A cyber checkup: 3 steps to “proving the positive” that your network is healthy
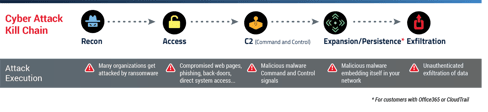
Did you know that it took well over a year for the infamous SolarWinds breach to be discovered, according to Crowdstrike? What is a cyber attacker, especially an advanced persistent threat (APT) group, doing during this crucial dwell time? In short, they are scoping out the network to determine the best way to escalate their privileges and figure out how to leverage network resources to reach their endgame: data exfiltration or system control. In the SolarWinds case, the adversary embedded malicious code into a widespread software update that affected 18,000 companies and organizations.
The type of attack vector for a data breach can prolong network dwell time and, accordingly, time to detection. Take breaches caused by stolen or compromised credentials, for instance. These take the longest of all to detect: an incredible 250 days (vs. the average of 212 days). Similarly, breaches caused by phishing take about 213 days to identify.
The question at hand is this: How would you know if you were breached (and do you even have a way to know)? If you’re not sure how to answer this question, it may be time for a cyber checkup. Think of a cyber checkup as an annual wellness visit to the doctor. The sooner you detect anything bad (i.e., a breach), the sooner you can respond, enabling you to reduce the negative efforts, or exposure in the case of cyber.
Regular cyber checkups are best, and they do have a spectrum:
Step 1: Take your temperature
Easy-peasy! This step involves checking whether any known Indicators of Compromise (IOCs) are present on your network. You can detect IOCs using signature-based detection tools. These indicators are the bread crumbs or old-school calling cards that reveal an adversary has stopped by, creating a known threat that easily can be checked.
Step 2: Get deeper insights from the experts
But what about threats that don’t have signatures associated with them yet? After all, it is broadly accepted in the analyst community that it takes only a small change to hash values, IPs, or domains for attackers to evade signature-based detection tools. That’s why it is critical to take detection efforts up a notch by using behavioral analytics, which let you dip deeper into what’s happening in your network based on machine learning algorithms tuned to alarm on suspicious activities.
It’s crucial to take a closer look at what’s on your network given that adversarial tactics, techniques, and procedures (TTP) are the most difficult for an attacker to change. Therefore, TTPs are the best type of indicators for defenders to focus their detection efforts and, quite frankly, the only way to “prove the positive” that your network is healthy, safe, and sound.
Step 3: Take a super proactive approach to your cyber health
A mindset of “proving the positive” shifts cyber defense from a reactive to a proactive posture for early detection “left of boom” — a phrase in military vernacular that refers to disrupting insurgent activity before the adversaries can build or plant bombs. The same holds true for cyber activity: You must detect the adversaries as far “left of boom” as possible to stop them before they charge ahead along the kill chain to accomplish their mission — whether planting ransomware, stealing intellectual property, or even launching a destructive attack via system control.
How proactive can you get? It’s safe to say that if a threat is detected, it’s already on your network. What does this mean? Think of your house. Let’s say a robber wants to target a safe in your house. The first step is getting past the back door (i.e., the endpoint or firewall). Next, the robber has to find the safe, navigate your guard dog, avoid tripping over the toys your kids left — all these steps are behaviors, or tracks, the adversary follows to reach their objective (which also includes "compromising the safe and taking out the valuables”). Every one of these behaviors is an opportunity to catch the adversary in the act. Your goal is to catch them as early as possible before they steal your valuables.
The same is true of your network (the heart of your enterprise) if you want to stand a better chance of staving off system control or data exfiltration. Catch them at the network gate! Only behavior analytics powered by machine learning can detect early and accurately.
Now, given the bad guy is in your house, it’s up to you to decide what to do to get them out of your house. “Proving the positive” increases your level of proactivity, which is critical for mitigating the impact of a breach and cost to the business. As IBM reports in its 2021 Cost of a Data Breach Report, “Data breaches that took longer than 200 days to identify and contain cost on average $4.87 million, compared to $3.61 million for breaches that took less than 200 days.”
Use case: Detecting credential phishing using behavioral analytics
Let’s go back to the attack vector by which attackers can dwell the longest in the network: stolen or compromised credentials. What happens once the cyber criminals breach the network in this way? The first thing attackers do when they compromise the system is establish persistence in order to gain a foothold into the enterprise. From there, the adversary takes inventory and makes a strategic plan of attack. They list everything installed on the machines, start watching for patterns (e.g., when and how the machines are used), and, from there, blend in for months to scope out their strategic attack.
Being able to detect a credential phishing attack when it happens, therefore, is one way to curtail the business impact of the cyber threat — well before the adversary can set up camp in your network to scope out their endgame (that is, system control or data exfiltration). As part of a well-rounded cybersecurity stack that includes endpoint detection and response (EDR) and a next-gen firewall, an advanced network detection and response (NDR) tool uses behavioral analytics to detect anomalous activity on the network.
Here is a walkthrough of how a SOC analyst can use behavioral analytics to detect a credential phishing attack:
A mindshift to “proving the positive”
Adopting the mindset of continually “proving the positive” enables you to confirm whether your network has been breached and is currently under attack. In other words, why wouldn’t you approach a network attack assessment in much the same way as your annual doctor’s visit? You continually check your enterprise network to ensure a clean bill of health by making sure there are no threats lurking undetected within, like an unknown cancer.
A regular network attack assessment can either bring the underlying cyber threat to light, prompting rapid mitigation or, even better, provide peace of mind in knowing that your network is healthy. By continually “proving the positive,” you can improve your network’s ongoing bill of health. Putting off the health of your network, by contrast, can wreak havoc while taking a financial toll as well: the global average cost of a data breach now banks at $4.24 million. Not to mention the intangibles of business impact: damaged brand reputation and the loss of customer trust.
Since remote and hybrid work environments have become the new normal, thereby widening the attack surface, “proving the positive'' is more crucial than ever. Why? Because the average network dwell time has increased significantly since companies and organizers were forced to pivot quickly to such environments in 2020, giving adversaries more ways to get in. In fact, IBM Security reports that, “organizations that had more than 50% of their workforce working remotely took 58 days longer to identify and contain breaches than those with 50% or less working remotely.” And of course the cost of the breach went up — to the tune of $1.07 million higher.
Don’t be afraid of the cyber doctor
We get it: the fear of the “what ifs” and the unknowns often deters getting regular checkups. But the potential outcome of not knowing what’s lurking beneath the hood could be even worse. So get your cyber checkup … and prove to your executive and board stakeholders that your network is healthy.
.png)



