July was yet another busy month in the world of cybersecurity. On July 19th, the U.S. government and its allies—including the European Union, the Five Eyes countries, and NATO—publicly condemned and blamed the People’s Republic of China (PRC) for a series of malicious cyber attacks, including the Microsoft Exchange Hacks, global ransomware attacks, and cyber attacks against medical research institutes and universities. We also saw the REvil ransomware group expand its arsenal to include a Linux variant, which allows the group to target ESXi and NAS (network-attached storage) devices. And to top it off, an advanced persistent threat (APT) group dubbed IndigoZebra has been identified conducting an ongoing spearphishing campaign against the Afghan government.
At IronNet, we look to behavioral analytics to detect such unknown threats on enterprise networks before adversaries succeed at their end-game: exploitation or exfiltration. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to threat sharing in real time.

The August IronNet Threat Intelligence Brief
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. As reported in the August Threat Intelligence Brief, our analysts review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered across the IronDome communities in July, showing 783 correlated alerts across IronDome participant environments:
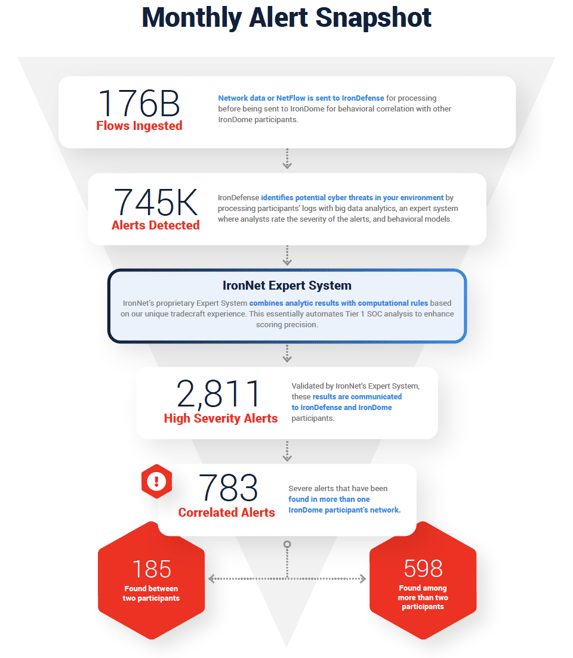
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 453 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. For example, we analyzed the malicious chilicuoghi[.]com. This is a phishing domain that could lead to potential personally identifiable information (PII) data loss. We recommend blocking the domain if it is seen in your network. All the IoCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the August Threat Intelligence Brief for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In July, we created 7,909 threat intel rules of our 258,895 created to date. Some examples of this month’s research include IoCs related to Cobalt Strike beacon payload distribution and command and control (C2). This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
REvil Linux variant and IndigoZebra targets Central Asia
The REvil ransomware group has expanded its arsenal to include a Linux variant, which allows the group to target ESXi and NAS (network-attached storage) devices. Similar to the Windows version of the ransomware that has targeted big names such as JBS, Acer, and Travelex, the Linux variant was first observed affecting ESXi and Linux systems in the wild in late May 2021. It is believed that REvil rapidly developed a Linux variant of its ransomware to compete against the Linux version of DarkSide that was released in March 2021. The development of a Linux variant of REvil ransomware poses a great threat and could be devastating to systems that rely on operational technology (OT)—such as critical infrastructure in the energy sector—since many devices on OT networks are Linux-based.


.png)



