
This month we are pleased to participate in National Cybersecurity Awareness Month. I personally would like to raise ongoing awareness that attackers continue to be successful with phishing campaigns. They are utilizing this technology to gain access to computers, steal your banking credentials, or compromise credit card numbers.
For consumers, there are a a few things to consider to protect against phishing: 1) Look before you click by hovering over links to see their true destination to ensure it matches the text you believe you are clicking on. 2) If an email sounds too good to be true, it probably is. 3) Use two-factor authentication where available to help mitigate the risks.
In enterprise environments, we use behavioral analytics to detect phishing threats, as well as additional unknown threats on the network. Here’s how our IronDefense NDR solution works. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to threat sharing in real time so SOC analysts across companies can answer the common question: “What’s going on here?”
With IronNet’s correlated threat knowledge and SOAR integrations, SOC analysts can respond faster to threats within their existing SOAR platform (e.g., integrations for Splunk Phantom).
Below is a snapshot of our latest IronLens report from the IronNet CyOC team:
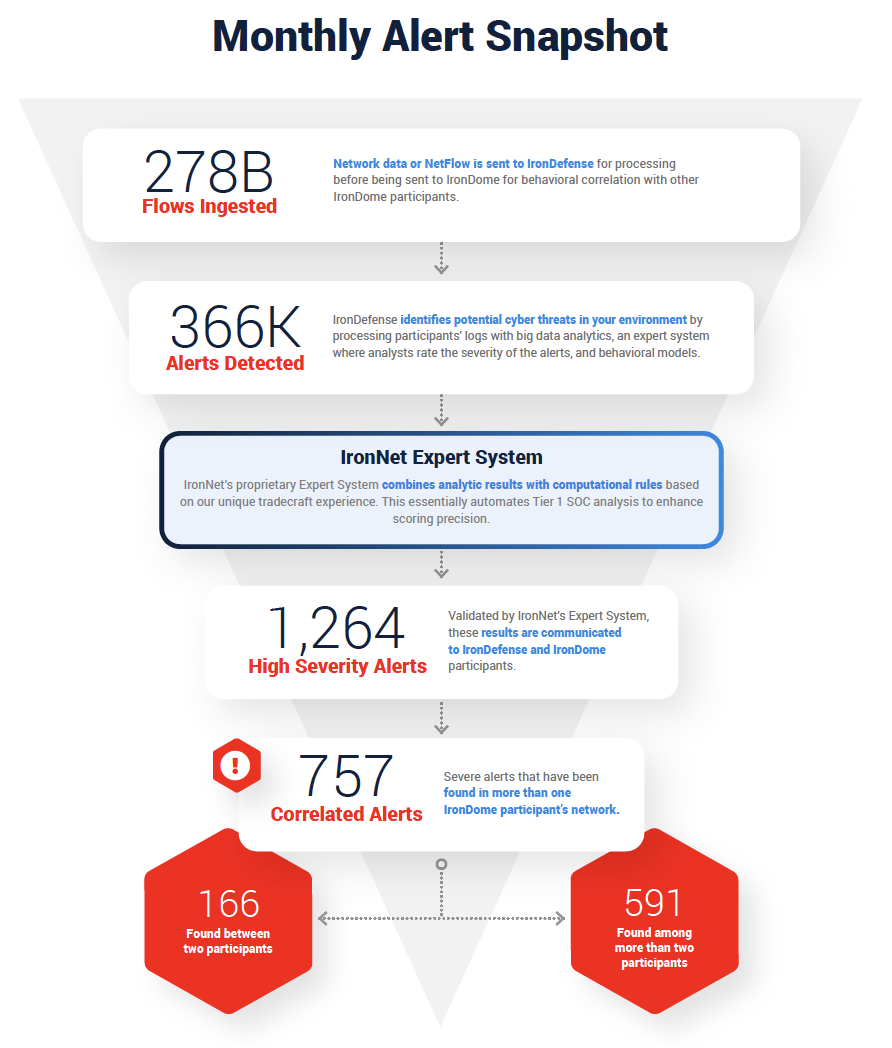
The October IronLens Threat Intelligence Report
The ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. Analysts in the IronNet Cyber Operations Center (CyOC) review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered and correlated across the IronDome communities in September, showing 757 alerts across IronDome participant environments:
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 352 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. For example, we analyzed a malicious domain (hajjumrahinfo[.]com) that appears to be hosting an active Chase Bank phishing login page. Many of the links and content of the site send the user to the legitimate Chase Bank website. The site appears to be harvesting credentials and security verification information, such as social security number, email address, and login information. If seen in your network, investigate the traffic for loss of personally identifiable information (PII) and block the domain.
All the IoCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the October IronLens Report for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In September, we created 15,078 threat intel rules of our 152,129 created to date. For example, new rules are based on analysis of exposed Docker servers infected with malicious payloads for cryptomining and Distributed Denial-of-Service (DDoS) attacks. Our threat research team also looked into the Baka e-commerce skimmer that has been observed on several merchant websites across multiple global regions.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
Recent Mac OS malware “notarized” by Apple
The IronNet CyOC continues to track industry threats to strengthen cybersecurity resilience across industries. For example, an instance of malicious software targeting Mac users was recently identified by cybersecurity researcher Patrick Wardle. In a blog post, Wardle described a piece of malware that appears to have been legitimately “notarized” by Apple.
Apple introduced the notarization process with the release of Mac OS Catalina in late 2019, which requires software developers to submit applications to Apple for review and approval prior to distribution. Such notarization allows for applications to be trusted by the operating system. This incident calls into question the security of the notarization process itself. This particular payload was observed delivering the Shlayer malware, which in turn installs various Mac OS adware.
This example illustrates the importance of defense-in-depth and the pitfalls of over-reliance on individual security controls. Behavioral detection techniques also become particularly valuable for detecting malicious activity when trusted processes are co-opted or compromised, as appears to have occurred in this case.
You can see the latest industry news in the full report and in IronNet News.
That’s a wrap from the CyOC. See you next month.
.png)

