Key points from our research:
- Around early-mid August, we noticed an increase in MacOS malware detections, specifically AdLoad and UpdateAgent in IronDome, in the education sector. This timing correlates with students returning to school, therefore bringing their personal (infected) devices to school networks, and is likely the cause of this increase.
- Our CyOC discovered previously unreported IOCs relating to AdLoad and UpdateAgent, including HTTP User Agents, HTTP Paths, and domains. Additionally, some IOCs discovered have been reported since 2019, which indicates the techniques the threat actors are using have been around for years and continue to compromise systems. These IOCs are available in the Appendix section.
- IronDefense was able to detect this activity via multiple different analytics, including our Suspicious File Download, Beaconing, and Domain Analysis behavioral analytics. IronDome correlated this activity together and uncovered five more enterprises affected.
Executive Summary
IronNet has observed an increase in MacOS malware within IronDome’s Education sector over the past couple of weeks. Our Cyber Operations Center’s (CyOC) investigations into these incidents found these infections were originating from already-infected personal devices that were brought into education networks, with the majority of these occurring at higher education institutions. The most prevalent malware strains we have observed include AdLoad, a package bundler that downloads additional payloads, and UpdateAgent, a trojan that we observed stealing basic system information.
This surge in MacOS malware detections aligns with students returning to school - which also contributes to our analysis that the systems these detections originated from are personal devices. This serves as a reminder that Bring Your Own Device (BYOD) policies are of the utmost importance, especially that any BYOD devices should not be inherently trusted and should be segregated from internal enterprise resources.
AdLoad/UpdateAgent
Overview
Beginning August 18th, 2023, IronDefense detected activity based on the Suricata rule ET MALWARE MacOS/Adload CnC Beacon. Upon initial investigation, IronNet threat hunters identified additional activity that varied from previously reported AdLoad IoCs. We observed a previously unreported C2 communications and a new subdomain pattern used for secondary downloads, static.<two-word-domain>.com.
Malware Command and Control (C2) Behavior:
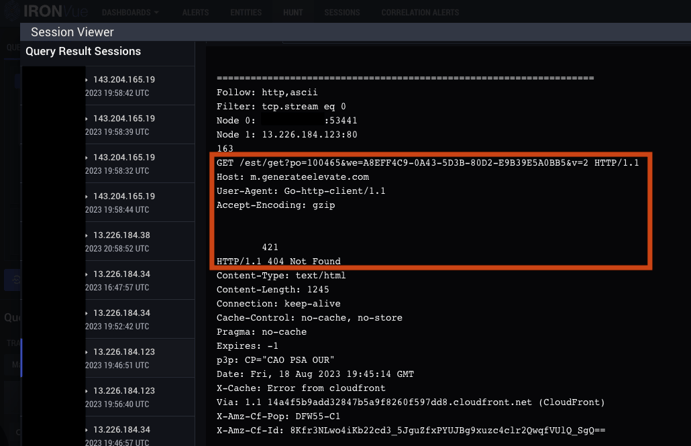
1. The victim host conducts HTTP GET requests to a C2 domain with two device unique variables, a 6 digit number and UUID string. These requests have user agent strings of either Go-http-client or curl, and result in an HTTP 404 response.
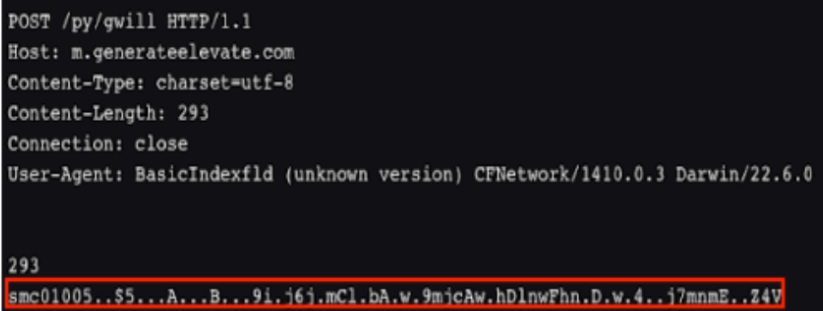
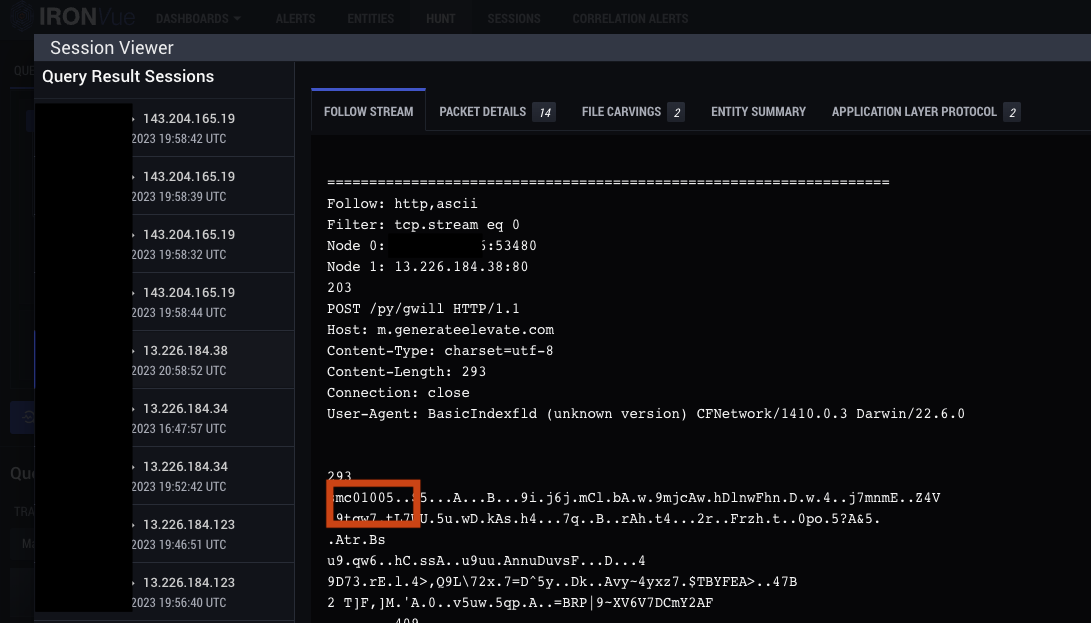
2. C2 activity begins via HTTP POST consistent with previously reported AdLoad C2 communications. The string smc is found at the start of the data portion of the POST request, followed by encrypted data.
