Black Hat USA 2021 is officially in the books. With thousands of attendees and vendors coming together for this elite cybersecurity event, Black Hat unfortunately also attracts hackers and cybercriminals determined to prey on vulnerable devices. As we learned firsthand through our work inside this year’s Black Hat Network Operations Center (NOC), my team and I have walked away with a newfound perspective on our responsibilities as cyber hunters and analysts. Amidst a rapidly evolving landscape of cyber threats, knowledge is the greatest power.
Monitoring the conference’s network gave us a unique and rewarding opportunity to equip others with critical knowledge to better secure their own devices and networks. Here are three key insights based on the IronNet team’s experience inside the Black Hat NOC:
1. Crossing the (red)line
IronNet’s network detection and response (NDR) solution IronDefense revealed a total of 1,788 alerts throughout the entire conference.
Among the malicious alerts, our analysts detected a wifi user who downloaded RedLine Malware while attempting to pirate a video production software from a Warez site. Unbeknownst to the user, the malware scraped their hardware for saved cookies, credentials, device information, and more.

To put it bluntly, Redline Malware is no joke. It exposes several facets of critical information to bad actors. It has the potential to inflict serious, irreversible damage upon victims by enumerating their machine info (usernames, hardware, location information, installed software), collecting their browser data (saved credentials, credit card information, autocomplete data), and exfiltrating sensitive information from their crypto wallet. It also is capable of file upload and download, file executive, and other RAT capabilities.
We discovered the threat from an alert on the IronNet platform that identified malware traffic following the infected software’s extraction and execution of the trojan. We subsequently contacted the victim to inform them their host was infected and provided instructions on how to alleviate it.

2. The SMTP ripple effect
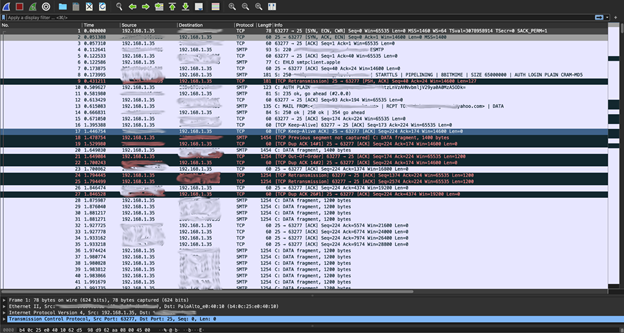
An iPhone connected to Black Hat’s public wifi was seen sending SMTP traffic, which left the email accounts, email correspondence, and Base64 encoded credentials of a security company’s Chief Operating Officer exposed to hackers. An IronNet hunter discovered the threat and notified the individual of the data exposure. Although the alert pertained only to one person, it is likely that others in the company regularly used the same server and, in turn, had their data exposed as well.
Above all, this case exemplified the immense impact one single data breach can have on an entire organization’s internal network or supply chain -- magnifying the importance for individual employees to practice hyper-vigilance to cyber threats in a remote work environment, as IronNet’s IronNet Hunt Operations Lead Melody Sampson explains.
3. A lingering DGA
The third case involved a potentially pre-infected device, meaning malware was already on the host prior to the victim attending the conference. With the number of people who attend BlackHat, this is a fairly common occurrence. The host was performing suspicious DNS queries for Domain Generation Algorithm-like domains -- coming on and off the network rapidly.
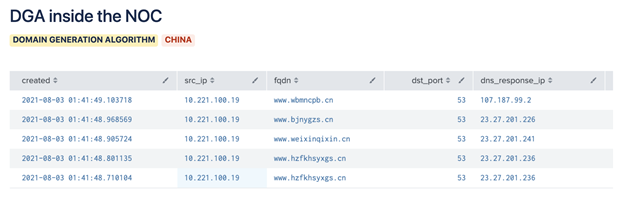
Then, we saw the DGA … again, this time on Black Hat’s public wifi.
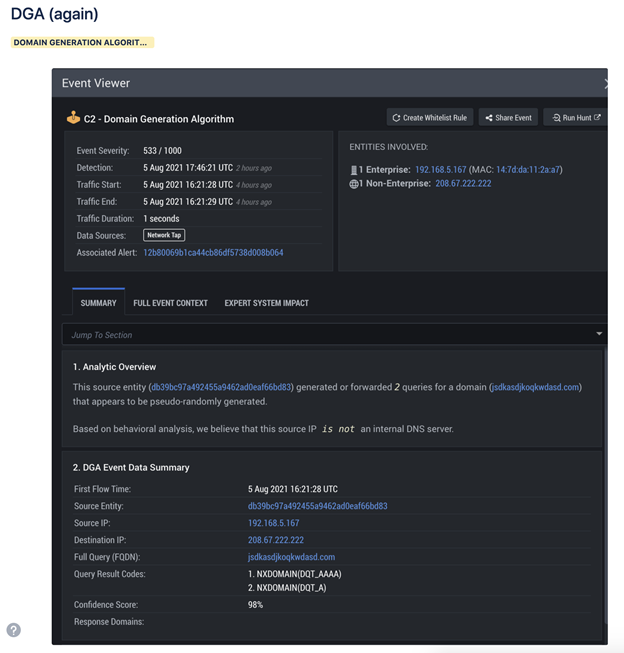
However, we didn’t observe any successful queries that went through and led to C2 traffic. The domains with visible host queries didn’t receive a response, which indicated the host was likely unable to find its C2 rendezvous. Since our analysts were unable to confirm what the scope of the infection was, we decided against a full intervention.
For more highlights of our experience at Black Hat 2021 and what we think about network defense, check us out on Twitter and LinkedIn or visit the IronNet website.

.png)
