
Key Points
- IronNet’s detections during the Black Hat Europe conference revealed not only several active malware infections – such as the Arechclient2 info-stealer – but also exposed a series of poor security practices by attendees that could have led to severe follow-on compromises in both the Black Hat network and their respective enterprises.
- IronNet’s detection of an insecure Chrome extension with suspicious exfiltration activity in the Black Hat network led to the identification of the same activity across nine different enterprises in the U.S., Asia, and the Middle East through our Collective Defense platform IronDome.
- As IronNet enters its third year as a partner in the Black Hat NOC, we continue to fill the critical role of providing network visibility for troubleshooting and hygiene in addition to lending detection and threat hunting capabilities.
In early December, we wrapped up another year of defending the Network Operations Center (NOC) at the Black Hat Europe cybersecurity conference. Our NOC threat hunters – Blake Cahen, Peter Rydzynski, and Jeremy Miller – assisted partner companies Palo Alto, Cisco, Meraki, Gigamon, and Netwitness in defending the Black Hat environment. This includes threats both external and internal, with a major focus being the security of the Black Hat infrastructure and the attendees’ devices. From a Network Detection and Response (NDR) perspective, helping identify potential malware on attendees devices has been one of the highlights of our contribution.
Detections in the Black Hat Europe Network
Arechclient2
 Arechclient2 alert detection
Arechclient2 alert detection
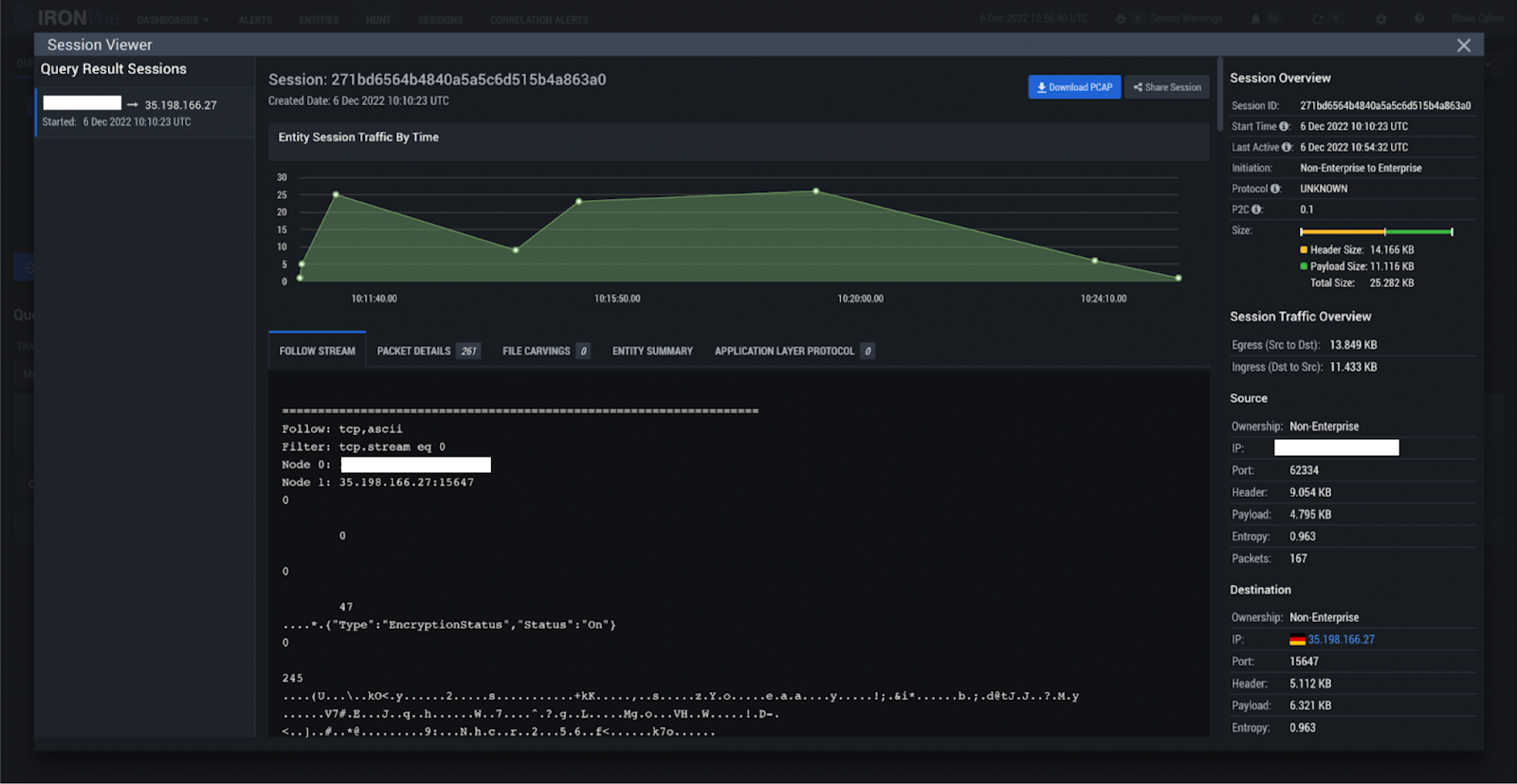
On the first day of the conference, IronNet hunters observed a user connecting to the network with a device that was already infected with Arechclient2 info-stealer malware. Within 10 seconds of joining the conference wifi, the infected device began calling out to the attacker-controlled command-and-control (C2) infrastructure and continued to do so until the user disconnected from the Black Hat network for the evening. The activity then resumed once the attendee arrived and reconnected to the wifi on the morning of the 2nd day, which is when we were able to confirm the infection, and the conference administrators reached out to the user to assist in cleaning up their device.
