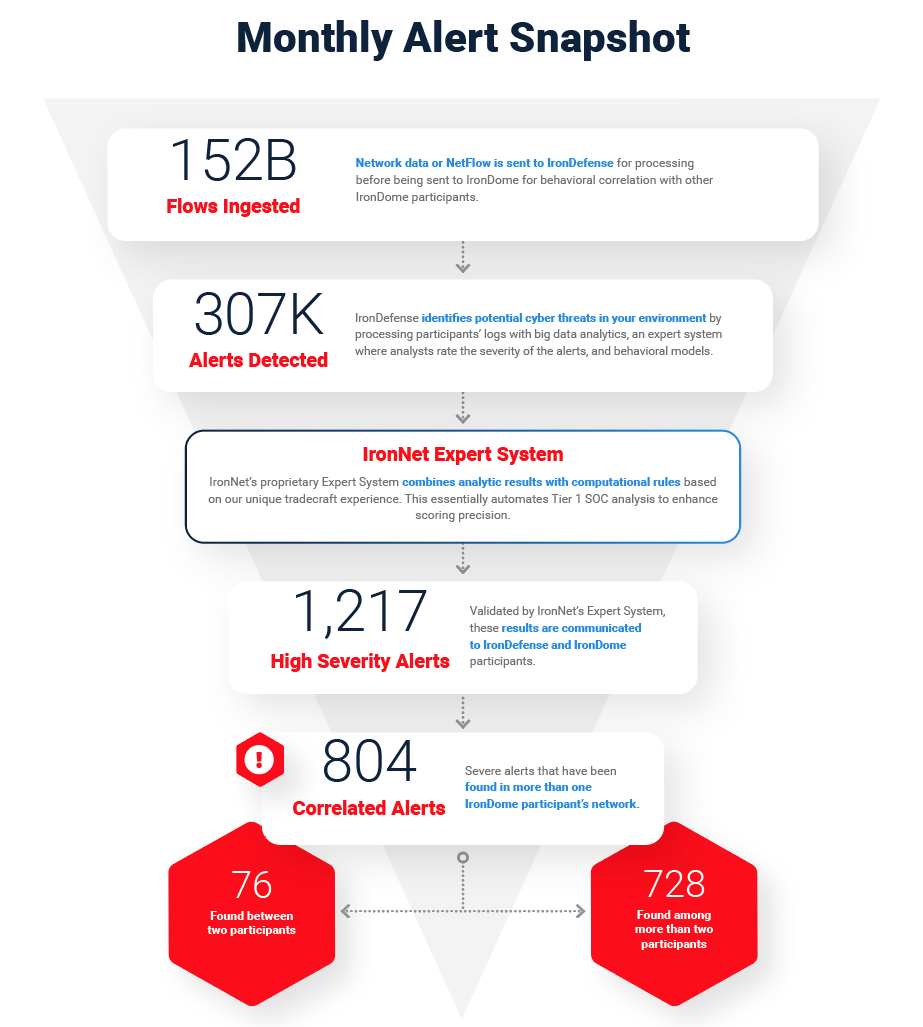
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 154 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. Some recent malicious IoCs include a Japanese language phishing page posing as an Amazon login with potential for personally identifiable information (PII) loss, including payment information. Also alerted as malicious was a domain appearing to be an Instagram phishing website. If seen in your network, we recommend investigating the traffic and blocking the domain.
These IoCs are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the August IronLens Report for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In July, we created 11,260 threat intel rules, including rules related to Cosmic Lynx business email compromise (BEC) campaigns targeting executives at Fortune 500 and Global 2000 corporations, as well as a cluster of activity impersonating cybersecurity vendors. You can see more in the full August IronLens CyOC Report.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
APT29 targeting COVID-19 research
The IronNet CyOC continues to track industry threats to strengthen cybersecurity resilience across industries. For example, we are tracking, according to a recent advisory from GCHQ, APT29 (also known as Cozy Bear). This adversary is currently targeting organizations in Canada, the U.S., and the U.K. who are engaging in COVID-19 vaccine research. The report includes descriptions of malware families referred to as WellMess and WellMail, which were not previously associated with APT29. Other TTP include basic vulnerability scanning against external IP addresses of organizations of interest and looking for opportunities to employ publicly available exploits that have been well-documented in recent months for use against vulnerabilities in Citrix, Pulse Secure, FortiGate, and Zimbra products. Historically, APT29 has targeted thinktanks and the Government, Healthcare, and Energy sectors. The importance of operating a robust vulnerability and patch management process are underscored by the description of this threat. TTPs such as these are not limited to this campaign. You can see the latest industry news in the full report and in IronNet News.
That’s a wrap from the CyOC. See you next month.

.png)