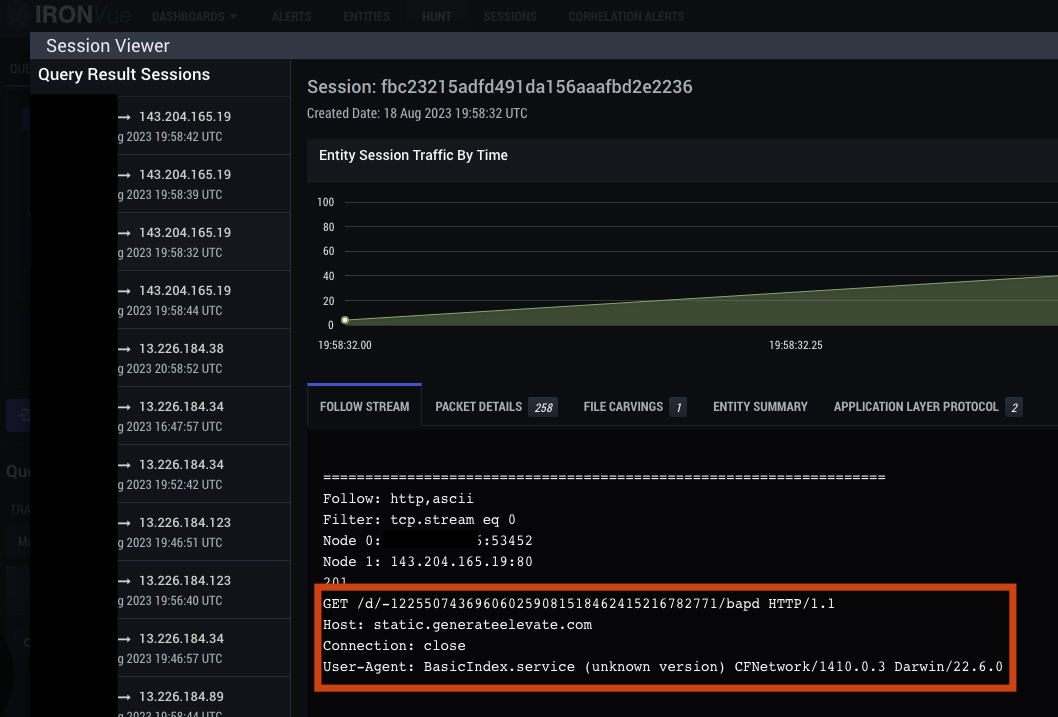
3. An additional payload is downloaded from static.<domain>/d/<38 digit string>/<filename>, which contains a password-protected zip file. At the time of writing, IronNet has been unable to access the contents of this zip file.
4. C2 activity continues, however the user agent changes to the name of the file found within the encrypted zip archives.
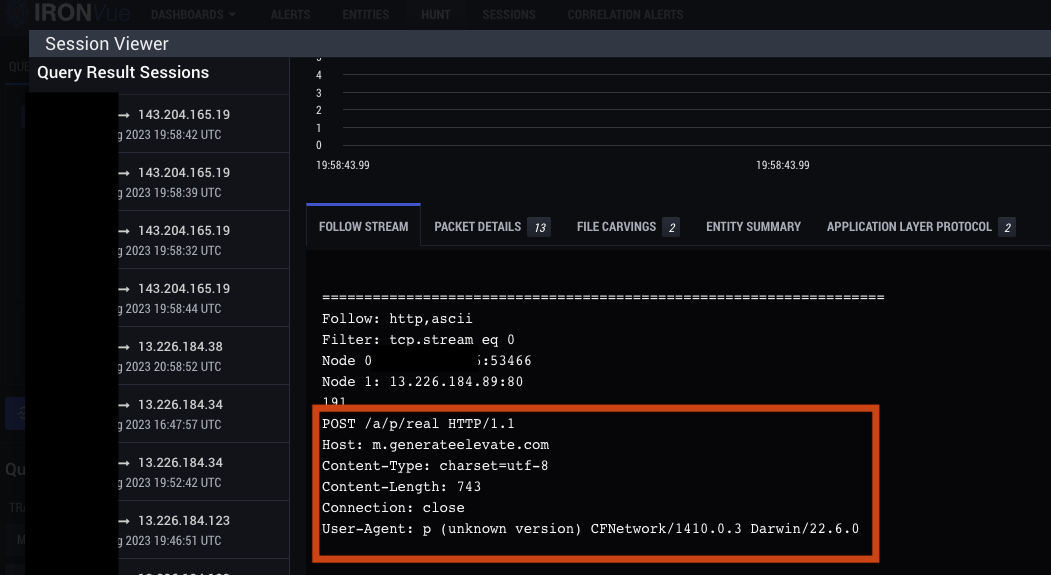
5. Additional HTTP GET requests to a C2 domain are observed using the same variables as the initial activity, however with different HTTP Path values. These sessions also result in an HTTP 404 response.