Arechclient2 (aka SectopRAT) is a .NET remote access trojan (RAT) with numerous functionalities, such as stealing browser and crypto-wallet information, launching a hidden secondary desktop to control browser sessions, and profiling compromised systems. It also has a number of anti-VM and anti-emulator capabilities, and it has been compared to the well-known RedLineStealer.
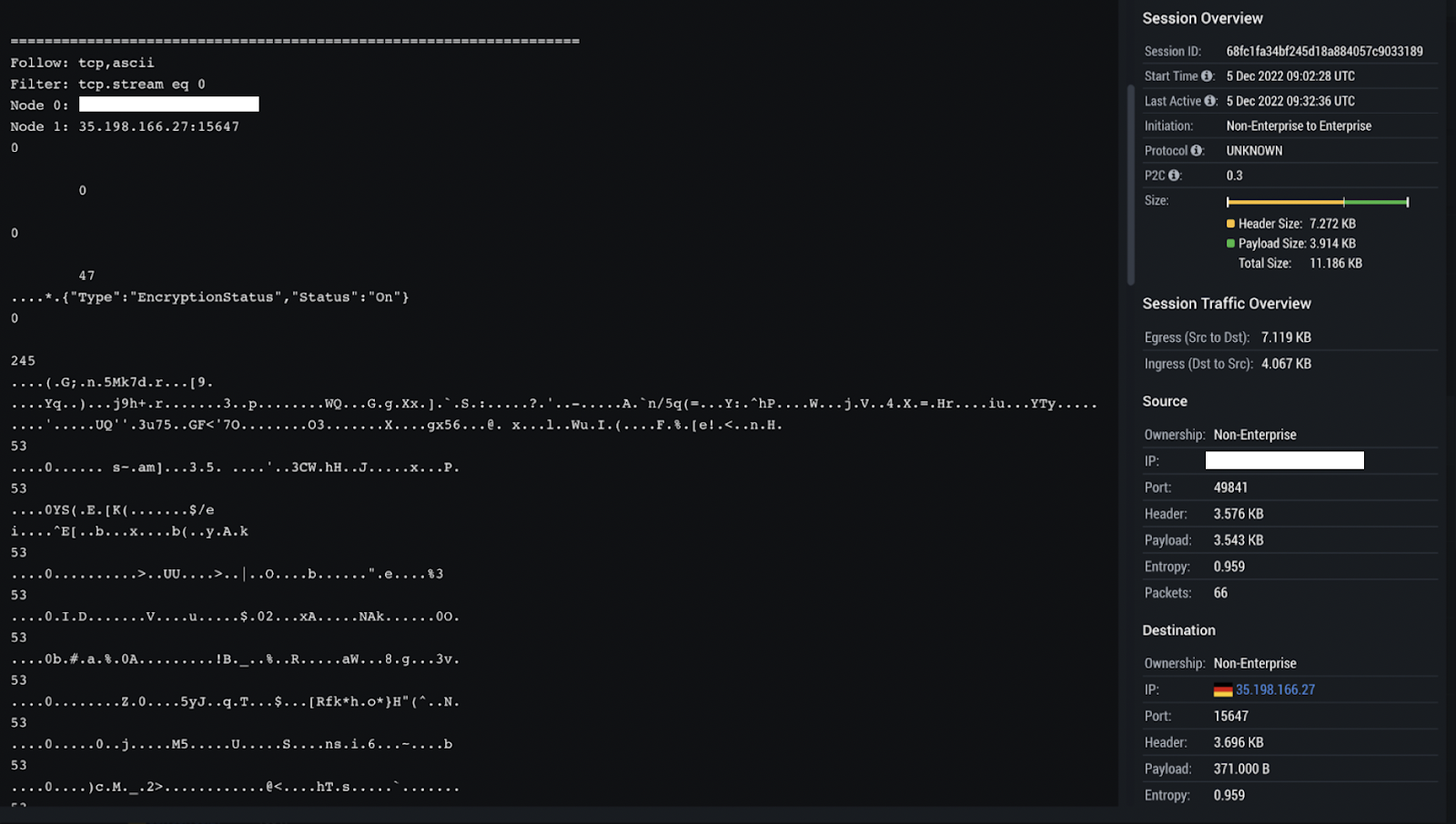
IronNet’s confidence that this was Arechclient2 activity centered on the initialization string “{"Type":"EncryptionStatus","Status":"On"}”, which served as an indication the encryption status for the malware activity was toggled to “on” in the compromise we observed. For this reason, the communications with the server were encrypted, making it impossible for our threat hunters to determine what data was exfiltrated. Despite this, we were able to determine the destination IP (35.198.166[.]27) was indeed malicious and that the observed activity was closely associated with the documented activity of the Arechclient2 malware family.
