
BACKGROUND:
- On-Premise Microsoft Exchange has been identified as being actively exploited in a series of attacks by using a collection of zero-day vulnerabilities.
- The supposed motive of this APT group attack aligns to the typical strategy of Chinese cyber attacks: intellectual property theft.
- The four vulnerabilities affect unpatched on-premise Microsoft Exchange servers from version 2013 to 2019, excluding only Exchange Online (Office365).
KEY TAKEAWAYS:
- After this initial attack, the attacker bypassed authentication and is able to steal the full contents of multiple user mailboxes.
- As a next step, the attackers performed a wide range of post-exploitation activities in order to export mailbox data through the use of Exchange PowerShell snap-ins.
- It is critical that defenders assume that any of their internally managed assets can be compromised at any time and, in turn, look for host- and network-based indicators of post-exploitation activity using behavioral analytics.
- Behavioral analytics can detect this kind of “talk and move” behavior on the network; NDR tools are designed to spot these behaviors on the network and triage quickly before the adversary succeeds at their end-game: data exfiltration or system control.
- In a Microsoft Exchange vs. SolarWinds comparison, it is worth emphasizing that although the means to which Russia gained access to victim networks via the SolarWinds supply chain attack and the way China gained access to their victims via the Microsoft Exchange zero-days are different, this does not mean that one hack is automatically more impactful or important than the other.
- The two widespread attacks pose the same challenges and highlight the ability of foreign cyber attackers to conduct mass exploitation of U.S. systems.
- If the adversaries are working together, creating a vast threat landscape, why aren't we all working together to defend against them through Collective Defense?
The Microsoft Exchange attack strategy: exploit server vulnerabilities
Based on IronNet threat research and analysis of reported threat intelligence, we know that the threat actors, attributed to the Chinese APT HAFNIUM, have exploited vulnerabilities as part of an attack chain in which they bypass authentication to secure access to an Exchange server. From there, the adversaries create a web shell to take control of the system and execute remote commands. In this process, threat actors secure access to an Exchange Server either by using stolen credentials or by exploiting CVE-2021-26855, a Server Side Request Forgery (SSRF) vulnerability, in which a remote attacker can send arbitrary HTTP requests to the Exchange Server and authenticate to it.
After this initial attack, the attacker bypassed authentication and is able to steal the full contents of multiple user mailboxes. As part of the attack chain, the threat actor exploits the other vulnerabilities, including CVE-2021-26857, to run code as SYSTEM on the Exchange Server and post-authentication arbitrary file write vulnerabilities (CVE-2021-26858 and CVE-2021-27065) to deploy web shells to the compromised host in order to control the server remotely. The web shells (ASPX files) allow threat actors to steal data and conduct further operations on the compromised system.
The attack cycle doesn’t stop there. As a next step, the attackers perform a wide range of post-exploitation activities, such as dumping LSASS process memory using Procdump, using 7-Zip to compress stolen data into ZIP files for exfiltration, exporting mailbox data through the use of Exchange PowerShell snap-ins, and using PowerCat (downloaded from GitHub) to open a connection to a remote server.