6. Additional payloads are downloaded using the same format, and the C2/Download cycle repeats.
UpdateAgent
Additionally, encrypted communications over TCP port 1027 were observed to qolveevgclr.activedirec[.]com and b.digitalgrounds[.]info. The domain qolveevgclr.activedirec[.]com was reported as a C2 domain for UpdateAgent in a Microsoft blog post from 2022, where Microsoft identified AdLoad as a secondary payload delivered by UpdateAgent. Since the systems we observed were compromised prior to joining the network, we are unable to confirm the sequence of events relating to UpdateAgent potentially dropping AdLoad as a secondary payload. While APT's and ransomware actors who target businesses and large organizations have realized the need to regularly cycle their infrastructure (domains and IP’s), threat actors targeting individuals have not needed to do this to remain effective.
Additional Observations
Overview
IronNet detected suspicious activity across the same education customer environments that, while sharing some similarities, does not appear to be related to UpdateAgent/AdLoad. We observed encrypted C2 communications to various domains, and additional payload downloads from zip archives. The first downloaded zip contained an unknown Mach-O binary that had no negative reputation in VirusTotal, while the second contained Genieo adware, a MacOS browser hijacker. The Genieo binary was being hosted on a C2 domain that the infected devices were communicating with. Like the UpdateAgent/AdLoad activity, IronNet Threat Hunters were unable to identify the initial infection source due to the devices being compromised prior to joining the network.
Malware C2 Behavior:
1. The victim host begins C2 activity via an HTTP POST to <domain>/reader-update, which contains a device_id= parameter unique to the host.
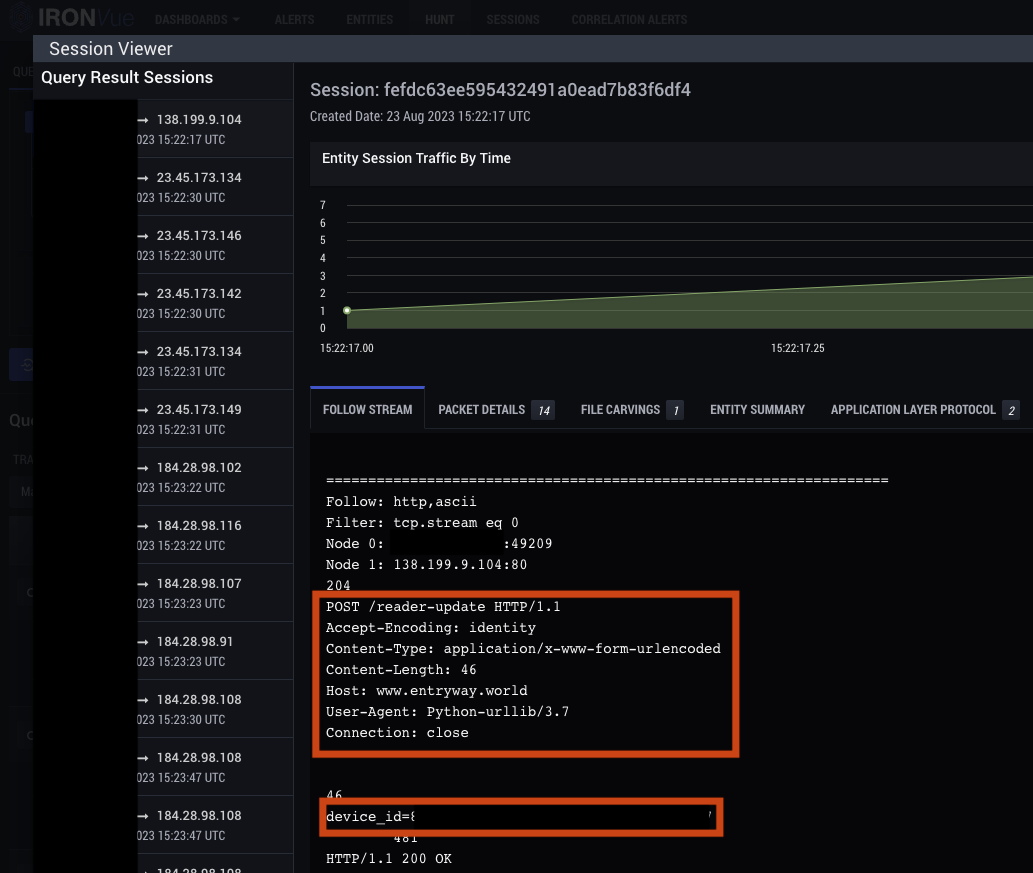
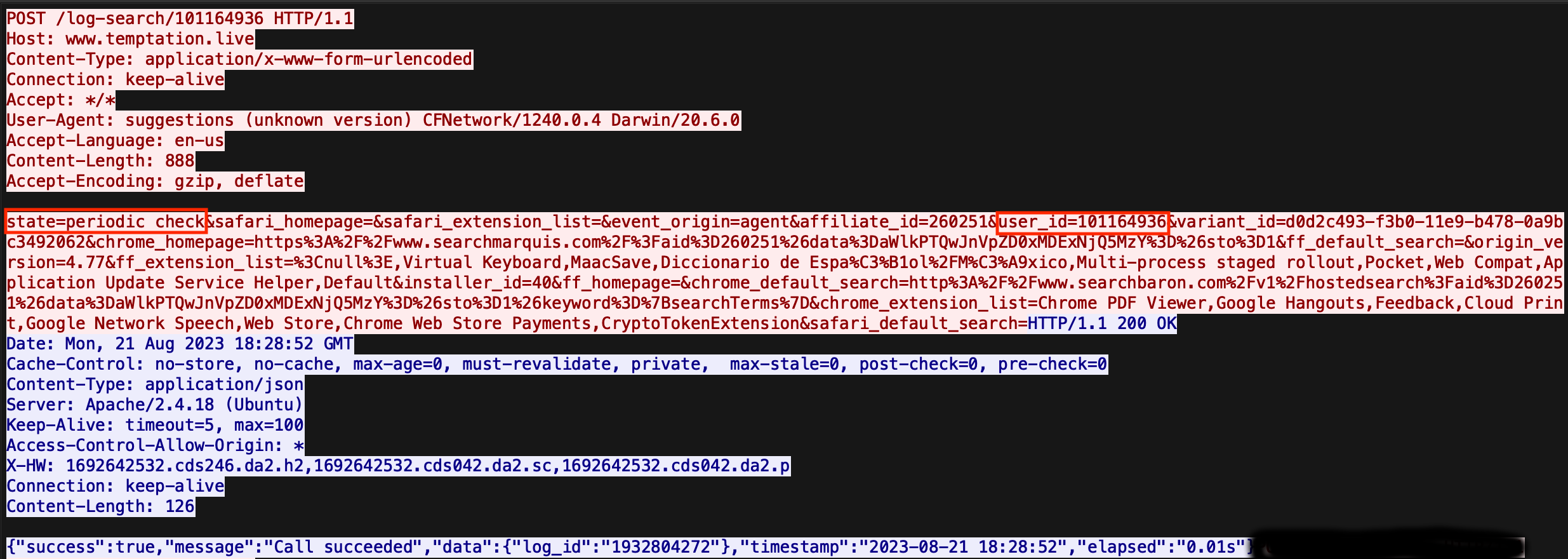
2. Follow-on HTTP POST activity is observed to /<one word>-search/<9 digit identifier> with additional host information, including: unique host identifiers, references to two domains associated with browser hijackers, and various Chrome extension names. This activity contains a state= parameter which in this case was set to periodic check.
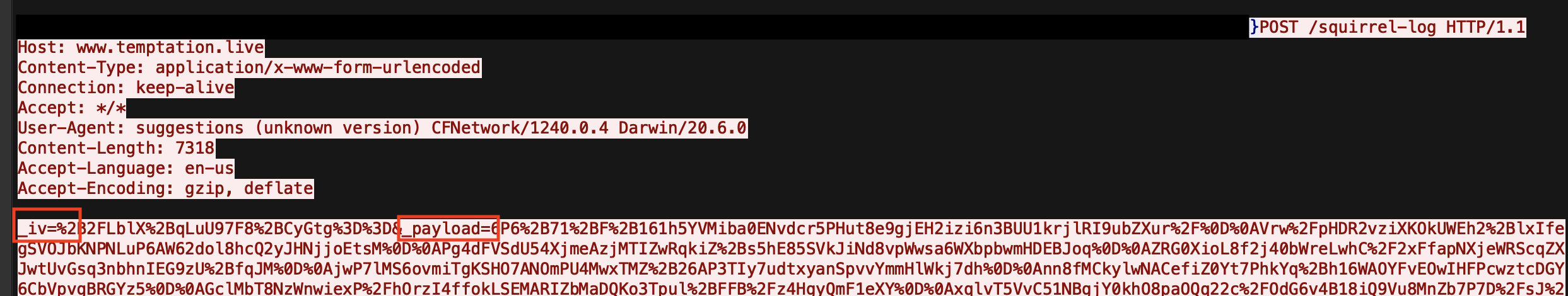
3. C2 activity begins to /squirrel-log with an encrypted data string that contains two parameters: _iv= and _payload=. The C2 server responded with an acknowledgement.
