On May 7, Colonial Pipeline became yet another victim of a ransomware attack. According to Bloomberg, the attackers siphoned nearly 100GB of data from Colonial Pipeline's IT side of the house before locking some of its computers and servers, ultimately demanding an undisclosed ransom. The attackers threatened to leak the stolen data while locking the information they encrypted on computers inside the network unless Colonial paid the ransom.
Although it does not appear as if the operational network was affected, Colonial Pipeline proactively shut down its pipelines temporarily as a precautionary measure to prevent the infection from spreading to the operational network.
Ransomware is a known, ongoing nemesis that never goes out of style among highly organized cyber criminal groups, particularly in the education, healthcare, and banking sectors. The pandemic environment has made the situation even worse. During the height of COVID-19 lockdowns from February to April 2020, ransomware attacks increased nine-fold. In fact, the threat-sharing group for the financial sector, FS-ISAC, even titled its latest report “The Rise and Rise of Ransomware.”
On average, according to a study by the Unit 42 threat intel team at Palo Alto and Crypsis incidence response, ransomware operators demanded an average of $847,344 for each attack during 2020, and the average actual payment increased by 171% over 2019 figures. In the Colonial Pipeline case, the ransom amount was nearly $5 million.
Detecting ransomware attacks
So, how can security analysts spot hackers early in the network intrusion cycle and before they reach the ransom demand stage?
The answer: By looking for anomalies on the network as adversaries are scoping out vulnerabilities. Behavioral analytics provide the magnifying glass that’s been missing in the cybersecurity space until the advent of machine learning. Now, analytics can detect unknown, or “zero day,” threats on networks without losing months waiting for known indicators of compromise.
IronNet uses behavioral analytics that are capable of detecting malware that paves the way for the payload demand by identifying adversarial tactics, techniques, and procedures (TTP) that appear as anomalies on networks. At present, the TTPs exhibited by the DarkSide group in this particular incident have not been confirmed.
IronNet’s network detection and response (NDR) platform, IronDefense, is able to track and trace ransomware campaigns as they progress along the cyber kill chain in the victim organization. IronNet precipitates various alerts associated with the attacker’s malicious activities, representing opportunities for the victimized organization to provide a swift and effective response to neutralize the threat.
Community analysis indicates that DarkSide itself does not deploy ransomware until they've enumerated the target environment and privileged accounts, exfiltrated sensitive data, and identified all backup systems, servers, and applications. What does such a campaign look like?
Using IronNet's behavioral analytics to detect ransomware
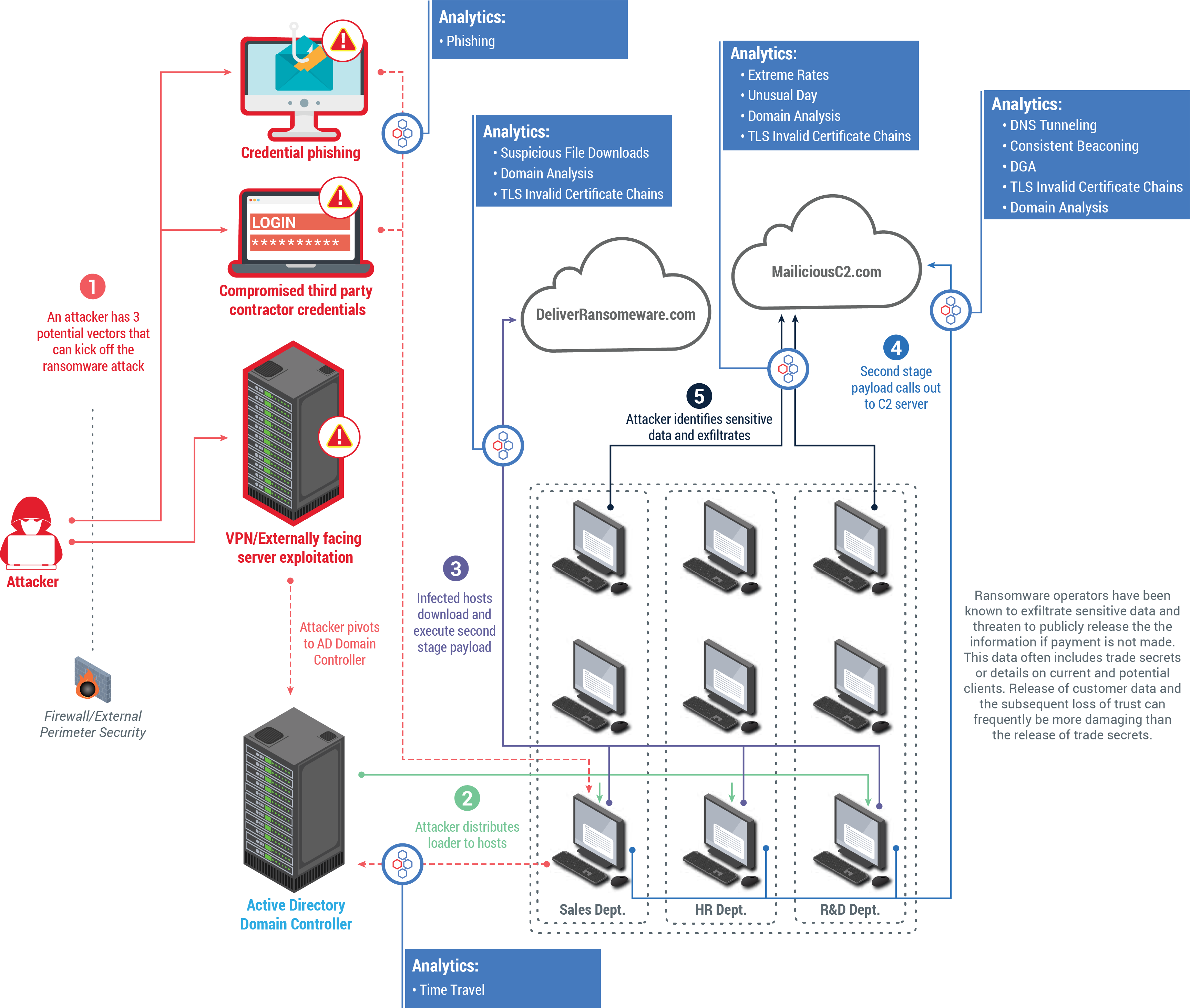
In the above illustration, based on the TTPs observed in this attack, IronNet's behavioral analytics would have detected several connections to primary backup repositories using compromised service accounts shortly before encryption. The DarkSide group infiltrates networks quietly in order to achieve the biggest bang for its nefarious buck during the noisier encryption phase of the attack. Behavioral analytics detect anomalies early in the intrusion cycle, during network dwell time, to halt this type of progression.
IronNet threat research team tackles ransomware
IronNet’s Threat Research team is committed to discovering new characteristics that can aid in the detection and prevention of these destructive attacks. With this in mind, they conducted experiments using lab detonation of publicly available ransomware variants to find commonalities among metadata and artifacts. You can read more about this study in "Ransomware's Malevolent Heyday" and "Detecting ransomware: three research-based recommendations."
.png)

