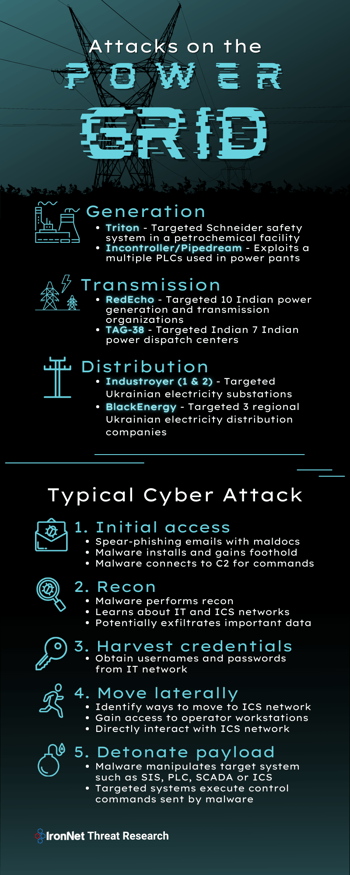
Given the recent news of Industroyer2 targeting Ukrainian electrical substations in April 2022 and the increased threat of cyber attacks on energy infrastructure, IronNet Threat Research took an interest in breaking down and analyzing past malware and threat actors that have targeted the various stages of the energy supply chain, specifically: generation, transmission, and distribution.
Generation
Triton
First detected in June 2017 in an attack against a Middle East-based petrochemical facility, Triton [PDF] is a destructive malware specifically designed to manipulate industrial safety systems.
Triton has been linked by the U.S. government to the Russian Central Scientific Research Institute of Chemistry and Mechanics (TsNIIKhM), a research institute that supports Russian armed forces. It operates by modifying in-memory firmware in safety controllers, allowing the attacker to read/modify memory contents and execute arbitrary code. Through this, the threat actors can gain complete remote control of the safety controllers and cause them to cease operating or to operate in an unsafe manner.
In the attacks against the Middle East-based petrochemical facility, Triton was prevented from reaching its full capabilities because software bugs in the malware caused the industrial control system (ICS) safety controllers to detect the anomaly and the facility to automatically enter a safe state.
Triton is still very much a threat, however, and could have potentially led to consequences such as facility damage, system downtime, and even loss of life. In March 2022, the FBI released a report [PDF] warning of Triton’s continued threat to global critical infrastructure ICS systems. Safety controllers are used in a large number of environments, and they will continue to be the target of destructive malware.
INCONTROLLER / PIPEDREAM
In a rare case of researchers being able to analyze malware before it being used against victim infrastructure, Incontroller (aka PipeDream) was first discovered in early 2022 and has not yet been seen deployed in the wild against a target. However, that may make it even more likely to be leveraged or replicated in future attacks.
Incontroller is a collection of utilities that includes tools for reconnaissance, manipulation, and disruption of programmable logic controllers (PLCs). It is the seventh known ICS-specific malware and the fifth specifically developed to disrupt industrial processes.
Believed by researchers to be a state-sponsored malware (though not attributed to any particular state), Incontroller has the capability to: disrupt controllers to shut down operations, modify controllers to disrupt or sabotage industrial processes, or disable safety controllers to cause physical destruction. Due to its versatility, Incontroller may be used to target and attack PLCs and industrial software from hundreds of additional vendors in multiple verticals, including equipment in liquefied natural gas (LNG) and electric power environments.
Transmission
RedEcho
In February 2021, researchers reported that since mid-2020, Chinese advanced persistent threat (APT) RedEcho had compromised at least 10 Indian power sector organizations, including four Regional Load Despatch Centers (RLDC) responsible for operation of the power grid through balancing electricity supply and demand.
