When considering the latest tech widget, do you ever ask yourself, “Why should I change?” "Will adopting this new technology, as advertised, make my life better or will it also undoubtedly introduce friction, a new workflow, or training that I do not have the time or patience for?" Again, the why takes over. For example, why should I start using a Roomba to clean my house when the vacuum cleaner I own already works just fine? On top of that, I have no idea how it will work with kids, dogs, and stairs.
At IronNet we understand this concern whenever a new technology comes out. That is why the user experience is just as important as the technology itself. What good is the innovation if it is an imposition to get up and running? We regard Collective Defense and advanced network traffic analysis as unique and second-to-none cybersecurity capabilities that are transforming the way we approach cybersecurity. Yet we are just as committed to minimizing the amount of change and effort needed to adopt and integrate these capabilities with existing cybersecurity technology stacks.
Integrating the new within your existing cybersecurity ecosystem
Well-established enterprise SOCs and MSSPs already have an ecosystem of products they rely on to provide cybersecurity. These products include endpoint protection, firewalls, email protection, threat intelligence feeds, and more. Additionally, SOCs already have a single pane of glass within their SIEM and have methods for conducting automated response within their SOAR. They also have ticketing and asset management systems in place. It makes sense, then, that when vendors come knocking, a SOC manager may have the same initial response as I had to the Roomba, “Sounds promising, but is this “shiny latest and greatest” really worth the investment and any changes I may have to make?” If you want to see unknown threats around the corner so you can keep your security house in order, with less effort and time, the answer is yes.
IronNet positions its product offerings in a way that does not introduce friction into the SOC, while also still providing network threat detection and a Collective Defense platform designed to give greater context to detections using global, curated, and trusted bidirectional intelligence. By integrating within an existing cybersecurity ecosystem, IronNet’s IronDefense and IronDome products have immediate impact. Today, these include integrations with leading SIEM, SOAR, and ITSM products. Tomorrow, these integrations will expand to leading EDR and NGFW products.
First and foremost, the key to integrations is a solid and available API. Traditional cybersecurity product APIs include the ability to export information such as detections. IronNet’s IronAPI provides the ability to export detections in both on-demand query and polling methods. The polling methods provide server side state, allowing clients to pick up where they left off and alleviating the necessity for the client to be fault tolerant. IronAPI also provides a unique ability for customers to report back their detection evaluations. Crowdsourcing customer feedback is at the core of IronNet’s Collective Defense. By correlating network behaviors between enterprises, sectors, and nations — both domestic and global. Furthermore, IronNet’s detections include additional contextual information to aid the alert triage process. This information drastically reduces the time required to turn the unknown detection into a known threat, thus moving enterprises from being reactive to proactive.
IronAPI Swagger Documentation
Each of IronNet’s integrations is designed to allow both the ingestion of detections and the ability to rate detections to enable Collective Defense. SIEM integrations in Splunk and QRadar receive all detection information in a format that is conducive for additional correlation within the SIEM. The SIEM integrations also include dashboards that allow an analyst to focus exclusively on IronNet’s detections, and, with a single click, provide the ability to pivot into IronNet’s user interface, IronVue. This capability allows customers to view PCAP, raw metadata, etc. and the new Detection Correlation Dashboard, which allows customers to visualize campaigns as they develop across the globe, all while still providing the necessary API capabilities required to understand network detections and Collective Defense.
IronDome's Detection Correlation Dashboard
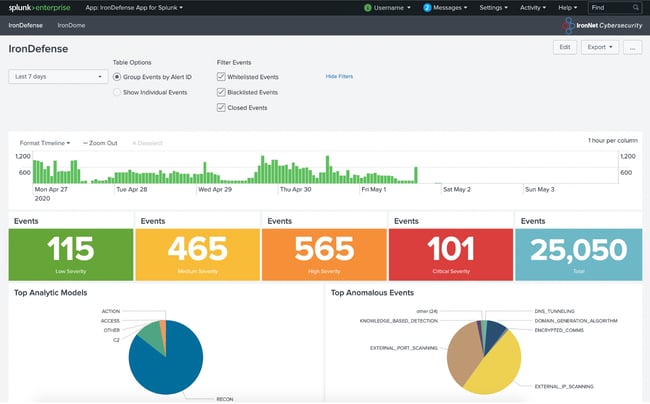
IronDefense dashboard in Splunk
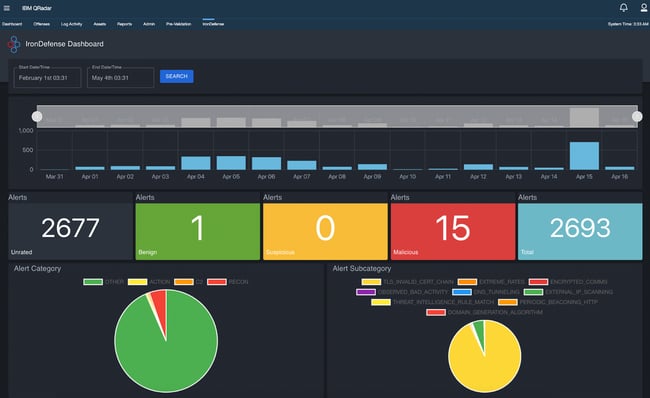
IronDefense dashboard in QRadar
SOAR integrations in Phantom, XSOAR (formerly known as Demisto), and Swimlane expose the same IronAPI endpoints for ingesting detections and responding with analyst feedback. The SOAR integrations also expose the ability to send IOCs from threats detected on the enterprise to IronDome to determine if the threat had been seen previously by other anonymized customers of IronNet and to provide the ability to distribute signatures (threat intelligence rules). This capability allows all IronDome participants to benefit from the shared (anonymized) intelligence derived from the detected threat. IronAPI is available within SOAR playbooks to support pulling additional context from endpoint, phishing, and firewall products when analyzing network threats, and for using network detections while triaging detections from other products. Within the playbook, network detections can be turned into proactive measures, such as containing a device on the enterprise network or setting up new firewall rules automatically.