Microsoft Exchange Attack Diagram
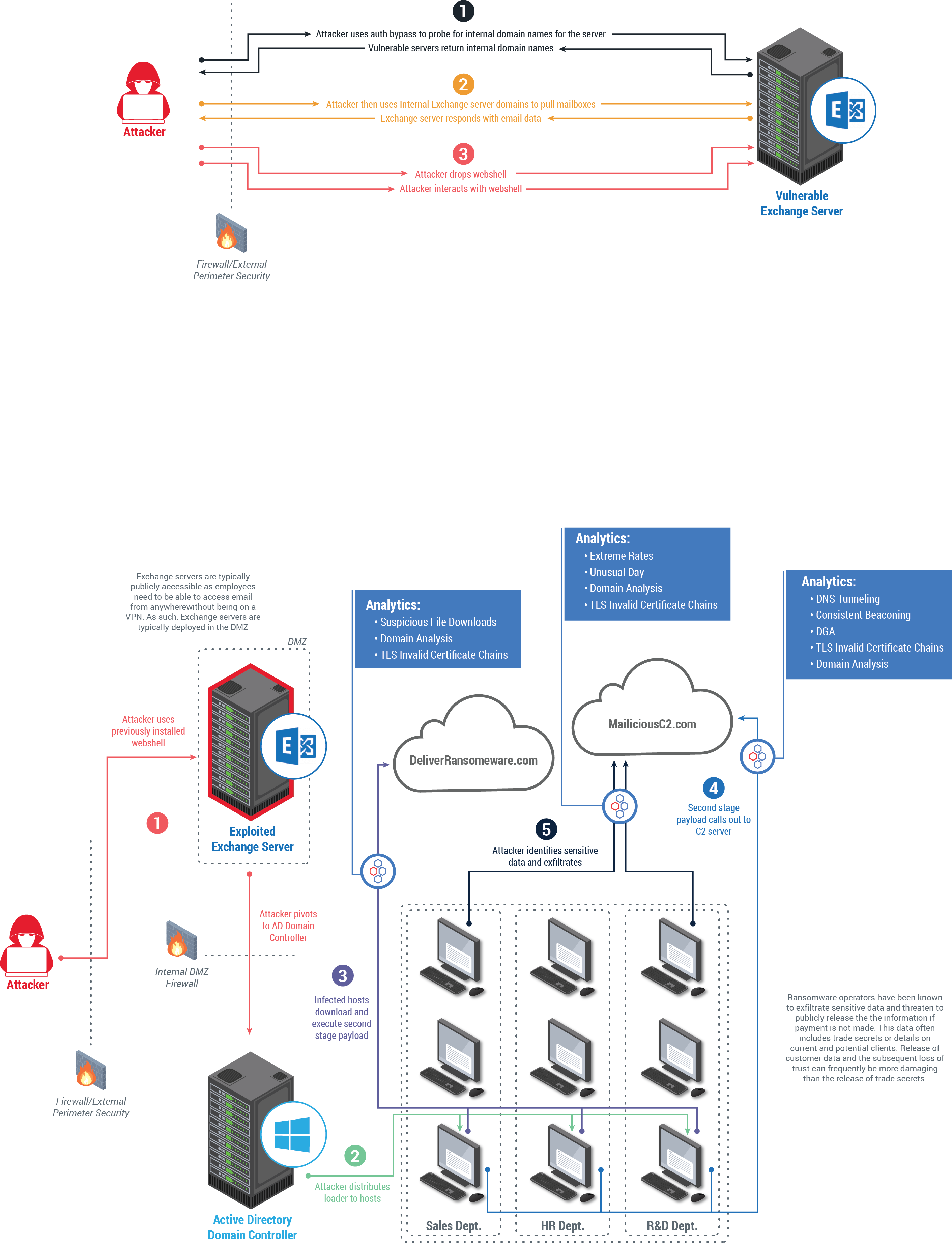
Top image: How Microsoft Exchange vulnerabilities generally work within network traffic. Bottom image: A hypothetical look at how an exploited Microsoft Exchange server can lead to full domain compromise and ransomware.
Who is most vulnerable to these types of Microsoft Exchange server attacks?
When it comes to preventing or detecting the initial authentication bypass exploitation, there does not appear to be much difference between organizations with mature security operations vs. those without. The companies who would be most affected, however, are those that do not deploy a defense-in-depth strategy and assume that their perimeter security is sufficient. It is critical that defenders assume that any of their internally managed assets can be compromised at any time and, in turn, look for host- and network-based indicators of post-exploitation activity using behavioral analytics.
What do we know about the Chinese APT HAFNIUM?
The supposed motive of this APT group attack aligns to the typical strategy of Chinese cyber attacks: intellectual property theft. This Chinese APT, HAFNIUM, has historically targeted U.S. entities with the goal of exfiltrating information from several industry sectors, including law firms, infectious disease researchers, higher education institutions, defense contractors, NGOs, and policy think tanks. While HAFNIUM originates in China, it operates primarily from leased virtual private servers (VPS) in the U.S. to conceal its true location, allowing it to exploit the legal restriction that prohibits intelligence agencies from inspecting systems based in the U.S.
Though HAFNIUM is believed to have been exploiting these flaws since January 6th, 2021, Microsoft publicly acknowledged the vulnerabilities on March 2nd and released several security updates to address the vulnerabilities, recommending that administrators install the patches immediately. Since the vulnerabilities of the unpatched systems became well-known, numerous threat actors beyond HAFNIUM have also been conducting attacks, with at least 10 distinct APTs that have been identified as exploiting the critical flaws in Microsoft’s email software.
Q&A with IronNet Analysts and Analytics Experts
Q: How could this attack have been detected?
A: Zero-Day vulnerabilities for internet-facing web-servers are incredibly difficult to detect based on the nature of the server’s role and its normal functionality. The key, instead, is to prevent such actions from even occurring through the proper implementation of a Web Application Firewall.
Given that the nature of a zero-day attack, however, is inherently unknown and sometimes attackers can bypass security controls and gain access into the environment completely undetected, it is critical to have defense-in-depth security controls. This includes a network detection and response (NDR) platform to help identify follow-on actions as the APT tries to dwell in the network to stake out next steps along the intrusion cycle toward data exfiltration or system control. Behavioral analytics can detect this kind of “talk and move” behavior on the network; NDR tools are designed to spot these behaviors on the network and triage quickly before the adversary succeeds at their end-game: data exfiltration or system control.
Q: What are some actions that these adversaries might take once inside the network, if firewalls were breached?