The researchers assessed that these intrusions offer little value in terms of economic espionage value, but pose major concerns over potential pre-positioning of network access to support Chinese strategic objectives. Making heavy use of an infrastructure known as AXIOMATICASYMPTOTE, which encompasses ShadowPad command-and-control servers (C2s), the threat actors are believed to be tied to the Chinese government. Notably, this campaign commenced shortly after border clashes occurred between Indian and Chinese forces at the the Ladakh border, resulting in the first combat deaths between the two sides in 45 years.
It should be noted that in this campaign, the threat actors did not succeed in compromising the OT/ICS network; however, they may have gained the necessary information to do so in the future.
TAG-38
In April 2022, researchers released a report [PDF] on a Chinese state-sponsored campaign that since September 2021 has targeted at least seven Indian State Load Despatch Centers (SLDCs) responsible for carrying out real-time electric grid operations in North India.
There are several consistencies in these intrusions and the previous RedEcho activity identified in February 2021, and one of the SLDCs targeted in these recent attacks was also targeted in previous RedEcho activity. However, there are also some notable distinctions that have led the researchers to not officially link the activity to RedEcho and instead cluster the latest intrusions under the temporary name TAG-38.
In the attacks, the TAG-38 threat actors compromised and co-opted internet-facing, third-party DVR/IP camera devices as C2s for Shadowpad malware infections. The threat actors did not succeed in compromising the OT/ICS network, but the goal behind the intrusions was likely to enable information gathering surrounding critical infrastructure systems or pre-positioning network access for future activity.
Distribution
BlackEnergy
In December 2015, variants of BlackEnergy and KillDisk malware took offline dozens of substations across three regional electricity distribution companies in Ukraine, causing roughly 225,000 civilians to lose power for several hours.
Researchers have attributed the attacks to the Russian state-sponsored Sandworm team, who gained initial access to the electricity companies’ IT networks roughly six months prior to the outage, using spear-phishing emails to deliver BlackEnergy3. Once gaining a foothold in the IT network, the threat actors harvested credentials and used existing remote administration tools on the operator workstations to deliver themselves into the environment for direct interaction with the ICS component. They then hijacked the SCADA systems to open the breakers and installed a modified KillDisk payload across the environment to erase the master boot record and some logs of impacted organization systems.
Notably, the Sandworm actors demonstrated the capability and willingness to target field devices at substations, write custom malicious firmware, and render critical devices inoperable and unrecoverable, causing arguably the largest power outage caused by a cyber attack ever recorded.
Industroyer
In December 2016, Industroyer malware targeted a Ukrainian electricity substation responsible for power flows, instigating a roughly hour-long power outage to at least one-fifth of Kyiv, Ukraine. Industroyer can be used to attack any ICS system and was referred to at the time as the biggest threat to ICS systems since Stuxnet.
Delivered through a spear-phishing email opened by an employee at a SCADA control workstation, Industroyer was able to run in the background for roughly six months before interacting with control system networks. The malware has the capability to directly control switches and circuit breakers at power grid substations using four ICS protocols. In this attack, it sent SCADA/ICS commands to devices in the field, which executed what it thought were valid and authorized control commands to cause a power outage event.
After the cyber attacks impacting Kyiv, many were concerned Industroyer may be repurposed to attack other ICS infrastructures, such as local water or gas utilities, manufacturing systems, or oil and gas distribution. These concerns were later fulfilled six years later in 2022.
Industroyer2
In April 2022 – less than two months after Russia invaded Ukraine – a second variant of Industroyer (Industroyer2) was discovered targeting regional high-voltage electrical substations in Ukraine. Luckily, the attack was detected and mitigated before a black-out occurred; however, the potential outages would have impacted an estimated two million people in the country.
Attributing the attack to the Sandworm team, researchers believe the threat actors initially gained access in early February 2022; however, it is currently still under investigation which tactics the attackers used to gain access and move laterally from the IT network to the ICS network.