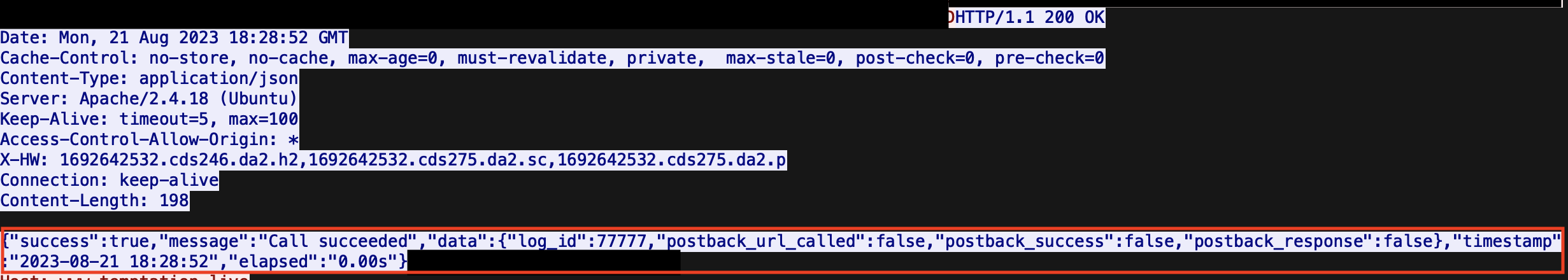
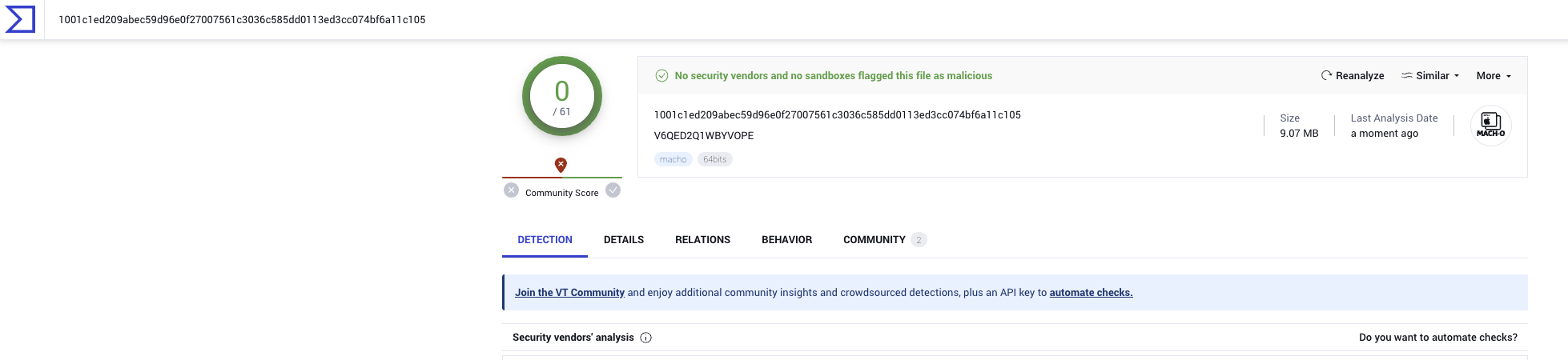
4. An HTTP request to <domain>/static/apps/<name>.zip is observed. In this session, 437.zip was downloaded, which contained a Mach-O binary named V6QED2Q1WBYVOPE. Interestingly, this has no negative ratings or reports in VirusTotal and attempts to execute the binary in sandboxes were unsuccessful at identifying what this file is.