A: It has been reported that the original threat actor, HAFNIUM, was after email communications — a fairly standard objective upon achieving access like this. Beyond that, although it has not been reported yet, we can only assume that, given the time, the threat actor would leverage this access to get themselves further into a target network, potentially resulting in scanning, lateral movement, C2, and possibly exfiltration activity, all of which IronNet can detect with its behavioral analytics.
What complicates the issue is that once the vulnerabilities were publicly reported, a number of different actors began exploiting these vulnerabilities, thereby making it very difficult for defenders to determine who was actually behind their breach. Motivations between actors can vary greatly and range from financially motivated groups dropping ransomware or crypto miners — all the way to nation-states looking to quietly gather intelligence. At this time, it is not even clear who all is involved, much less what their end motivations may be.
Going forward, it is likely (as folks are moving to the cloud so now we're seeing more and more hybrid environments) that the adversary is going to immediately attempt to pivot to things like Azure AD/O365 and implement AD persistence in order to live in the environment and read inboxes via powershell snap-ins. Basically, they will try to blend into the environment immediately so that all traffic and logs look like benign behavior. For this reason in particular, a compelling argument is that small to medium-sized businesses should be moving to the cloud to ensure that services as sensitive as email are protected by professionals who understand and are familiar with the technologies at play.
Q: How could this attack have been detected more quickly?
A: Detection of these attacks can be further accelerated if organizations are working together in a Collective Defense operational model that allows them to share threat data on these anomalies in real-time. On top of that, the Collective Defense model effectively increases the signal-to-noise ratio of events across enterprises targeted as a group by threat actors, and it is particularly effective against previously unknown and novel attack vectors.
Q: Does the fact that this is one of the first mainstage circumstances where the vulnerability existed solely with the on-premise solution mean that cloud environments are more secure?
A: The security community has been relatively split on the risk of migrating to the cloud vs sticking with metal. In this case, those that likely have not fully adopted 0365 or are still in the process of migrating to the cloud, as well as may have not had properly configured Web Application firewalls, are typically the ones hit. This is not necessarily a direct argument for on-prem solutions being less secure; instead, this highlights how the decision to move to the cloud needs to be a balance. The conversation that organizations need to have is “What we do feel confident in running/maintaining/securing and what do we not? Maybe we are solid on our webserver, but we don't have the time/money/expertise to feel 100% on an email server.” Those conversations will help inform business decisions on what should be in the cloud. Also, it is important to note that managed services in the cloud are different from running your own services on a privately managed cloud virtual private server.
Q: I have always invested in my perimeter security, so how can IronNet help me?
A: Supply chain attacks such as SolarWinds/SUNBURST aren’t the only vector that will compromise your perimeter security; zero day exploits will, too. As former offensive cyber operators, we are confident an adversary can breach your perimeter security and get into your network. Whether through phishing, exploiting unpatched vulnerabilities, or installing signed software updates from a trusted partner (such as as SolarWinds), the enemy can get in. No firewall, anti-phishing tool, threat intelligence service, or endpoint agent can stop the initial breach from an unknown threat (as proven in the Microsoft Exchange Server attack). Once that happens, the goal is to find it as quickly as possible. IronDefense was designed to do exactly that. That's why we focus our analytics on identifying early-stage Command and Control. That's why we were successful in identifying SolarWinds behavior last May. You can't prevent the breach, but you can find it quickly with IronDefense.
Breaches are unclear at this time. We have customers who run on-premise Exchange servers and we should assume they have been breached. We are supporting them through TIRs, TDQs, and manual hunts. Although IronNet’s products weren’t designed to address the authentication bypass activity, we remain acutely focused on the likely second stage activity that exhibits behaviors that we are expertly positioned to detect like scanning, lateral movement and C2 activity with the following analytics: External IP Scanning, External Port Scanning, Internal IP Scanning, Internal Port Scanning, Lateral Movement Chains, PII Data Loss, Suspicious File Downloads, Consistent Beaconing HTTP, Consistent Beaconing TLS, DNS Tunneling, Domain Analysis HTTP, Domain Analysis TLS, Domain Generation Algorithm, Encrypted Comms, Periodic Beaconing HTTP, Extreme Rates, Extreme Rates TLS, Unusual Day, TLS Invalid Cert Chain, Threat Intelligence Rules and Knowledge-Based Rules.
Due to the fact that the attacker used known webshells, IronNet has deployed additional suricata signatures that will aid in the detection of the China Chopper, C99, R57, B374k and WSO webshells, known to have been used by Chinese state actors.
How does this Microsoft Exchange attack compare to SolarWinds?
Though the victims and methods used in the SolarWinds attack and the Microsoft Exchange attack are notably different, the two pose the same challenges and highlight the ability of foreign cyber attackers to conduct mass exploitation of U.S. systems.