The Sandworm threat actors used several malware variants in the attack. Along with Industroyer2, they deployed three wiper variants (CaddyWiper, AwfulShred, SoloShred) targeting different operating systems, and a worm (OrcShred) to spread the two different wiper malware targeting Linux and Solaris systems. CaddyWiper, which is a wiper first seen a month prior targeting a Ukrainian organization, was observed deployed via Group Policy Object (GPO), indicating the attackers had prior control of the target’s network beforehand and possibly even achieved full domain compromise. Researchers believe the use of wipers was likely an effort to slow down the recovery process and prevent operators of the energy company from regaining control of the ICS consoles.
Typical Cyber Attack Chain
From examining past attacks on electric infrastructure, IronNet threat analysts generated an attack chain that is typical of attacks targeting an electric utility. Each step in the attack chain is mapped to the associated MITRE ATT&CK tactic or technique and, where appropriate, the relevant IronNet behavioral analytic.
Initial access
- Spear-phishing emails with maldocs
- MITRE ATT&CK: Initial Access - Phishing (T1566)
- IronNet Analytic: Phishing HTTPS
- Analyzes encrypted communications and destination server information to detect when a user visits a domain that may be associated with phishing activity.
- Install malware and gain foothold
- MITRE ATT&CK: Initial Access - Phishing (T1566)
- IronNet Analytic: Suspicious File Download
- Analyzes file downloads to determine if it differs from historical norms of the network and to identify potentially malicious files.
- Specifically designed to target file downloads typically observed in phishing campaigns and malware gathering additional file resources from the internet.
- Connect to C2 and ask for commands
- MITRE ATT&CK: Command and Control - Application Layer Protocol (T1071)
- IronNet Analytic: Consistent and Periodic Beaconing HTTP/TLS
- Identifies periodic, outbound communications that are indicative of repetitive attempts by malware to establish communications to attacker-controlled C2 servers.
Recon
- Learn about IT and ICS networks
- MITRE ATT&CK: Reconnaissance - Active Scanning (T1595)
- IronNet Analytic: Internal Port Scanning
- Identifies when network ports are being scanned, which is commonly seen in recon activity by threat actors looking for ways to move laterally and spread throughout energy company networks, and pinpoints the device that is the source of the scanning.
- Potentially exfiltrate important data
- MITRE ATT&CK: Exfiltration Over C2 Channel (T1041)
- IronNet Analytic: Unusual Day
- Detects when an outbound network data transfer is significantly higher than historical norms for a specific user or device, which may indicate a threat actor attempting to take advantage of off-hours time to transmit sensitive data outside the enterprise network.
Harvest credentials
- Obtain username and passwords from IT network
- MITRE ATT&CK: Credential Access (TA0006)
- IronNet Analytic: High Failed Logins
- Identifies high rates of failed logins per user from a workstation and keeps track of the reason for failure in order to detect brute force attacks and potential recon of domain users.
- IronNet Analytic: Suspicious Successful Logins
- Identifies suspicious successful logins from a single workstation by accounting for anomalous host, account types, and login processes, which could indicate an attacker has compromised user credentials and/or gained access to the network.
Move laterally
- Identify ways to move to ICS network
- MITRE ATT&CK: Discovery - Network Service Discovery (T1046)
- IronNet Analytic: Error Codes
- Detects users within specific accounts and roles that have an anomalously high rate of access/authorization error codes, which could suggest an attacker has accessed the network and is attempting to pivot to privileged or sensitive information or systems.
- IronNet Analytic: Role Enumeration
- Detects anomalous high rates of distinct role calls within a specified time period to identify threat actors that may be trying to assume many different roles in quick order to try to escalate their privileges or move laterally through the network.
- Gain access to operator workstations
- MITRE ATT&CK: Lateral Movement - Remote Services (T1021)
- IronNet Analytic: Lateral Movement Chains
- Identifies anomalous traffic chains that occur over common remote access protocols that indicate attempts by an intruder or malware to move throughout a network towards more valuable assets.
- Directly interact with ICS network
- ICS MITRE ATT&CK: Command and Control (TA0101)
Detonate payload
- Manipulate target system such as SIS, PLC, SCADA, or ICS
- Execute control commands sent by malware
.png)