Once upon a time, the rules were simple.
Strategic cyber operations were led by government hackers hidden away in giant, windowless buildings. When organized cybercrime groups came onto the scene, they mainly focused on profitable targets like corporations and tried to avoid public targets that would attract too much attention, such as critical infrastructure and governmental systems.
However, the Ukraine-Russia War tossed all these “rules” out the window.
Today anyone, including the stereotypical hacker in a hoodie working out of their parents' basement, can join in on a cyber war. As the Ukraine-Russia War rages on, more and more people from around the world are joining the conflict from the comfort of their own home.
Expectations and surprises
For those familiar with Russia’s previous cyber tactics, many expected the cyber domain to be a major battlefield for the Ukraine-Russia War. Rather, the cyber attacks led by Russia so far in the conflict have been relatively minor.
In the days leading up to and during Russia’s invasion, Ukraine fell victim to the low-level cyber attacks that many had anticipated, like distributed denial-of-service (DDoS) attacks, phishing campaigns, and data wiping malware. If anything, these were the bare minimum of what was expected of Russia.
What has been a surprise, however, are the Russian cyber attacks that haven't happened.
In the run-up to the invasion, many speculated that Russia would combine massive cyber attacks with "boots on the ground" to generate maximum chaos and destruction in Ukraine. Everyone's worst expectations were that Russia would target Ukraine's critical infrastructure, just like the power grid attacks in 2015 and 2016, or unveil an attack using a zero-day exploit that would cripple systems across Ukraine.
We also expected Russia to enlist the help of the cybercriminal groups for cyber operations. Given Moscow’s historical tendency to outsource cyber attacks and its close ties to cybercriminal groups based in the country, it was presumed cybercriminal groups would support Russia in the conflict with ransomware attacks and data breaches.
Yet, none of these expectations of a devastating cyber war on Ukraine have materialized (at least, as far as we can tell). Sure, Ukraine is experiencing the rudimentary cyber attacks we mentioned earlier, like DDoS attacks, phishing campaigns, and malware wipers, but it’s been experiencing attacks like these (and worse) for the past eight years.
Instead, while Russia has been leading a relentless offensive cyber campaign against Ukraine and other Western countries for the past decade, Ukraine has been quietly learning from Russia’s cyber playbook and is turning the tables on Moscow. Now, rather than being the architect of a brutal cyber war, Russia has quickly become the victim of the cyber chaos campaign it pioneered.
Crowdsourcing a cyber army
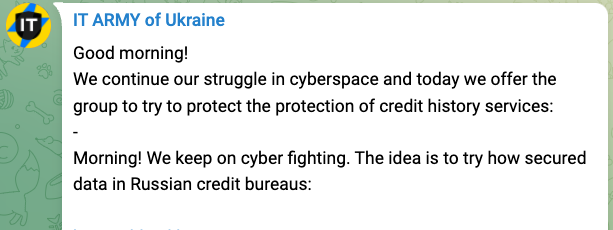
Shortly after Russia invaded, the Ukrainian government organized a volunteer "IT Army," reminiscent of the "patriotic" hackers Russia has used in the past. Using a Telegram channel, the Ukrainian government provides voluntary hackers with a list of targets, such as Russian government and business websites, and instructs them on how to bring sites down using DDoS attacks and even test how secure private data is on a site.
Image from Ukraine's Telegram channel
Beyond the official Ukrainian IT Army, hackers from around the world have joined the fray. Shortly after the war began, the Anonymous collective pledged outright support for Ukraine and declared “cyber war against Russia.” Since that declaration, Anonymous has led a series of cyber attacks against Russian entities that have produced data leaks and hindered Russia's ability to promote propaganda, perform daily functions, and respond to increasing economic sanctions.
Cybercrime support
Ukraine isn't the only one that has received outside cyber support, though. The Conti group, one of the most prolific ransomware groups in the world, publicly stated its support for Russia at the start of the conflict. But shortly after announcing its allegiance, Conti became the victim of a massive data leak that spilled secrets about its infrastructure, communications, organizational structure, and operations to the world.
This leak, which is widely believed to be retribution for Conti’s declared support of Russia, has arguably deterred other cybercriminal groups from publicly supporting Moscow as well. LockBit, which is another notable ransomware group, came out shortly after the leak stating it is apolitical and any attacks it launches are purely for financial gain.

Figure: LockBit statement declaring neutrality.
Cybercriminal groups like Conti and Lockbit run their operations like true businesses, meaning they tend to prioritize profit over actions that may attract government attention and public backlash. For this reason, it’s unlikely we will see any other cybercriminal groups voluntarily become involved in the conflict, especially on behalf of Russia.
Individuals are at the forefront
On the other hand, however, Ukraine’s crowdsourcing of cyber attacks has been very effective in debilitating Russian cyber infrastructure and cohesion. We will likely see more individuals become involved as stories and images of innocent victims continue to tug on the heartstrings of people around the world.
We were expecting state-sponsored APTs and sophisticated cybercriminal groups to be at the forefront of the cyber war. Instead, spontaneous and decentralized networks of hackers from around the world have risen up to take the spotlight.
Cyber attack crowdsourcing is uncharted territory
Cyber attacks have become accessible unlike ever before, meaning cyber war is no longer solely the domain of highly sophisticated government hackers. Technology, whether it be in the form of software tools, social media platforms, or instantaneous messaging, has expanded the Ukraine-Russia war from one that is confined by geographical boundaries to one whose reach is only limited by the internet.
In this conflict, the networks and computers around the world have proven to be just as much a “battlefield” as the cities in Ukraine. Crowdsourcing cyber attacks is not new, but we are now seeing it on a scale unlike ever before and the potential impact of so many different players becoming involved remains to be seen. We are in uncharted territory and how it plays out is anyone's guess.
.png)