 IronNet PCAP sample of Arechclient2 encryption flag
IronNet PCAP sample of Arechclient2 encryption flag
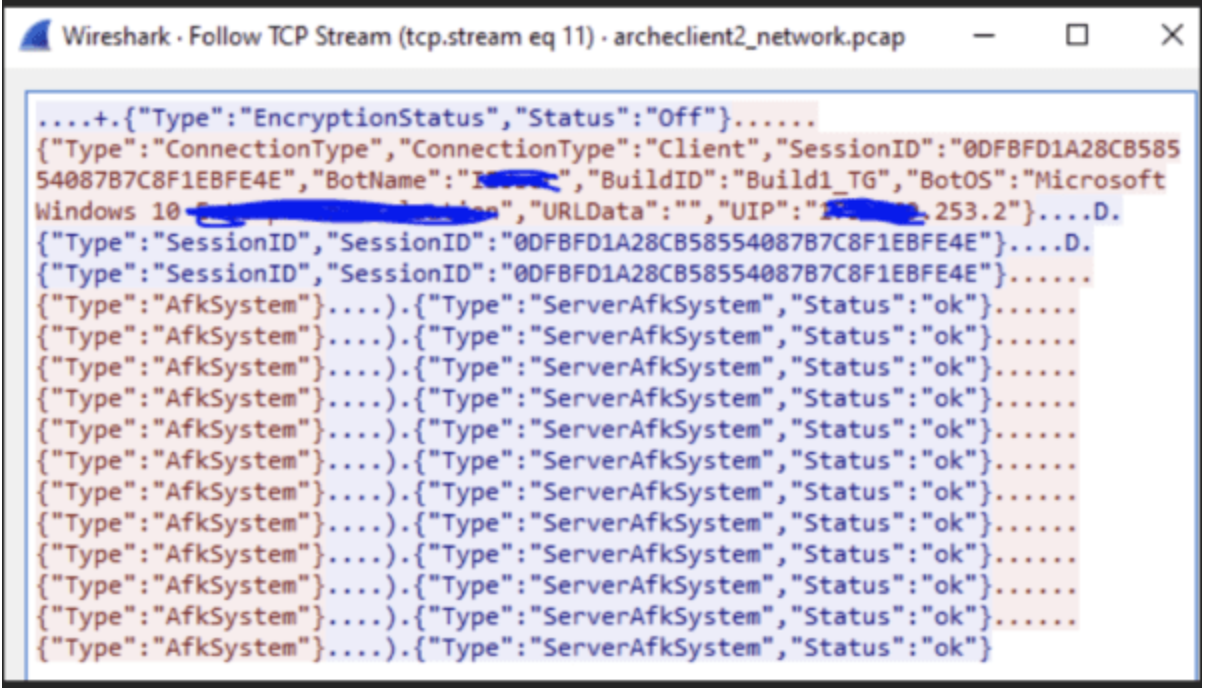
For example, research published by Tampa Bay Tech on Arechclient2 last month also references the use of the encryption status flag, except their observed sample had the encryption status disabled (“{"Type":"EncryptionStatus","Status":"Off"}”). We also observed outbound C2 communications to Google Cloud hosts on port 15647, which aligns with Arechclient2’s historical TTPs and further confirms the presence of this malware on the user system.
