At IronNet, we believe proactive Collective Defense can raise the bar on cybersecurity by allowing enterprises, business ecosystems, industry sectors, states, and nations to work together to stave off and defend against highly sophisticated adversaries. How does this new approach work? It’s simple: knowledge sharing in near real time. By communicating correlated threat behaviors across the IronDome Collective Defense platform, every stakeholder can mutually aid in the detection, remediation, and mitigation of cyber threats to any single organization. In other words, the sum of us working together is much greater than any one part.
Let’s take a closer look at recent threats affecting the cyber community.
The March IronLens from the IronNet CyOC
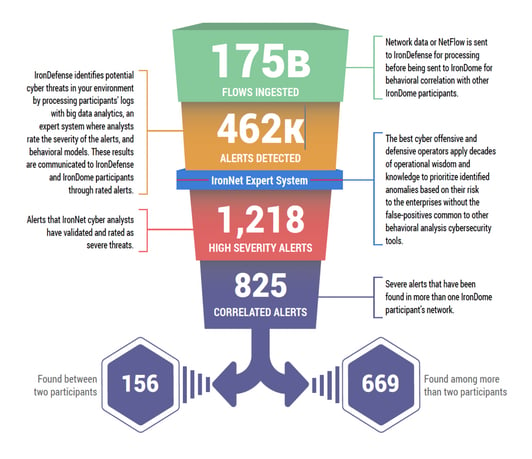
No single organization has sufficient analysts and threat intelligence to track all major threat groups and realistically monitor their activities in near real time. IronNet’s IronDome Collective Defense platform allows the threat analysts in IronNet’s Cyber Operations Center (CyOC) to correlate patterns of behavior across IronDome participants’ networks. Keep in mind that these communities are cross-sector and include both large and small companies. Large companies benefit, for example, by gaining visibility of threats that affect the smaller companies they depend on, and smaller companies benefit from broader awareness and resources for threat detection. All participants can see “innocuous” threats in a new light if they appear across the ecosystem.
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. Essentially we ingest and process millions of data flows, analyze and rate them, and share them with IronDome participants. Sending alerts through the funnel in this way greatly diminishes “alert fatigue” for SOC analysts.
Here is a snapshot of what we discovered in March:
Our sharp eye on cyber threats
In addition to correlated alerts, significant IronDome community findings revealed 202 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. These IoCs are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
Recent Indicators of Compromise included a phishing campaign using a domain disguised as a Microsoft Office login page and another phishing activity posing as a valid eBay login page. Detection of this type of credential harvesting activity is critically important as it typically occurs early in the Kill Chain as a precursor to the more nefarious activity a threat actor seeks to undertake. See the March IronLens Report for the full list.
The bigger picture of collective defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants. In March, we created 5,296 threat intel rules, including rules related to a variety of APT campaigns utilizing coronavirus-themed lures to enable malware distribution. You can see more in the full March IronLens CyOC Report.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
A wider aperture for cyber defense
The CyOC continues to track industry threats to strengthen cybersecurity resilience across industries. For example, we are seeing cyber criminals stand up bogus coronavirus-themed web pages designed to attract targets who are just looking for information online. To collect as many victims as possible, these adversaries commonly use current and popular themes in the news as topics for phishing campaigns. For example, when the disappearance of Malaysian Flight MH370 in the Asia Pacific region was in the news headlines for months, cyber threat actors were quick to incorporate this theme into their phishing campaigns, attempting to entice users to click a link or download a file. Unfortunately, COVID-19 is the latest theme shepherding these malicious campaigns.
As such, the U.S. Department of Homeland Security Cybersecurity and Infrastructure Security Agency has released an alert, warning individuals to remain vigilant for scams related to COVID-19. Healthcare industry stakeholders can hear more from our healthcare cybersecurity expert John Ford about ways to stay cyber-vigilant against these egregious threats in this trying time.
That’s a wrap from the CyOC. See you next month.


.png)