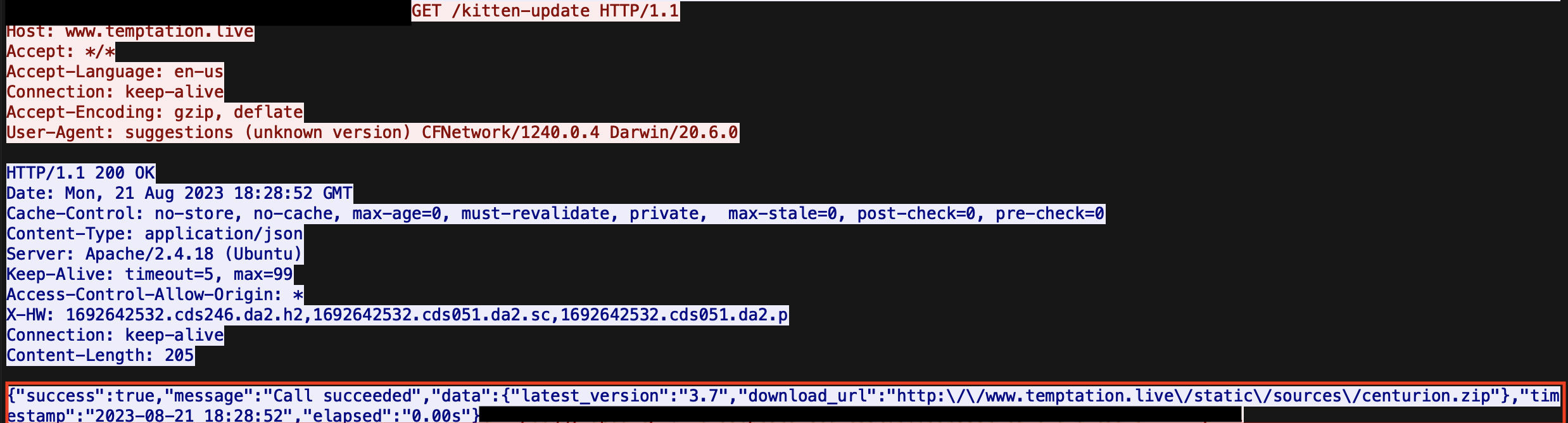
5. A C2 session to <domain>/kitten-update where additional download instructions are sent to the victim host.
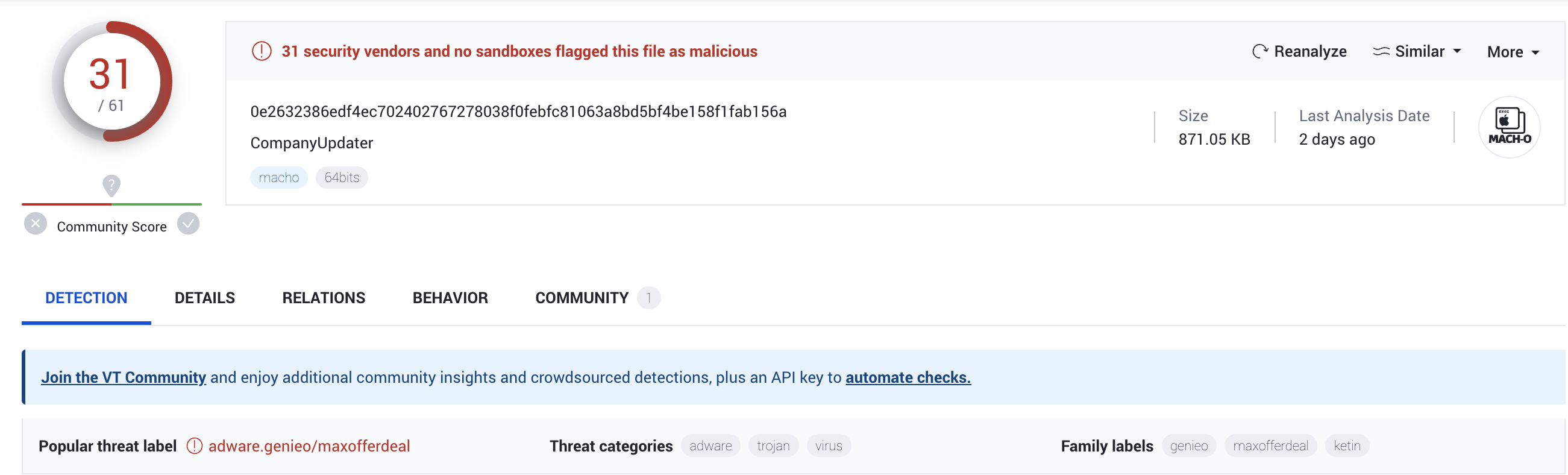
6. An additional payload is downloaded per the C2 download instructions. In the activity outlined, this downloaded a zip file centurion.zip, which contained the file CompanyUpdate. After uploading to VirusTotal, it was identified as Genieo adware.
7. C2 activity resumes with a request to /doggy-update/<9 digit identifier>/<40 digit string>, which returns a failed response from the C2 server.
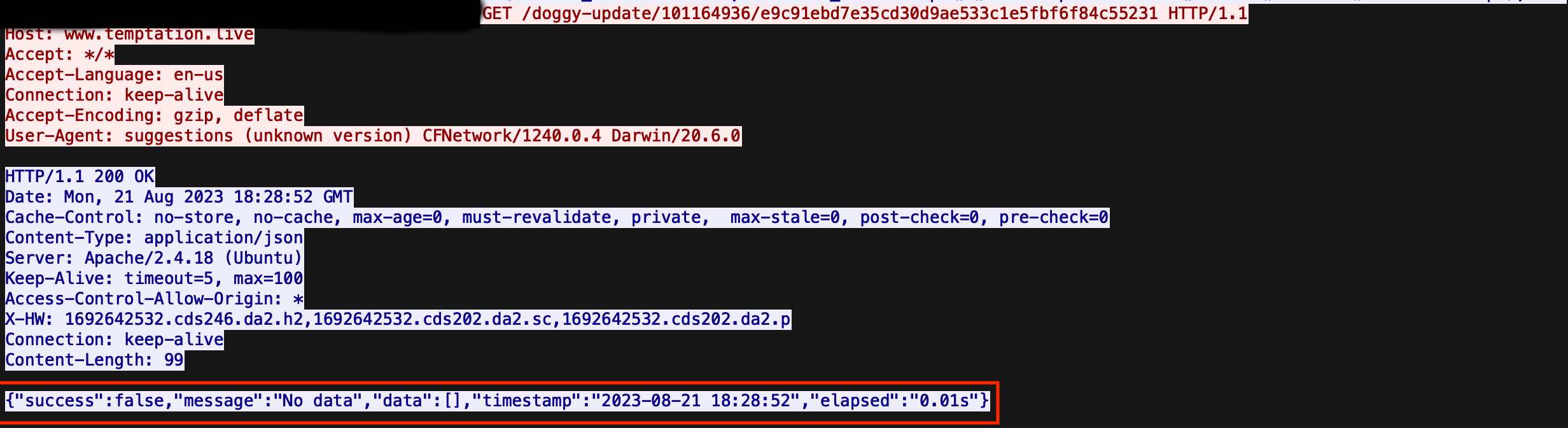
IronDome Correlations
We rated all alerts associated with these campaigns as malicious, and when this happens, IronDome creates Threat Intelligence Rules for the IOCs associated with the activity and pushes those rules to all IronDefense instances, as well as comments that the analyst adds to provide context to other analysts triaging this same activity. These Threat Intelligence Rules uncovered additional activity in other IronDome participants which prompted additional investigations, and enabled us to discover the uptick in MacOS malware detections within the Education sector.