 PCAP sample of Arechclient2 encryption flag from Tampa Bay Tech
PCAP sample of Arechclient2 encryption flag from Tampa Bay Tech
FBDown Chrome Browser Extension
 FBDown exfiltration alert detection
FBDown exfiltration alert detection
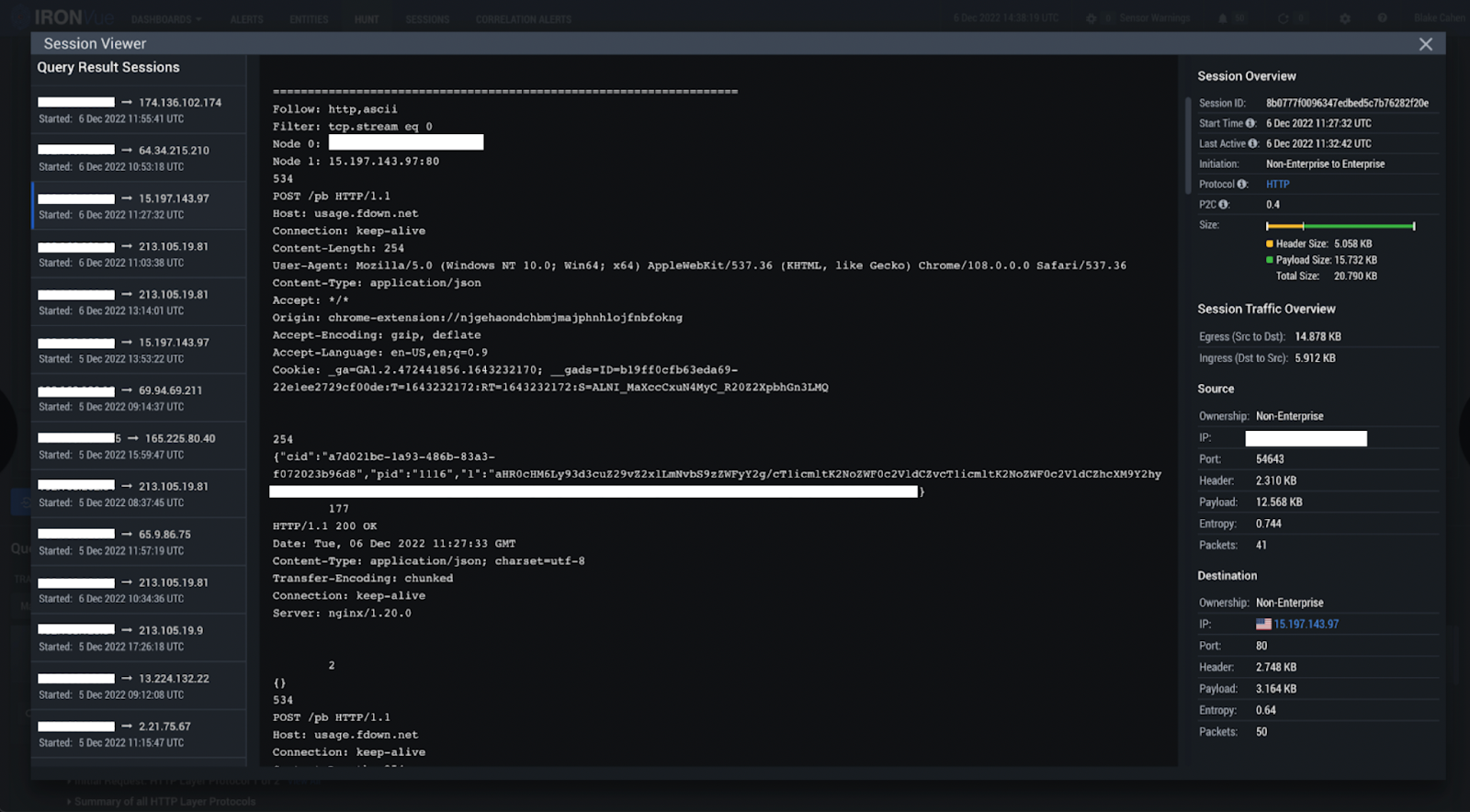
During the conference, we also observed a case of unusual exfiltration by a seemingly benign browser extension.
A user had a previously installed a Chrome Extension called FBDown (Facebook Video Downloader/Video Downloader Pro) on their laptop, which we observed exfiltrating all domains and URI’s the user submitted within Chrome and sending it via a base64 encoded HTTP POST request to the external server owned by the extension (usage.fdown[.]net/pb). In other words, the FBDown extension was collecting all of the user’s browser activity and history – which, safe to say, is far out of the scope of the extension’s intended and publicized functions.
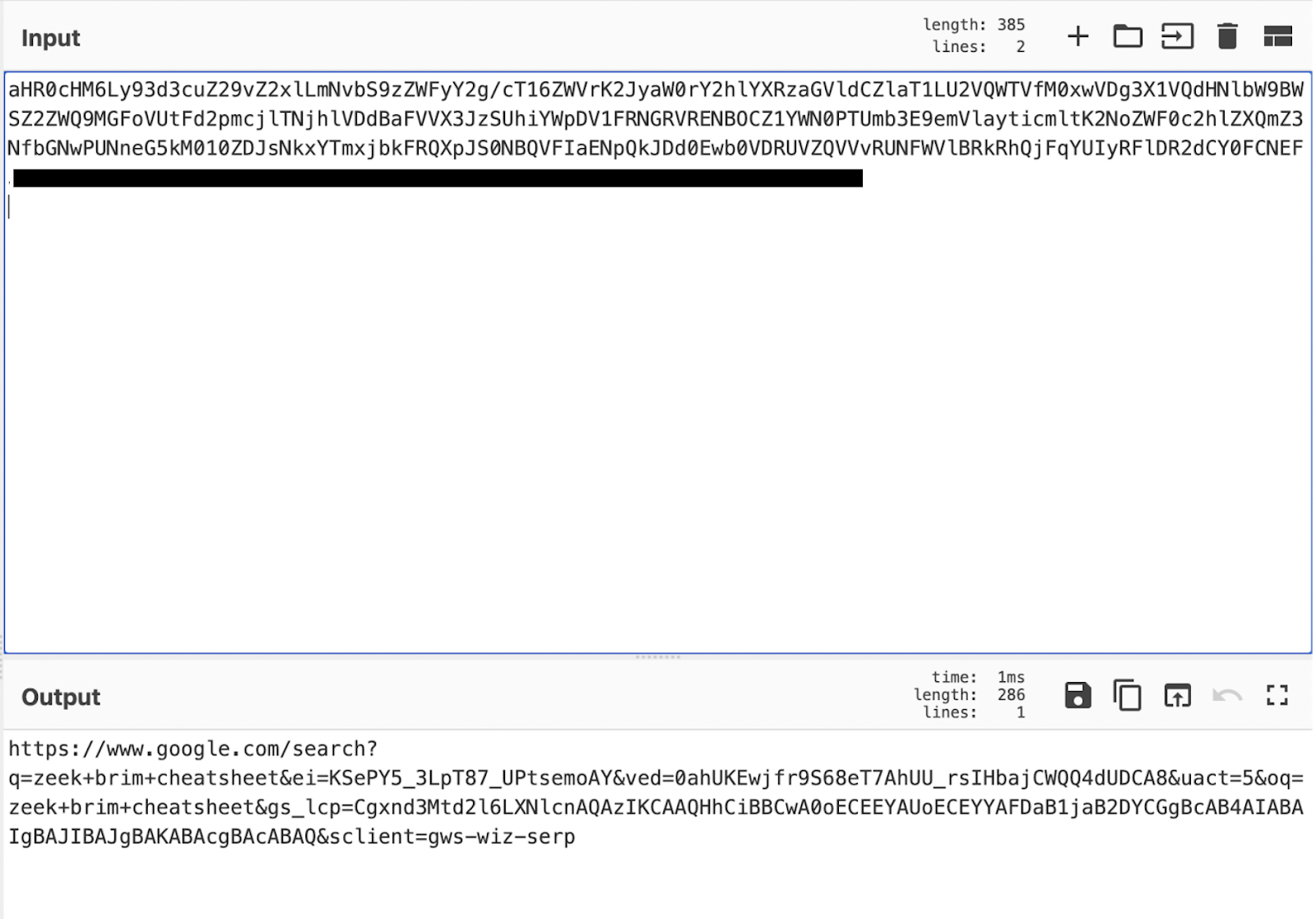 Decoded Base64 data sent to FBDown servers
Decoded Base64 data sent to FBDown servers
It’s important to note that there is no evidence FBDown is malicious in itself, but it does pose a significant security risk to anyone who has it installed. This is because it steals and collects every URL a user submits, including their search engine history – which can especially pose a problem for users in countries with more restrictive censorship laws. These URLs can also contain password reset tokens or even usernames and/or passwords in the paths.
Our concern here was not only the collection of the browser activity by FBDown, but also the risk of the extension itself being targeted by a threat actor aiming to use it as an access point to the information of all users who have it installed. It’s even possible someone could try to purchase the extension from the original developer knowing the treasure trove of data it contains. There are several reasons why an individual would not want their browser activity sent to an external destination – especially not in the clear. If a user is on public wifi and a threat actor thought to look for this, they could easily listen and collect the information themselves as the user’s computer transmits all of its browser activity to the extension’s server.
Correlating Black Hat NOC detections in IronDome
Following this observation, we rated the alert as malicious, which automatically pushed the related details to all organizations under IronNet’s Collective Defense platform IronDome. As a result, the IronDome platform detected the presence of this extension and associated exfiltration activity across nine different enterprises in the U.S., Asia, and the Middle East.
