As part of the IronNet Cyber Operations Center (CyOC) team, I am part of the team that creates threat intelligence rules to accelerate threat detection at our customers’ sites. We are committed to doing threat detection groundwork that can help overcome cybersecurity shortages while also alleviating “alert fatigue” at our customers’ in-house SOCs. Collective Defense is our unique collaborative approach.
Specifically, we focus on detecting “unknown unknowns” by correlating patterns of behaviors across the networks of companies and organizations participating in our IronDome Collective Defense platform. Participants can share threat knowledge, too, and volunteer comments related to how to triage. This kind of collaboration benefits everyone.
This month we created signatures looking for Indicators of Compromise identified by a variety of IronNet analytics, including Suspicious File Download, Domain Generation Algorithm, and Phishing HTTPS. Additionally, we created rules for indicators identified during malware triage (e.g., specifically looking at an emerging Remcos RAT campaign and a Parallax RAT campaign).
Let’s take a closer look at recent threats affecting this cyber community.
The May IronLens from the IronNet CyOC
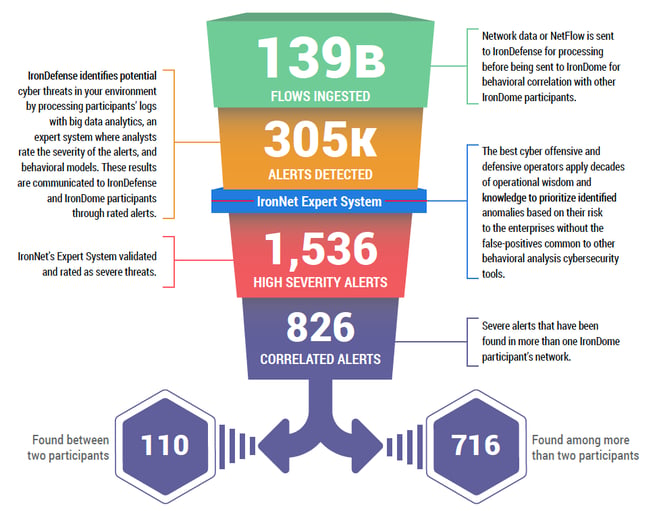
This ability to analyze and correlate seemingly unrelated instances is critical for identifying attackers who leverage varying infrastructures to hide their activity from detection. Analysts in our CyOC review alerts from millions of data flows that are ingested and processed with big data analytics. The ratings that are applied to alerts (benign/suspicious/malicious) are immediately shared with IronDome participants. Funneling alerts in this way is how we do our part in diminishing “alert fatigue” instead of piling on more work for SOC analysts.
Here is a snapshot of what we discovered and correlated across the IronDome communities in May:
Our sharp eye on cyber threats
In addition to correlated alerts, significant IronDome community findings revealed 143 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. These IoCs are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
Recent malicious Indicators of Compromise included:
- a domain hosting a Trojan posing as a fake Microsoft login page targeting corporate login credentials
- a scam site posing as eBay Motors (eBay’s auto parts and vehicles site) but hosting fake listings while using a copied version of the actual eBay site
- a domain used to host Valak malware, which has the ability to conduct reconnaissance, collecting user, machine, and network information to send back to control servers.
See the May IronLens Report for the full IoC list.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants. In May, we created 9,272 threat intel rules, including rules related to a threat leveraging illegitimate Zoom installers to drop malware. You can see more in the full May IronLens CyOC Report.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
A wider aperture for cyber defense
The CyOC continues to track industry threats to strengthen cybersecurity resilience across industries. For example, a new campaign dubbed “Phantom in the Command Shell” has been identified targeting the global financial sector with an updated variant of EVILNUM malware. Although this campaign began on May 3, 2020, EVILNUM malware was originally discovered in 2018. This newest variant appears to have incorporated new methods for evading both host- and network-based detection mechanisms. The infection chain begins with an end-user accessing a link to a file hosted in Google Drive. The malware conducts some system enumeration and alters actions (such as determining what to use for command and control) by evaluating which antivirus products are detected on the host machine. Ultimately, this malware is capable of stealing files and cookies and may be able to load additional payloads onto infected systems. You can see the latest industry news in the full report and in IronNet News.
That’s a wrap from the IronNet CyOC. See you next month.


.png)