IronDome correlated this activity within six enterprises, three behavioral analytics, and also the Suricata rule ET MALWARE MacOS/Adload CnC Beacon. To give an idea of what this looks like for IronNet analysts and threat hunters, below is an example of one of the domains in our Indicator Intelligence page within our Collective Defense Portal (CDP):
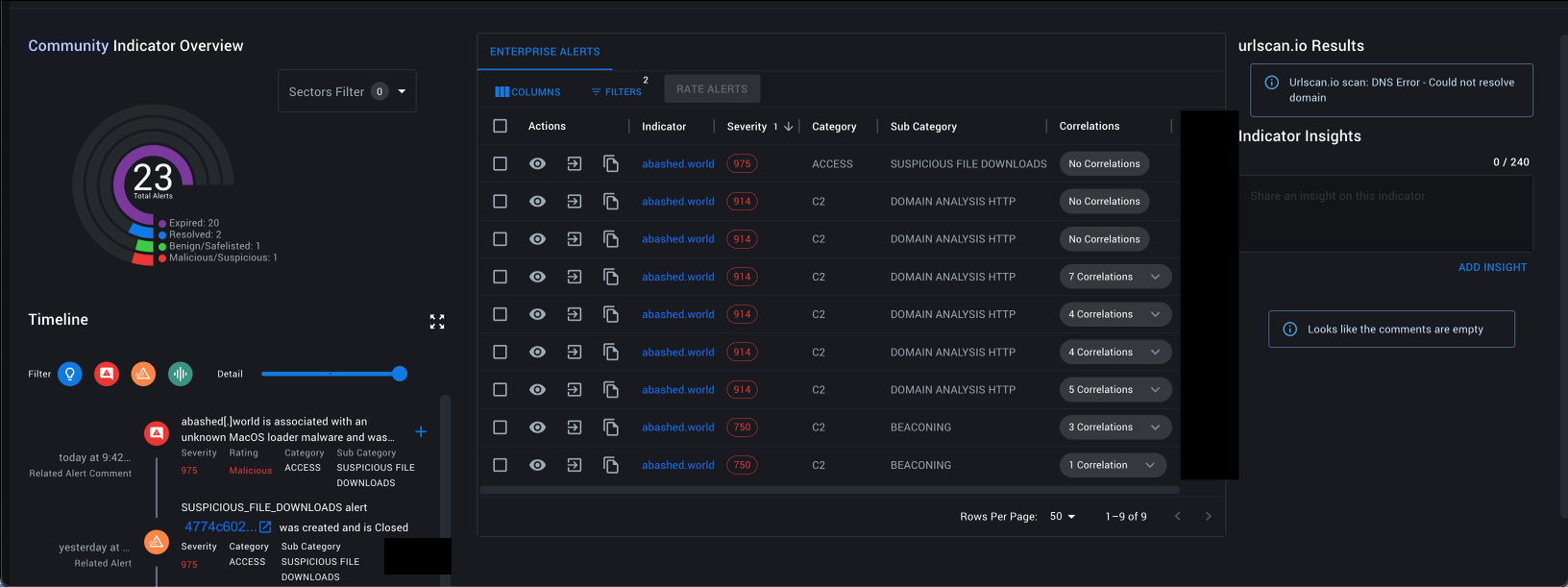
Displayed above, IronDefense generated three unique alert subcategories for this activity, including Suspicious File Download, Beaconing, and Domain Analysis HTTP. This immediately provides additional context to the analyst about this activity, informing them of the behaviors that are occurring and helping them prioritize what and how to triage. Additionally, albeit being sanitized in the screenshot, we are able to quickly determine all of the IronDefense instances affected, as well as see comments about the behaviors.
Summary
BYOD brings inherent risks to an enterprise, especially when considering the devices are untrusted and can be infected with malware prior to connecting to an enterprise network. Given this, it is imperative to have strict BYOD policies and technical controls, such as network segmentation, to limit the risk that BYOD presents to your network. Adversaries continue to target personal devices as a means to either gain access to loosely secured networks or to gain enterprise credentials or information stored on personal devices.
The IronDome platform was able to correlate three unique behaviors across the Education sector, which enabled us to prioritize and investigate this activity further. This led to our analysts uncovering this trend of previously-compromised devices being detected on Education networks, which closely aligns with the timing of students returning to school.
Detections
|
Behavior |
MITRE ATT&CK |
Details |
|
AdLoad - ZIP file downloads from unknown domains |
T1071.001 |
HTTP URL: Subdomain of static, with a path of: /d/<38chars>/<extensionless file> Example: static.generateelevate[.]com/d/-122550743696060259081518462415216782771/bapd |
| AdLoad - HTTP POST with the data portion starting with smc, followed by encrypted data | T1071.001 |
Subdomain of 1 character, with the data portion starting with smc, followed by encrypted data Example: m.generateelevate[.]com
|
| AdLoad/UpdateAgent - Encrypted Comms over non-stand port (port 1027 was observed) | T1571 | qolveevgclr.activedirec[.]com b.digitalgrounds[.]info |
| Unknown - HTTP POST to path /squirrel-log with suspicious HTTP user agent | T1071.001 |
HTTP URL: www.temptation[.]live/squirrel-log with a user agent string of suggestions (unknown version) CFNetwork/1240.0.4 Darwin/20.6.0 The suggestions part of the user agent does change, some others seen are TheSkyXStudentEdition, VFXMT4MacLion, and PhotoMetaEdit |
| Unknown - HTTP POST to path /<oneword>-<oneword> | T1071.001 |
HTTP Path examples:
|
|
Suricata Rule |
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET MALWARE MacOS/Adload CnC Beacon"; flow:established,to_server; http.method; content:"POST"; http.uri; content:"/a/rep"; bsize:6; fast_pattern; http.host; content:"m."; startswith; http.user_agent; content:"|20 28|unknown|20|version|29 20|CFNetwork|2f|"; http.content_type; content:"charset=utf-8"; bsize:13; http.request_body; content:"smc"; startswith; content:"$"; distance:7; within:1; isdataat:200,relative; threshold:type limit,count 1,seconds 600,track by_dst; reference:url,cybersecurity.att.com/blogs/labs-research/mac-systems-turned-into-proxy-exit-nodes-by-adload; classtype:trojan-activity; sid:2047628; rev:1; metadata:affected_product Mac_OSX,attack_target Client_Endpoint,created_at 2023_08_11,deployment Perimeter,former_category MALWARE,malware_family Adload,signature_severity Major,updated_at 2023_08_11;) | |