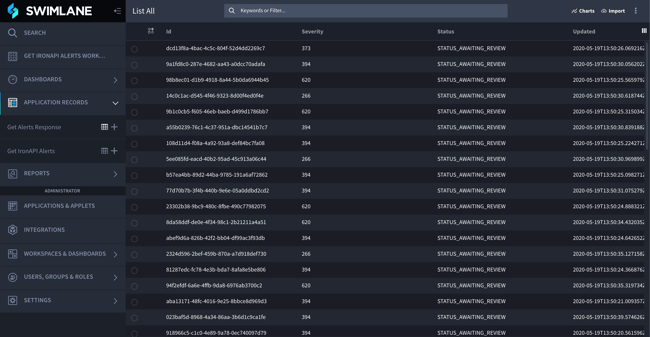
Swimlane dashboard
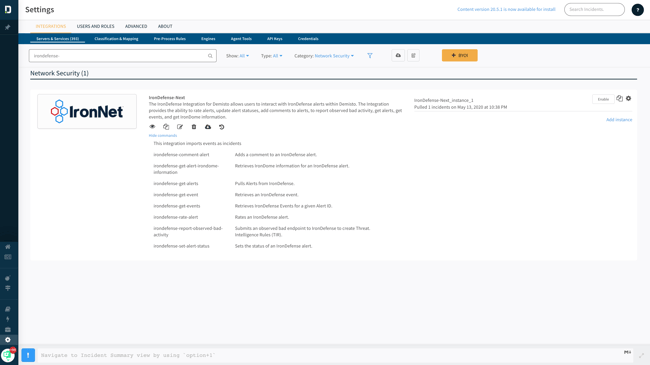
XSOAR (Demisto) integration
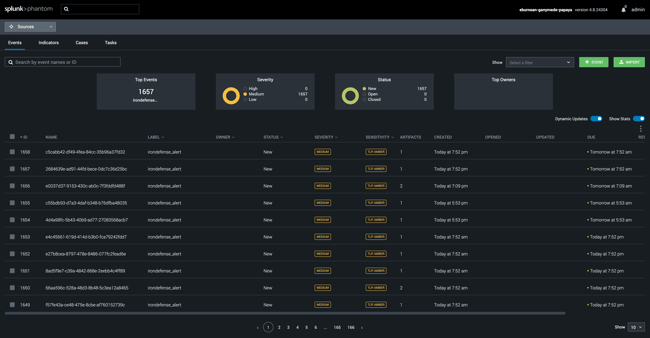
Phantom integration
Workflow integrations
Large enterprises are driven by ticket management. ITSM integrations in ServiceNow focus on enabling workflow. By giving customers the option to create ServiceNow events when triaging IronNet detections, the significant and tedious tasks of copying information from one product to another are eliminated.
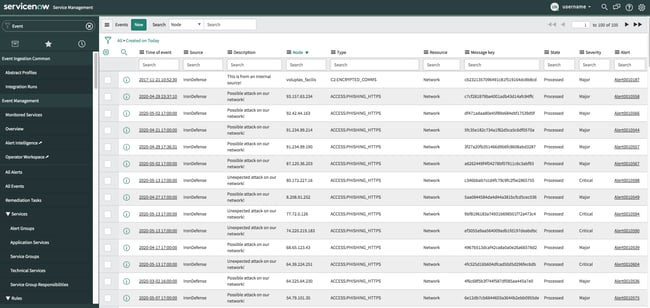
ITSM - Information Technology Service Management
The IronNet approach is not to change SOC workflow; instead, it is to offer protection at the network layer that detects the unknown while allowing the SOC to continue operating efficiently and effectively. Does IronDefense increase the ability to detect threats? Yes. Does IronDome increase the intelligence and brain power of the SOC? Yes. Should those come at a sacrifice to the SOC analyst? No, and they don’t.
Keeping the cyber house in order
But back to the Roomba. It has transformed cleaning from a reactive process to a proactive one that saves time and effort. Rethinking my approach was worth the change. My floors have never been cleaner, and the product is smart enough to work well in my house/environment — kids, stairs, pets, and all. With IronDefense and IronDome, we hope your cyber house is in better order, with easy integration, no matter your existing cybersecurity infrastructure.
.png)