So far, it is believed that the Microsoft Exchange hack has impacted more targets than the SolarWinds hack. This could be due to a difference in both the approaches used and the ultimate goals of the attacks:
- In the SolarWinds attack, a Russian APT compromised the supply chain of software vendor SolarWinds by injecting a backdoor into an IT monitoring platform software update, which was then downloaded by thousands of SolarWinds customers. The attackers then cherry-picked high-value targets it wanted to exploit and deployed additional malware to compromise those networks and exfiltrate information. A White House press briefing revealed that despite more than 18,000 organizations being exposed to the SUNBURST backdoor, only nine government agencies and around 100 U.S. companies actually experienced post-intrusion activity.
- In the Microsoft Exchange attack, the threat actors secured access to Exchange servers either through stolen credentials or through the vulnerabilities that allow them to bypass authentication. Once they connected to the servers, they then deployed a web shell to control the system and execute commands remotely. Information about the Microsoft Exchange hack is still emerging, with the number of potential victims across the globe growing daily. Initially only targeting a small number of victims, HAFNIUM changed tactics around the time Microsoft publicized the attack, beginning to use automated software to scour the internet for vulnerable servers to infect. Initial estimates gauged the number of affected systems at around 30,000, but the true breadth of the breach and the identities of the victims are still being revealed. While many of the victims caught up in the hack likely hold little intelligence value, such as small businesses, school districts, and city governments, it is probable that high-value espionage targets are included as well, such as military contractors and the European Banking Authority, whose email servers were reported on March 7th to be compromised in the attack. The Norwegian Parliament was reported on March 10th to have been to have compromised in the attack.
Certainly a key difference to note here is their initial access vectors:
- Russia’s ability to generate its own zero-day by infiltrating the inherent trust of the code base is highly sophisticated and would take years of planning.
- Yet, China’s ability to discover a zero-day in an already internet-facing product is also distinctly advanced. Russia’s vulnerability window (from exploitation to victim detection) may have been greater by a few months, but China was able to accomplish a similar end result in a shorter time frame.
Although the means to which Russia gained access to victim networks via the SolarWinds supply chain attack and the way China gained access to their victims via the Microsoft Exchange zero-days are different, this does not mean that one hack is automatically more impactful or important than the other.
Where the SolarWinds attack highlights the inherent trust that administrators put in software updates and the risks associated, the Exchange vulnerabilities prove that it isn’t just a supply chain attack that enables such widespread and sensitive access. The ability of nation-states to gain access to a trusted platform that government entities and companies alike use to exchange information should be worrisome, regardless of how they gain access to it. Because of the treasure-trove of information on Exchange, and its unique relationship with Active Directory, defenders need to operate under the assumption that these assets are compromised and put in place network detection and response platforms.
What are the motivations behind these two nation-state actors?
- Russia is looking to gain geopolitical insight and to perform influence operations, which we’ve been seeing heavily now since 2016. Russia wants to create doubt, manipulate information, and create distrust amongst allies in order to further their National Interest. The Solarwinds attack highlighted this — their ability to orchestrate a supply-chain attack is no small feat, and furthermore, could only be pulled off by a handful of Nation States. So if we look at the victims of that attack, it’s clear that Russia was very much interested in gaining access to any high-profile U.S. government systems. Any defense contractor or U.S. company that may supply some service or product (like Microsoft) to the U.S. government, would’ve just been the “cherry on top.”
- Vladimir Putin is ex-KGB, so this is like having the head of the CIA become the dictator of your country. All foreign policy / operations are being viewed through the lens of someone who has spent most of their career in intelligence operations — and understands the vast benefits of this when paired with cyberspace.
- Though equally as interested as Russia in beating the U.S., China attempts to do so through a different approach. Instead of executing influence operations, it is looking to beat the U.S. economically. China is looking to compete for global information technology (IT) market share, contend with U.S. defense contractors, and continue to solidify its aspirations with the belt and road initiative and its expansion in the South China Sea. Stealing intellectual property and then using it to prop up their own economic and defense interests is their main goal, and cybersecurity is the exact tool for the job.
- This is why we see more “smash and grab” style tactics when it comes to China vs. Russia. China doesn’t necessarily care about being caught; as long as they can get the intellectual property and get out in a timely manner, it’s worth it because they’ve saved billions of R&D money and time. Whereas with Russia, part of executing a successful influence operation is to operate in the shadows, which inherently means more sophisticated cyberspace operations.
One commonality? Seemingly, one of the main goals in both these attacks was around O365 and Exchange servers. We saw Russia pivot to O365 once access was gained, and we can speculate that China performed months of research to discover these Exchange zero-days. Thus, they were able to gain a foothold in a place where U.S. government entities and companies alike conduct their most intimate conversations with external partners and have sensitive internal communications.
We will update this post as the news and insights unfold.
.png)