Appendix (IOCs)
Domains:
|
Domains |
MITRE ATT&CK |
Notes |
|
m.generateelevate[.]com |
T1071.001 |
C2 - AdLoad |
|
latestandtest[.]info |
T1071.001 |
C2 - AdLoad |
|
m.standartboost[.]com |
T1071.001 |
C2 - AdLoad |
|
static.standartboost[.]com |
T1071.001 |
Download/C2 - AdLoad |
|
static.generateelevate[.]com |
T1071.001 |
Download/C2 - AdLoad |
|
qolveevgclr.activedirec[.]com |
T1071.001, T1571 |
C2 - UpdateAgent |
|
b.digitalgrounds[.]info |
T1071.001, T1571 |
C2 - UpdateAgent |
|
www.temptation.live |
T1071.001, T1041 |
Download/C2 - Unknown |
|
www.aww799[.]com |
T1071.001, T1041 |
Download/C2 - Unknown |
|
www.abashed[.]world |
T1071.001, T1041 |
Download/C2 - Unknown |
|
gettime[.]world |
T1071.001 |
C2 - Unknown |
|
www.entryway[.]world |
T1071.001 |
C2 - Unknown |
|
www.tense[.]world |
T1071.001 |
C2 - Unknown |
|
www.bleed[.]world |
T1071.001 |
C2 - Unknown |
|
www.maddening[.]world |
T1071.001 |
C2 - Unknown |
|
www.hanging[.]world |
T1071.001 |
C2 - Unknown |
|
www.obstruct[.]world |
T1071.001 |
C2 - Unknown |
|
www.behave[.]world |
T1071.001 |
C2 - Unknown |
|
www.goofy[.]world |
T1071.001 |
C2 - Unknown |
|
www.bleed[.]world |
T1071.001 |
C2 - Unknown |
UserAgents:
Note: User Agent strings can easily be modified, therefore these indicators should be viewed as potentially suspicious, rather than known malicious.
|
HTTP User Agent |
Description |
|
BasicIndexfld (unknown version) CFNetwork/1410.0.3 Darwin/22.6.0 |
C2 - AdLoad |
|
BasicIndex.service (unknown version) CFNetwork/1410.0.3 Darwin/22.6.0 |
C2 - AdLoad |
|
StandardBoost.system (unknown version) CFNetwork/1128.0.1 Darwin/19.6.0 (x86_64) |
C2 - AdLoad |
|
p (unknown version) CFNetwork/1410.0.3 Darwin/22.6.0 |
C2 - Unknown |
|
14694811275077026145 (unknown version) CFNetwork/1410.0.3 Darwin/22.6.0 |
C2 - Unknown |
|
.62F6F5BF-9B85-405E-B519-B0944DA64AB1 (unknown version) CFNetwork/1410.0.3 Darwin/22.6.0 |
C2 - Unknown |
|
a (unknown version) CFNetwork/1128.0.1 Darwin/19.6.0 (x86_64) |
C2 - Unknown |
|
AlienSkinBokeh2 (unknown version) CFNetwork/811.5.4 Darwin/16.7.0 (x86_64) |
C2 - Unknown |
|
systemmond (unknown version) CFNetwork/1410.0.3 Darwin/22.6.0 |
C2 - Unknown |
|
OSXUpdate (unknown version) CFNetwork/811.5.4 Darwin/16.7.0 (x86_64) |
C2 - Unknown |
|
PhotoMetaEdit (unknown version) CFNetwork/811.5.4 Darwin/16.7.0 (x86_64) |
C2 - Unknown |
|
iCEPS (unknown version) CFNetwork/811.5.4 Darwin/16.7.0 (x86_64) |
C2 - Unknown |
|
TheSkyXStudentEdition (unknown version) CFNetwork/1240.0.4 Darwin/20.6.0 |
C2 - Unknown |
|
scd (unknown version) CFNetwork/1128.0.1 Darwin/19.6.0 (x86_64) |
C2 - Unknown |
|
SolitaireGameHalloweenFree (unknown version) CFNetwork/1128.0.1 Darwin/19.6.0 (x86_64) |
C2 - Unknown |
|
suggestions (unknown version) CFNetwork/1240.0.4 Darwin/20.6.0 |
C2 - Unknown |
|
chitchat (unknown version) CFNetwork/1128.0.1 Darwin/19.6.0 (x86_64) |
C2 - Unknown |
Files:
|
SHA256 |
Filename |
Filetype |
File Link (URLscan.io) |
|
1001c1ed209abec59d96e0f27007561c3036c585dd0113ed3cc074bf6a11c105 |
V6QED2Q1WBYVOPE |
Mach-O |
|
|
0e2632386edf4ec702402767278038f0febfc81063a8bd5bf4be158f1fab156a |
companyupdater |
Mach-O |
|
|
ab6116a1be4107fb626e8283cd598a507216db1550edb70b980317f10534a27d |
p |
ZIP Archive |
|
|
b0572238639a68c81d4730549898a4ce5dd8584cee247aa046f2f4e9820c7593 |
p |
ZIP Archive |
|
|
f5fb68acbaecb3791c36de85dcd1e9f314ce48039a3afabe5613957ff9098ec6 |
ra |
ZIP Archive |
|
|
dae3d0988dd4e376671fddc7f44f604403654f867484f5613a5900ce391e3010 |
ra |
ZIP Archive |
|
|
dda75a6faa851b02053a0d5b55ff48027fe53942c9f37958bd64d8a1d0bffe6b |
a |
ZIP Archive |
|
|
2c81813b1fec1dc0544d51b373d7bff6f222170798079249e3845f73e908c0d2 |
crx |
ZIP Archive |
.png)