
Everyone working behind the scenes at any SOC, in any industry, knows that there is a shortage of analysts to monitor, track, and triage network threats. The number of threats is growing faster than we can keep up. Nevermind what the specific ratio of threats to analysts is. We all feel it.
One of the ways we try to close this gap is to do much of the threat detection groundwork so SOC analysts at our customers’ sites can focus more of their already-pressed time on triage and response. But not only do our overwhelmed counterparts need extra sets of eyes on the threat landscape, they also need a way to reduce “alert fatigue” once threats are detected. That’s where correlating threats comes into play. IronDome is IronNet's Collective Defense platform for sharing threat knowledge in near real time. We correlate patterns of behaviors across the networks of companies participating in our IronDome communities. Participants can share threat knowledge, too, and volunteer comments related to how to triage. This kind of collaboration benefits everyone.
Let’s take a closer look at recent threats affecting this cyber community.
The April IronLens from the IronNet CyOC
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. Analysts in our CyOC review alerts from millions of data flows that are ingested and processed with big data analytics. The ratings that are applied to alerts (benign/suspicious/malicious) are immediately shared with correlating IronDome participants. Funneling alerts in this way is how we do our part in diminishing “alert fatigue” instead of piling on more work for SOC analysts.
Here is a snapshot of what we discovered and correlated across the IronDome communities in April:
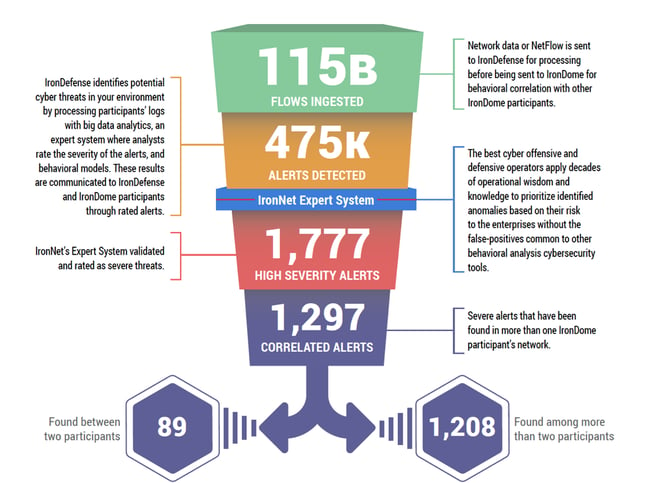
Our sharp eye on cyber threats
In addition to correlated alerts, significant IronDome community findings revealed 76 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. These IoCs are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
Recent Indicators of Compromise included a phishing campaign that impersonates a valid PayPal account login. A user may lose their PayPal account credentials if they input them into
this login page. The site appeared to be taken down on or around April 9, 2020, but, if seen in your network, it’s worth investigating the traffic and contacting users to ensure no loss of personally identifiable information (PII) has occurred. Detection of this type of credential harvesting activity is critically important as it typically occurs early in the Kill Chain as threat actors are exploring ways to launch bigger attacks. Additionally, we know that credential reuse is a very real risk, and it is difficult to know whether the stolen PayPal password will unlock the keys to the kingdom elsewhere. See the April IronLens Report for the full IoC list.
The bigger picture of collective defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants. In April, we created 8,977 threat intel rules, including rules related to a recent phishing campaign that uses VPN access for remote work as a lure. You can see more in the full April IronLens CyOC Report.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
A wider aperture for cyber defense
The CyOC continues to track industry threats to strengthen cybersecurity resilience across industries. For example, on April 9th, the U.S. Department of Justice published a recommendation to revoke
China Telecom Corporation’s authorization to operate in the United States. This decision was based on several reasons, including concerns that China Telecom might be vulnerable to undue influence from the Chinese government, and inaccurate information provided to the U.S. government with respect to China Telecom’s data storage and cybersecurity practices. China Telecom had previously been involved in several incidents of Border Gateway Protocol (BGP) misdirection, which resulted in large amounts of internet traffic being unnecessarily routed through mainland China.
While it is not clear whether these incidents were deliberate or accidental, the concerns arising from these episodes likely contributed to the Executive Branch’s decision to push forward with the recommendation. We will continue to track this threat and its implications.
That’s a wrap from the CyOC. See you next month.
.png)