In one case, we observed the exfiltration of a Microsoft login that contained the user’s enterprise email. Though this is not inherently malicious (such as the exfiltration of Microsoft credentials would be), it could provide a pivot point for a threat actor looking for a list of enterprise accounts to brute force or spear-phish.
The company’s internal sharepoint was also sent as a URI, potentially allowing threat actors to collect extensive data related to the target’s search history, internal folders that are being exfiltrated out, and any related accounts. Essentially, it gives an attacker all the information they would need to easily and successfully target the user with realistic spear-phishing attacks, such as thread hijacking attacks.
Legacy Plaintext Protocols
It’s very common to see the use of plaintext protocols, and in many cases, the use of plaintext (i.e. unencrypted text) doesn’t pose a huge security risk. In some uses, it’s even preferred. There are many plaintext protocols that are updated with subsequent versions that add encryption over the top. However, there are still some applications using more insecure legacy network protocols that open the door for any systems in a public network to remotely access a user’s exposed credentials. For this reason, these types of protocols are often targeted in cyber attacks – it’s pretty common practice for cyber criminals and APTs alike to use a tool such as Mimikatz to target resources that are stored in plaintext.
In the case of the Black Hat EU NOC, we detected a number of plaintext protocols in use. Some of these were used by tools and resources for classes, which didn’t pose as much of a security risk in the framework of the conference. However, it should be noted that passing credentials in the clear – in this case, Splunk and API credentials – should be discouraged and do pose a larger security risk outside the context of the conference.
On the other hand, there were some instances where the use of plaintext protocols during the conference were significant causes for concern. For example, we observed plaintext authentication into an FTP database containing sensitive customer/business-related data. This type of practice can be common when using default settings for a service, but it can also give an attacker additional information they could use to gain access. Even if the data is not deemed sensitive, using the encrypted versions of these common protocols is recommended.
