On June 18th, an IronNet customer in the education sector was targeted in a ransomware attack. Initial investigation of the compromise points to the BlackCat ransomware group as the possible threat actor behind this intrusion. It is unclear at this time how the threat actors gained initial access; however, we did observe a spike in scanning prior to the compromise through our external and internal port scanning analytics. After that, we saw the attackers establishing a foothold through an independent C2 before switching to AnyDesk and RDP (remote desk protocol) and using these remote access tools to conduct more malicious activity on target hosts.

At IronNet, we look to behavioral analytics to detect unknown threats on enterprise networks before adversaries succeed at their endgame: exploitation or exfiltration. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our IronDefense NDR expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to crowdsourced threat intelligence exchange in real time.
The July IronNet Threat Intelligence Brief
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. As reported in the July Threat Intelligence Brief, our analysts review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
Here is a snapshot of what we discovered across the IronDome communities in June, showing 696 correlated alerts across IronDome participant environments:
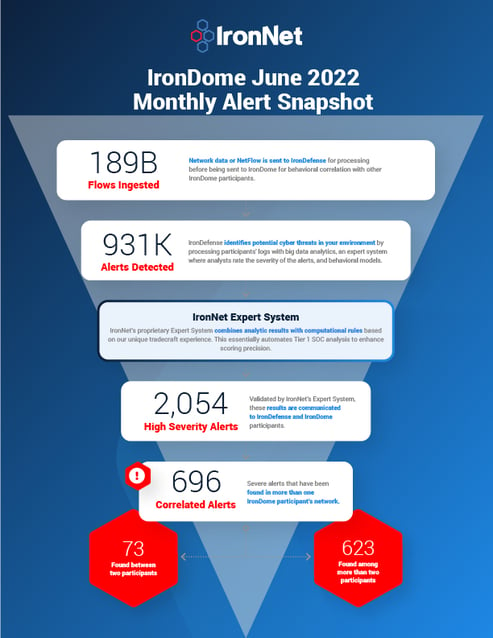
Given the unique cross-sector visibility and Collective Defense capabilities of IronDome, we are able to highlight the most frequent behaviors each month, in turn enabling us to track trends over time. For June, the most frequent behavior analytics were DNS Tunneling (1,992), New and Suspicious Domains (283), and Credential Phishing (157).
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 623 Indicators of Compromise (IOC) that may pose risk to IronDome participant environments. For example, we analyzed the malicious domain freecaptcha[.]top, which asks the user to allow push notifications when certain URL parameters are passed. Users should not allow these spam push notifications as they could potentially lead to suspicious or malicious sites or downloads. We recommend blocking the domain and further investigating traffic.
All the IOCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the July Threat Intelligence Brief for the full list of recent IOCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIR) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In June, we created 13,668 threat intel rules of our 320,697 created to date. Some examples of this month’s research related to indicators associated with Cobalt Strike beacon payload distribution and C2, IOCs related to XLoader malware, and Sauron command-and-control malware domains.
This combination of behavior-driven and IOC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
Suspected BlackCat ransomware attack
BlackCat (aka ALPHV) is a ransomware family that was first observed in November 2021, when it garnered attention for being one of the first ransomware families written in the programming language Rust. BlackCat operates under a ransomware-as-a-service (RaaS) model, which means affiliate groups or hackers use the BlackCat ransomware to carry out attacks against targets and then give a percentage of that profit back to BlackCat. For this reason, the TTPs used like the initial entry vector and the ransomware execution itself vary depending on the affiliate conducting the attack. There have been reports that BlackCat may be a subdivision of, or is at least connected to, the “recently dissolved” Conti ransomware group.
You can see the latest industry news in the full brief or check out IronNet’s threat intelligence hub.


.png)



