Russia once again dominated headlines last month as both the REvil ransomware gang and APT 28 - SkinnyBoy (SB) were linked to numerous attacks. On the heels of the latest REvil attack on Kaseya this past week, the ransomware group targeted Sol Oriens, a U.S. federal nuclear contractor that consults for the U.S. Department of Energy's National Nuclear safety Administration, in June adding to the groups recent attack on meat producer JBS. Not to be outdone, a new Cyber Threat Intelligence Research and Adversary Hunting Team, Cluster25, has discovered a new backdoor being used in a series of attacks conducted by APT 28 (also known as Fancy Bear, Strontium).
At IronNet, we look to behavioral analytics to detect such unknown threats on enterprise networks before adversaries succeed at their end-game: exploitation or exfiltration. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to threat sharing in real time.
 The July IronNet Threat Intelligence Brief
The July IronNet Threat Intelligence Brief
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. As reported in the July Threat Intelligence Brief, our analysts review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered across the IronDome communities in May, showing 673 correlated alerts across IronDome participant environments:
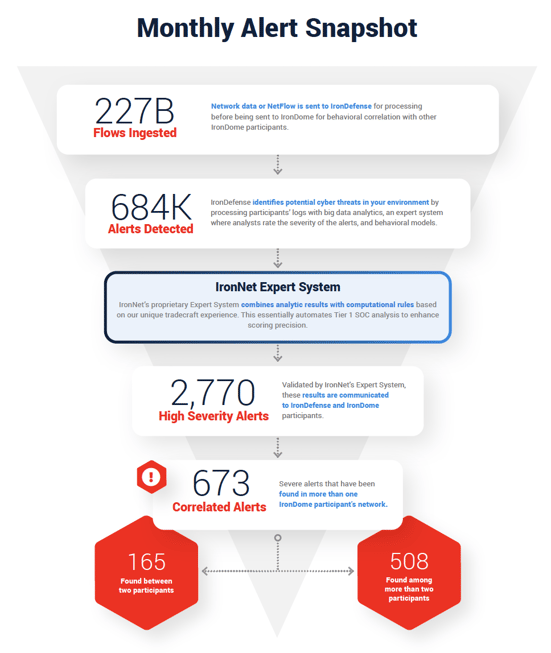
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 507 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. For example, we analyzed the malicious wcomhost[.]com. This domain appears to host an insurance site; however, it is actually a copy of the legitimate insurance site www.aquidneckislandinsurance[.]com. In the past, this domain has hosted fake PayPal login pages to lure clients into inserting personally identifiable information (PII) and credentials into form fields of the page. Ensure no PII was entered into form fields and block the domain.
All the IoCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the July Threat Intelligence Brief for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In June, we created 30,182 threat intel rules of our 250,986 created to date. Some examples of this month’s research include indicators associated with C2 domains for the Hupigon backdoor and IoCs surrounding the NOBELIUM phishing campaign.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
REvil Continues to Create Headaches
The REvil ransomware gang was recently revealed to have targeted Sol Oriens, a U.S. federal nuclear contractor that consults for the U.S. Department of Energy’s National Nuclear Safety Administration. Sol Oriens became aware of the attack in May 2021, but states no internal documents or sensitive information regarding U.S. nuclear programs was stolen. This latest ransomware attack by REvil adds to the group’s recent attacks on meat producer JBS, Japanese technology corporation Fujifilm, foodservice supplier Edward Dawn, and Apple supplier Quanta Computer.
REvil has been increasingly observed using QBot malware as an initial access vector. Although it originated as a banking Trojan, QBot has evolved into a sophisticated botnet that can compromise sensitive data, typically exploiting hijacked email threads to instigate the spread of infection. REvil is not the only ransomware group to leverage QBot; ProLock and Egregor have also been known to partner with the QBot group.
You can see the latest industry news in the full June brief or check out IronNet’s threat intelligence web page.


.png)