The most severe case of exposed plaintext we observed during the conference was a BigFix patch management app that was leaking sensitive host information, including all interfaces, running services, installed apps and versions, and user accounts on the machine. As the BigFix anti-virus software should be configured to communicate with servers using TLS, we determined this exposure was due to a misconfiguration on the software. It’s possible this type of misconfiguration could enable follow-on compromises, as the information returned is essentially everything an attacker would want to know to target a particular system.
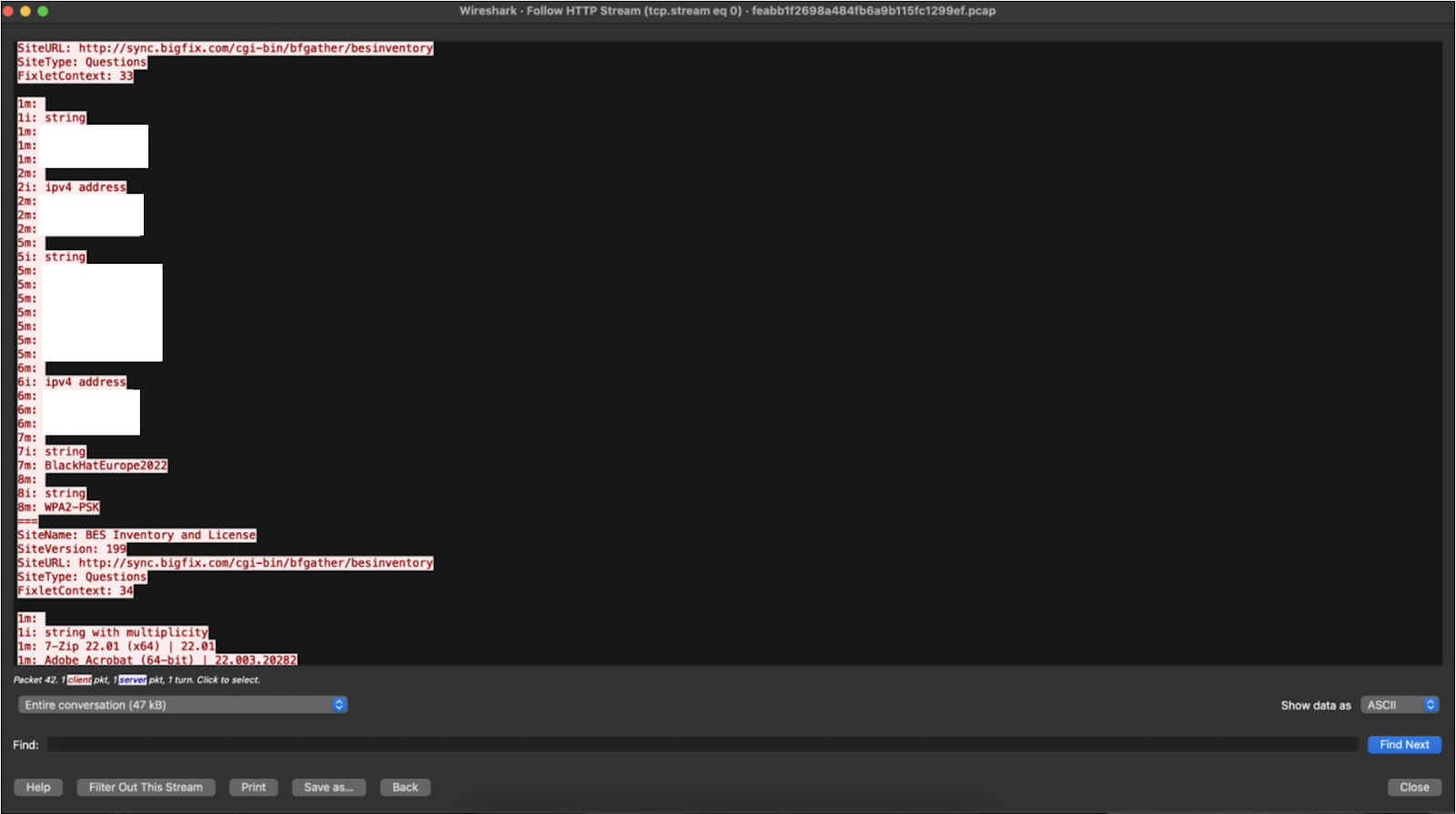 IronNet PCAP of BigFix misconfiguration (1)
IronNet PCAP of BigFix misconfiguration (1)
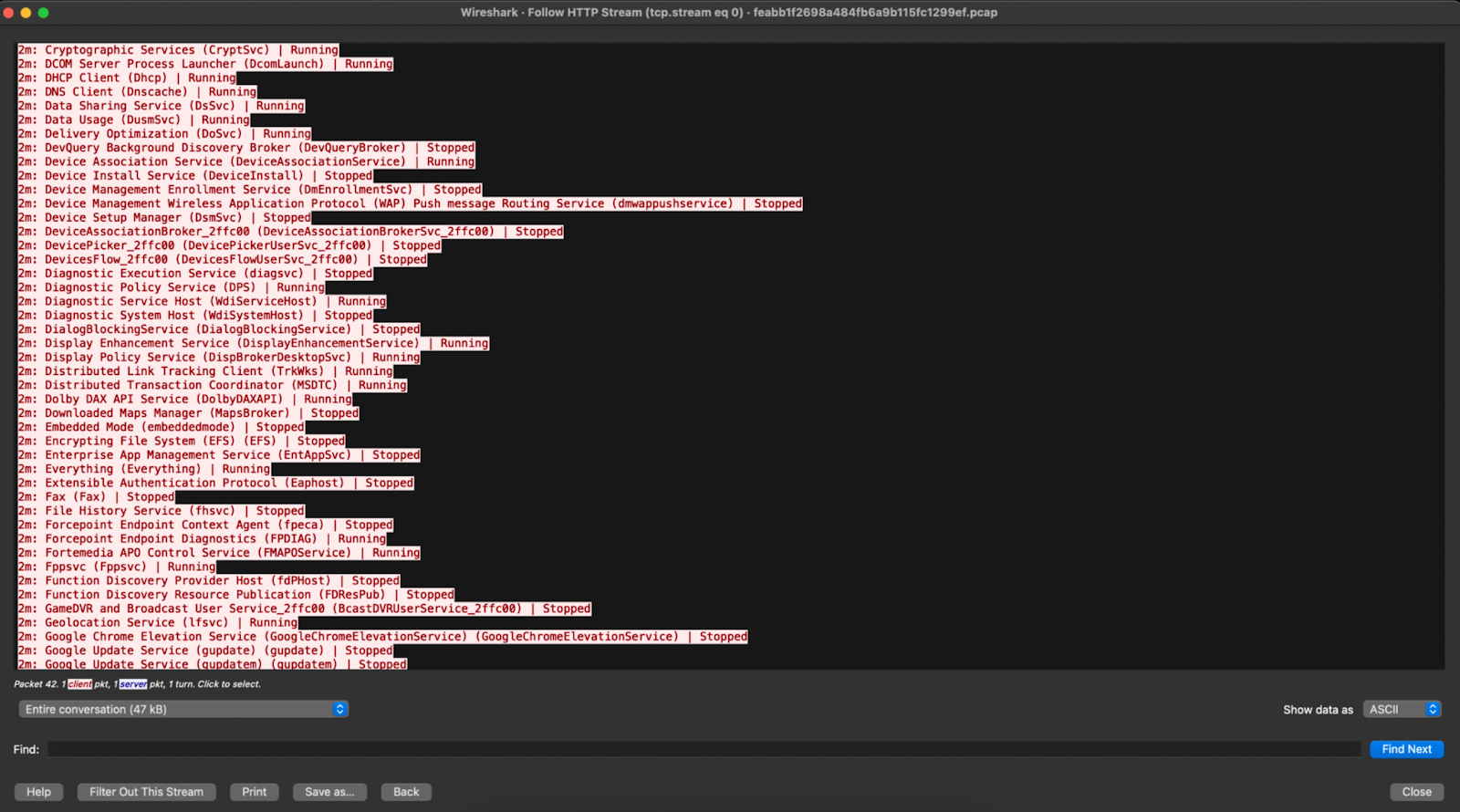 IronNet PCAP of BigFix misconfiguration (2)
IronNet PCAP of BigFix misconfiguration (2)
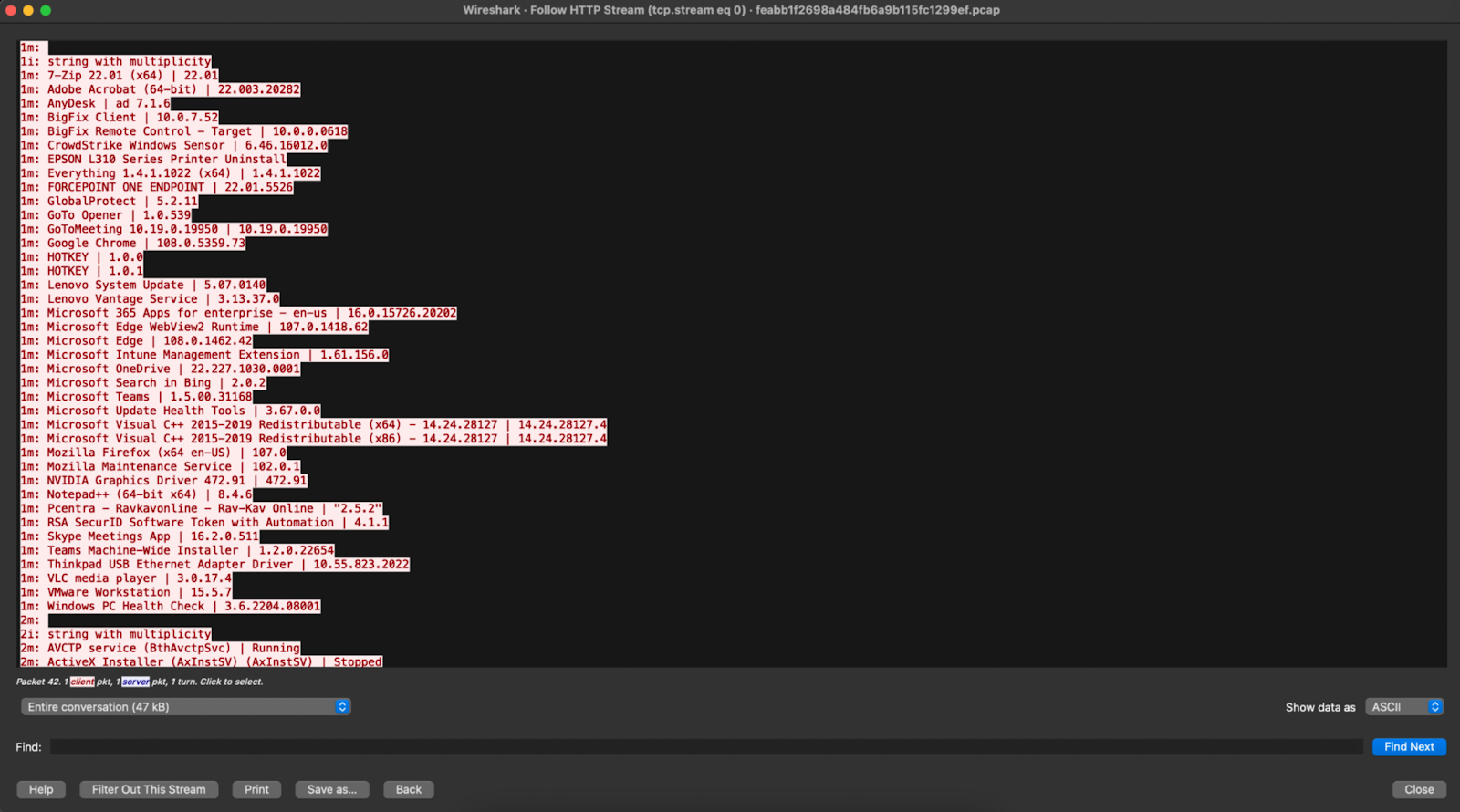 IronNet PCAP of BigFix misconfiguration (3)
IronNet PCAP of BigFix misconfiguration (3)
The role IronNet plays in the Black Hat NOC
Black Hat partners with a handful of select organizations to defend the NOC during its three annual conferences in Asia, the U.S., and Europe. Each partner serves a different function and provides services that work together to establish a stable and well-protected network during the conferences.
IronNet has been a NOC partner for two years, and in addition to providing detection and threat hunting capabilities, IronNet fills the vital role of providing network visibility for troubleshooting and hygiene.
