In mid-January there were multiple attacks on the Ukrainian government website. Several webpages were wiped and defaced stating that Ukrainian, Russian, and Polish personal data was leaked. Microsoft observed destructive malware activity tracked as DEV-0586 used in intrusion attacks against the Ukrainian government agencies. There has not been any association between DEV-0586 and any other known threat actor groups.

At IronNet, we look to behavioral analytics to detect unknown threats on enterprise networks before adversaries succeed at their end-game: exploitation or exfiltration. First, we do the threat detection groundwork needed to spot abnormal network activity across our customers’ networks. Second, our IronDefense NDR expert system scores these alerts, prioritizing the most interesting events to help cut down on alert fatigue. Finally, we take a Collective Defense approach to crowdsourced threat sharing in real time.
The February IronNet Threat Intelligence Brief
This ability to analyze and correlate seemingly unrelated instances is critical for identifying sophisticated attackers who leverage varying infrastructures to hide their activity from existing cyber defenses. As reported in the February Threat Intelligence Brief, our analysts review alerts from millions of data flows that are ingested and processed with big data analytics. We apply ratings to the alerts (benign/suspicious/malicious) and immediately share them with IronDome Collective Defense participants.
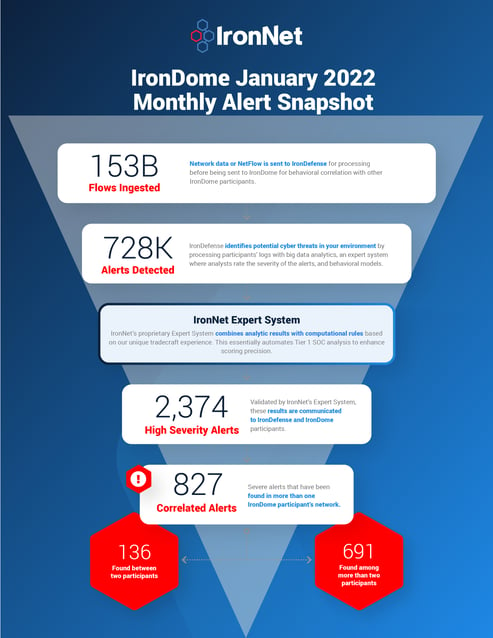
Here is a snapshot of what we discovered across the IronDome communities in January, showing 827 correlated alerts across IronDome participant environments:
Given the unique cross-sector visibility and Collective Defense capabilities of IronDome, we are able to highlight the most frequent behaviors each month, in turn enabling us to track trends over time. For January, the most frequent behavior analytics were External Scanning (477), C2 Rendevous (DGA) (185), and New and Suspicious Domains (142).
Analysis of IOCs
In addition to correlated alerts, significant IronDome community findings revealed 552 Indicators of Compromise (IoC) that may pose risk to IronDome participant environments. For example, we analyzed the malicious domain best-lucky-man[.]xyz, known for hosting process injection malware detected by ESET and VirusTotal.
All the IoCs we analyzed are used to trigger alerts that are mapped to the Cyber Kill Chain to identify the stage and progression of the threat. They can be used to create detection rules for network, endpoint, or other security tools currently deployed to mitigate cyber risk in each IronDome participant’s environment.
See the February Threat Intelligence Brief for the full list of recent IoCs.
The bigger picture of Collective Defense
Every month, IronNet’s expert threat analysts create threat intelligence rules (TIRs) based on significant community findings from IronDome, malware analysis, threat research, or other methods to ensure timely detection of malicious behavior targeting an enterprise or other IronDome community participants.
In January, we created 3,521 threat intel rules of our 293,909 created to date. Some examples of this month’s research related to indicators associated with malware delivery domains for Gafgyt, Setag, Tsunami, Typosquat, ClipBanker, and Perseus malware.
This combination of behavior-driven and IoC signature-based detection, alert ranking, and sharing ensures IronDome participants have the broadest view of threats facing their enterprise.
Ukrainian government website attack
As I mentioned, multiple Ukrainian government websites were targeted and personal data was leaked. The Secret Service of Ukraine (SSU) reported this was the result supply chain attack that allowed the threat actors to to access a company called Kitsoft. Kitsoft manages websites for the Ukrainian government websites impacted by the attack included the Ukrainian Ministry of Foreign Affairs, Ministry of Education and Science, Ministry of Defense, the State Emergency Service, the website for the Cabinet of Ministers, and others. It's reported that reported threat actors tried to compromise 70 websites but only reached 10.
On January 13, Microsoft observed destructive malware being used in intrusion attacks against numerous Ukrainian government agencies and associated organizations. While it appears the malware was designed to look like ransomware, its lack of ransom recovery indicates that its purpose was to render the system inoperable.
The two-stage malware first overwrites the Master Boot Records and leaves a ransomware note containing a Bitcoin wallet and ToxID. The second stage executes when the compromised device is powered down. This activity is known as DEV-0586. Lastly, given the timing of the wiper malware deployment and the fact the messages on the website said data had been stolen and deleted, there is some speculation that the website defacements and wiper malware attacks were intended to have been better coordinated.
You can see the latest industry news in the full brief or check out IronNet’s threat intelligence hub.
.png)