Having comprehensive network visibility – especially in a complex non-enterprise network such as Black Hat’s – is critical. While logs may be present for some activity, it’s more efficient and beneficial to go directly to network traffic and confirm a suspicion, since logs often do not provide the full story.
For example, in one instance, firewall logs detected traffic coming from an IP address associated with the conference’s core routing infrastructure to external destinations in locations such as Colombia and Russia. Since the core infrastructure should not be communicating with external destinations such as this, it raised concerns; however, the firewall logs provided insufficient information to determine the maliciousness of the outbound communications.
In this case, IronNet was able to step in and dive into the traffic to determine the true source of where the traffic was coming from. Through the network visibility provided by IronNet’s Network Detection and Response (NDR) platform IronDefense, we were able to discover the activity occurring was in fact not outbound communications, but instead ICMP ‘Host Not Found’ error messages. However, since the traffic triggering the activity was coming from a classroom performing IP spoofing demonstrations, it appeared in the logs as if it was responding to a source IP in Colombia or Russia, when it was really just a spoofed IP.
Conclusion
As we noted earlier this year in our blog about defending the NOC at Black Hat USA, there are many characteristics that make Black Hat’s networks a unique experience to defend. There’s real malware and malicious activities coming from people bringing already-infected devices onto the network; people with poor security practices such as using plaintext credentials on a public network; and then, on top of that, there’s all the simulated exploits going on in classrooms and demos that our product is detecting but are actually benign.
We enjoy the opportunity to defend and hunt in this unique environment, and we look forward to defending the NOC at Black Hat Asia in 2023.
Recommendations
- Closely review all browser extension permissions, especially those related to tracking information and data sharing, and ensure your extensions are installed only through trusted sources.
- Enterprises should create and enforce browser extension policies that reject extensions with permissions that do not match the functionality of the app.
- Ensure comprehensive network visibility through IronNet’s network detection and response (NDR) platform IronDefense in order to effectively monitor and detect suspicious or malicious browser activity.
- Configure servers to use encrypted channels for communication, which may include SSL or other secure protocols.
Indicators of Compromise (IOCs)
| Network IOCs | Description |
35.198.166[.]27 |
Arechclient2 C2 |
usage.fdown[.]net/pb |
FBDown Chrome Extension domain (C2) |
.png)
